One weak password can lead the way to all sorts of evil-doer activities. Cyber criminals don’t only steal your money and sensitive information. They also steal your
8 bad password practices you need to avoid
Bad password practices are getting more and more attention. The year 2019 saw 5,183 data breaches that exposed 7.9 billion records in high-profile cyber attacks. Financial organizations, internet companies and retail businesses have all been affected. This means there is a pretty good chance you’ve been affected too.
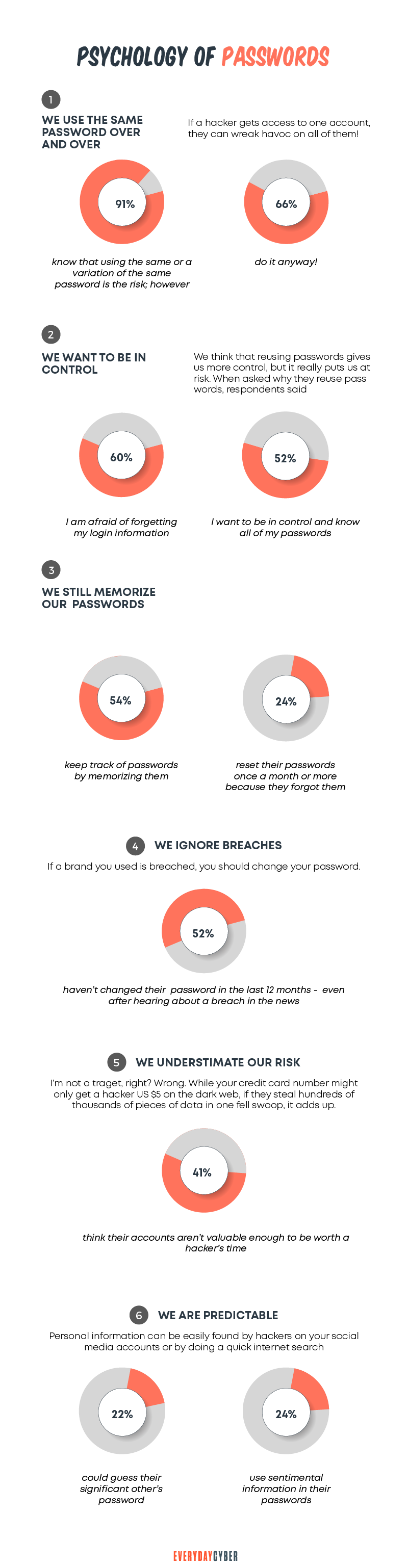
Bad password practices make it much easier for cyber criminals to do evil things. These practices could include:
- Weak passwords
- Reusing passwords
- Using personal information, such as pet name, birth date or street address
- Saving your information in clear text
- Never updating passwords
- Sharing passwords
- Using sequential keyboard paths
- Using the same password for all your online accounts
We all struggle to create secure password combinations. Often, we have so many of them and trying to remember them all is, quite frankly, a pain. Unfortunately, we tend to take the easy path and make short and memorable passwords. And far too frequently, we use the same passwords everywhere.
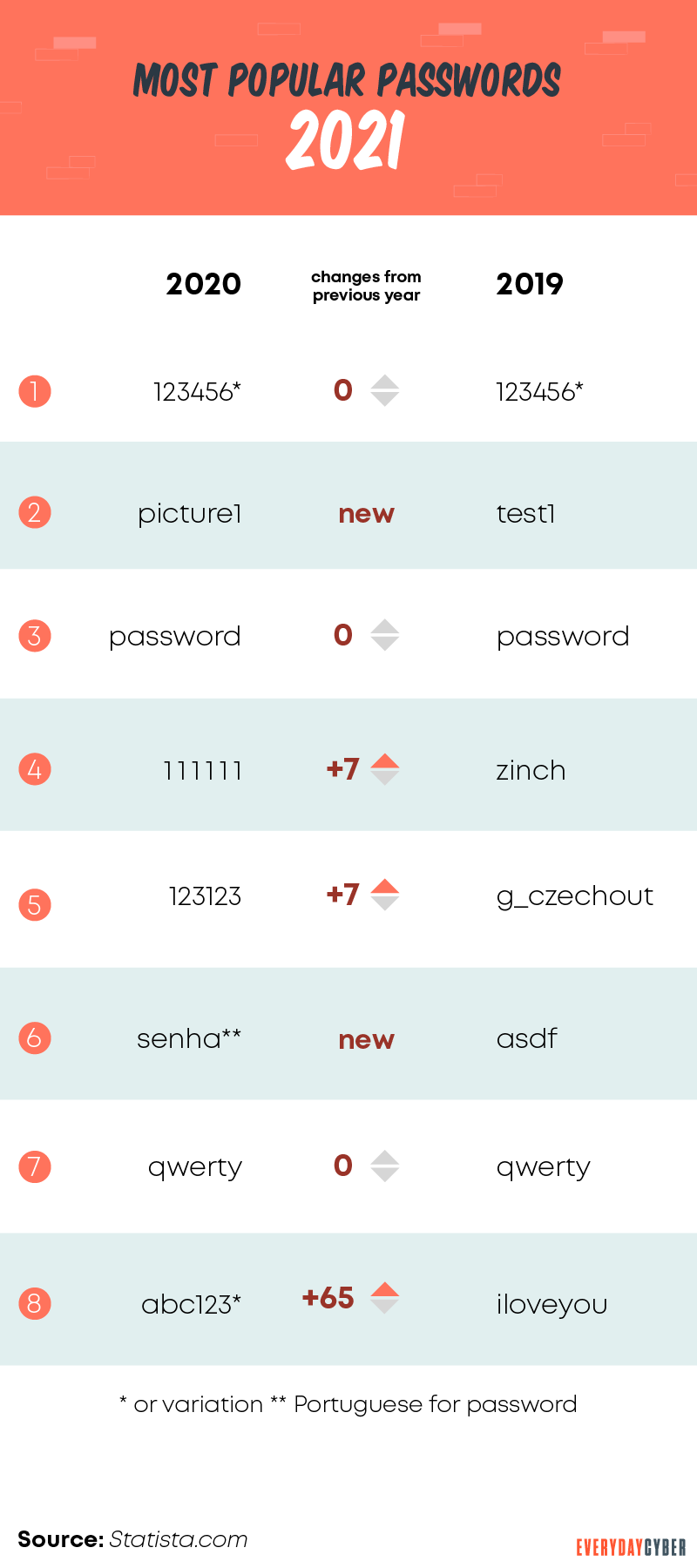
LogMeIn, which owns LastPass, did a study that shows each of us could average 85 passwords across all our online accounts. It’s not surprising when you count all your online accounts. You have banking, social media, media and other digital accounts. So it adds up fast.
We need to protect our personal information, money, and lives from cyber criminals. In many ways, password strength may be the last line of defense. While a pain, starting with good password ideas is a key step in the fight against cyber crime.
Having strong passwords protects your digital life. Yes, it does take a little work, but the numbers show it’s worth the effort. Using strong passwords has always been a challenge. But they are more important than ever for online
Why you need strong passwords
There are many reasons to use strong password combinations. But the primary reason is that the bad dudes have many ways to crack passwords.
Cracking passwords is primarily a math problem. With today’s computing power, solving that math problem can be done faster and faster. With the coming of quantum computers, the speed of cracking passwords will increase exponentially.
4 ways hackers steal your passwords
There are two primary methods for cracking passwords — brute force and dictionary-based attacks.
1. Brute force attack
The brute force method uses every possible combination of characters. It targets the length or number of characters in the password. It may also focus on specific alphanumeric or special characters.
2. Dictionary method
Dictionary attacks use a known set of words. They may be previously hacked passwords or patterns from some defined list. The hackers will try to combine them in every possible way until they find the correct answer.
3. Keylogger attack
A keylogger attack involves a program that hides in your computer memory. It starts to run as soon as you open your computer. The keylogger captures every keystroke you type and creates a log. This log is then sent to the hacker. Keyloggers are often programmed so that they’re hidden in the Processes of your task manager, making them extremely difficult to detect.
4. Social engineering
Social engineering is a popular method hackers use to steal passwords. They trick their victims into revealing their passwords by developing some level of trust first.
Here’s one way this can go. A hacker may get in touch with you with a message that sounds urgent, rewarding, or threatening. For example, they can tell you that your email account is hacked. They will then ask for your login details so they can fix the issue. It may sound crazy to give away your password, but it often works.
Estimated amount of time to crack a password
What’s troubling is the speed at which these cracking methods can operate. Many hackers use clusters of computers, so cracking keeps getting faster. Powerful computers can guess well over 100 billion passwords per second. And the numbers are rising with CPUs and GPUs becoming more powerful. Quantum computing will increase the speed by “orders of magnitude”.
But even with computers getting more powerful, there is still a good case for strong passwords. You can increase password entropy with longer, more complex, and more unique passwords. Password entropy is a measurement of how unguessable a password is. Even with super-fast computers, long, complex and unique passwords are very hard to crack.
Here are some simple numbers based on today’s computing power. This will give you an idea of the effect of password length and complexity on how long it would take a hacker to crack a password.
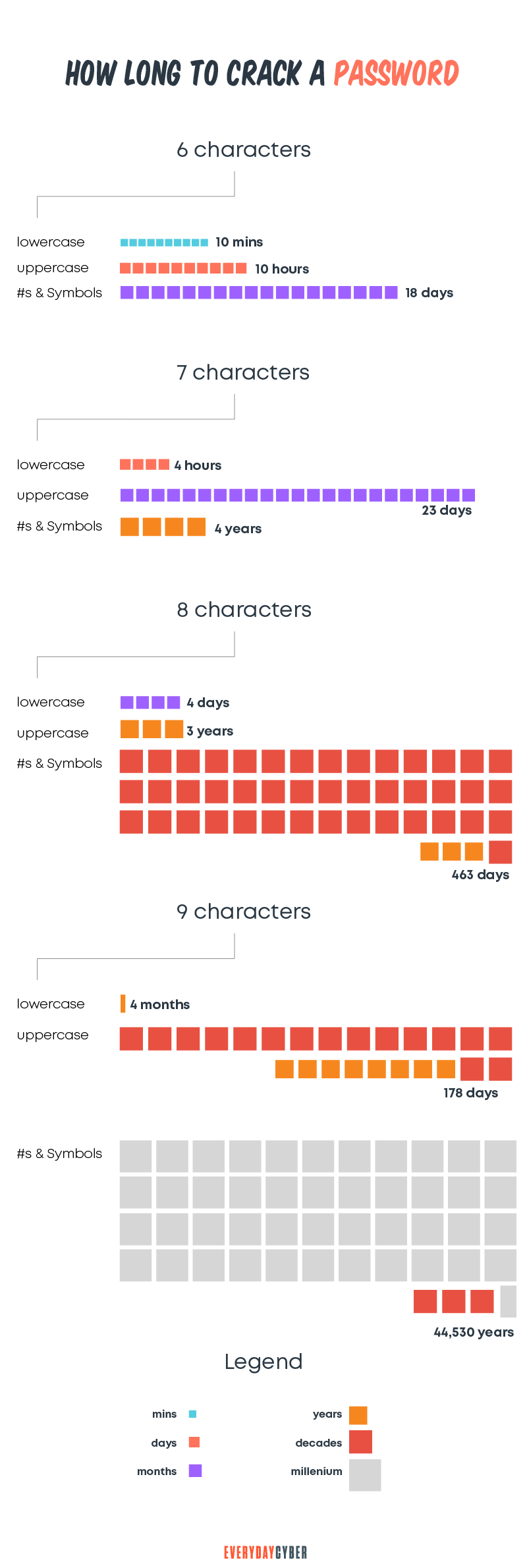
So you can now imagine what a 16 or 20 character password would be like to crack. Longer and more complex is much better protection than simple and short – the math proves it.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
So, what makes strong passwords?
The simple definition of a strong password is one that cannot be cracked using a brute force attack. It is always best to use longer passwords with more possible characters. The probability your complex password gets cracked becomes infinitesimal.
Here are the rules for creating hard-to-crack strong passwords:
- Make long password options. Use at least 12 characters but 16 or 20 is really where you should go.
- Use the widest character set possible – uppercase and lowercase letters + digits + special Characters.
- Use random words or passphrases + special characters.
- Do not use any personal info (name, birth date, house number, pet name, etc.) in the password.
- Use random passwords whenever possible; nonsensical combinations are great.
- Do not use common dictionary word phrases (i.e., Big Dog or Brown house) in the password.
- Create unique password combinations.
- Do not reuse any of your passwords.
- Always logoff/sign out if you leave your device for the day
- Avoid entering your passwords on computers you don’t control
- Avoid entering your passwords on unsecured WiFi connections
- Use a
password manager
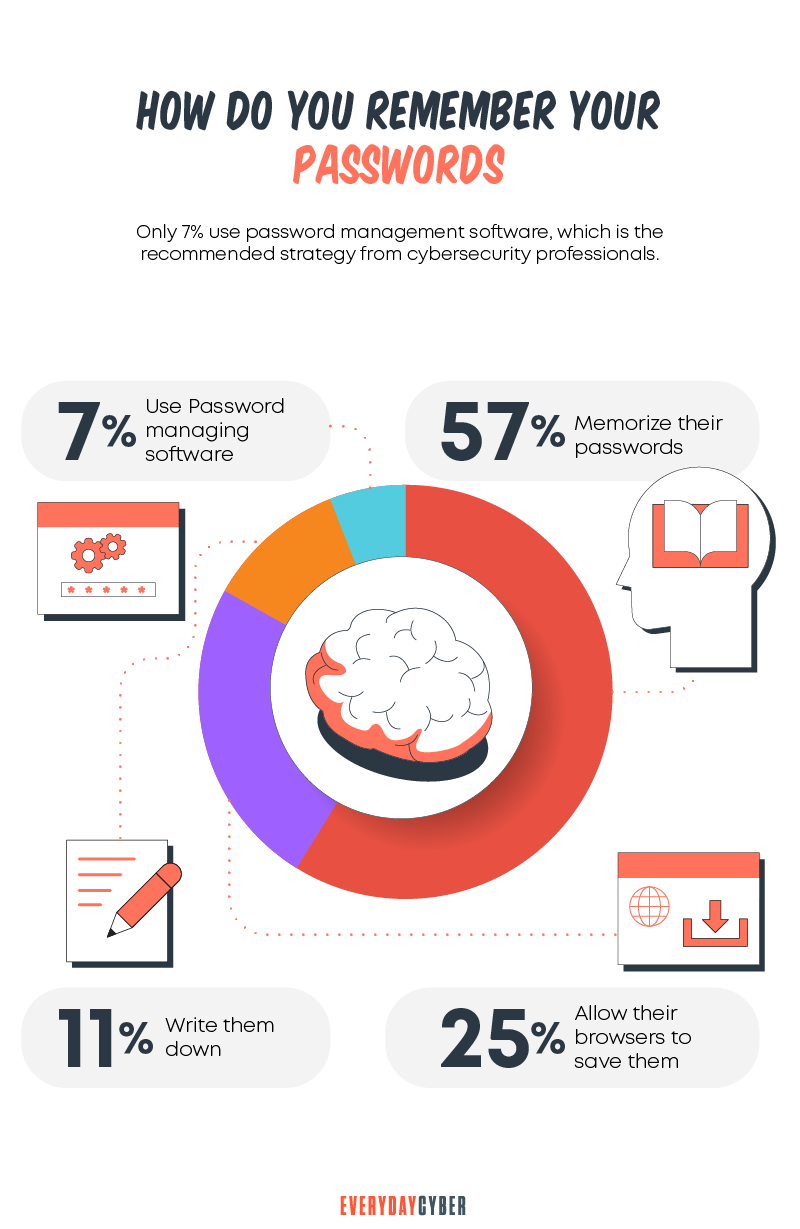
Where to keep your passwords
So, how are you supposed to remember 85 16-character passwords?
This is a challenge, but it’s not impossible to solve. Here are two ways of keeping all your passwords safe.
1. Piece of paper
The first is on a good old piece of paper. Write down your passwords and keep them in a safe place. But someone can break into your house or office and steal that piece of paper. The probability of theft is low, and thieves would have to get into your house or office to get it. But it’s still tedious to have 85 passwords on paper and take it with you everywhere you need to go.
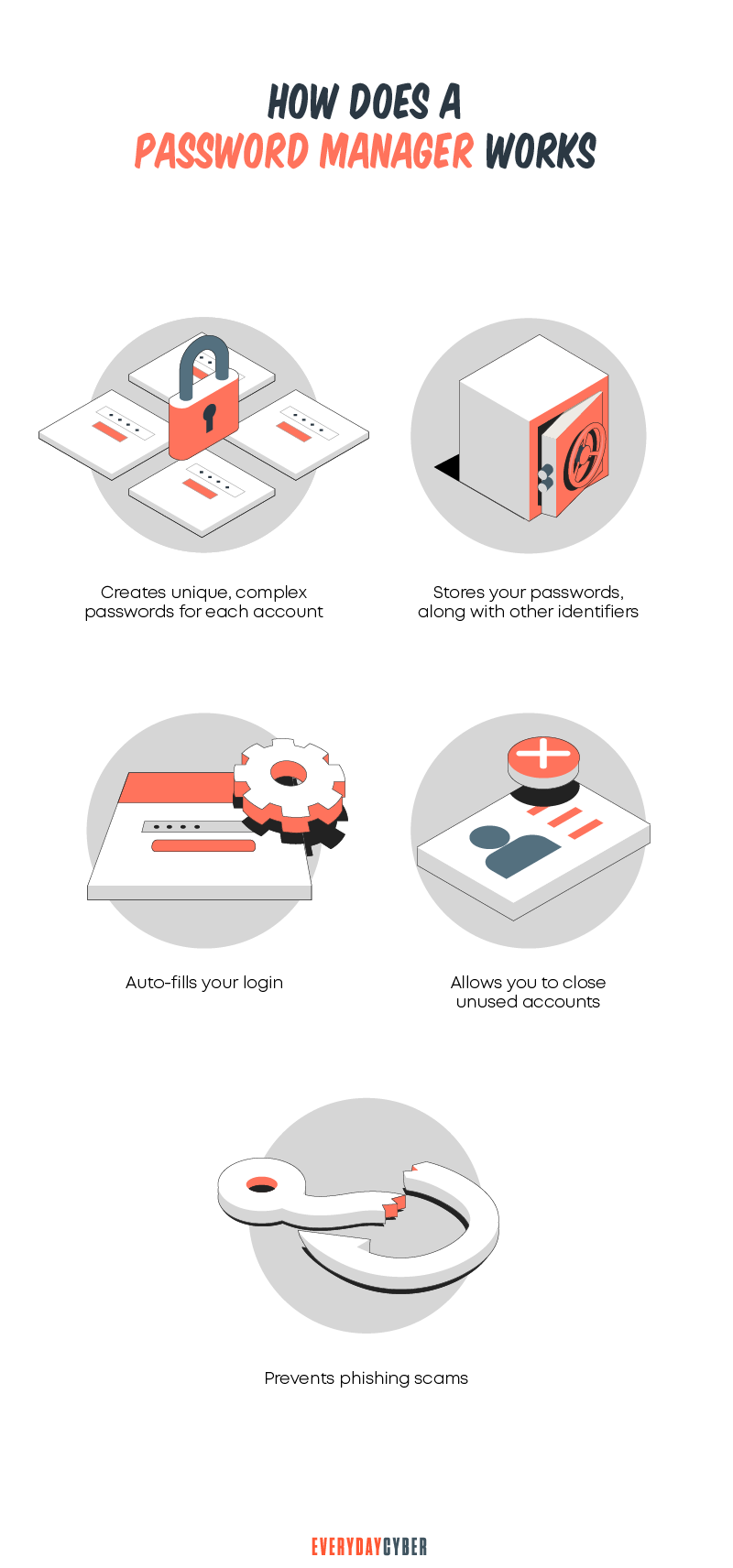
2. Password managers
The second option is to use a
Offline password manager
An offline
Online password manager
An online password manager is delivered via the cloud. The cloud makes it accessible to all your devices.
Both offline and online options support various features. They include a random password generator, password storage, password management, and auto-fill.
You won’t need to remember which username or email address you use for your online accounts. A secure password manager will fill this in for you.
You’ll only need to remember one password, the master password, so you can access all your other passwords. The
Strong passwords are essential, but they don’t help if your password is leaked in a data breach
Data breaches continue to happen at an alarming pace. Having extra protection is even more critical with sensitive data.
These days, you need a secondary method to confirm your
The most common form of secondary authentication is multi-factor authentication (MFA). You’re probably familiar with two-factor authentication, also called
2FA typically sends you a one-time code (OTC) or one-time password (OTP) via text or email. You then enter the OTC or OTP on the service you want to access.
There are other
Final thoughts: You don’t want your credentials to land on the dark web because of data breaches. Good password practices provide the first line of defense to your online accounts. These help you create a strong password culture to strengthen your online
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is DNS Hijacking?
DNS hijacking is no laughing matter. It is a serious security threat that is consuming the cyber world. The critical role of DNS for network security has made a primary target for facilitating mass data theft.
Is a Cybersecurity Risk Assessment Worth the Money?
A cybersecurity risk assessment does more than just identify and analyze threats. It counteracts threats and keeps your IT systems safe.
What is a Rogue Certificate?
A rogue certificate is a valid certificate issued by a legitimate certificate authority. However, it’s untrustworthy because either it was compromised or was issued to the wrong party.
What is a zero-day threat?
A zero day threat is a security flaw known or unknown to the software vendor which hasn't had a patch made to fix the vulnerability.
What is Social Engineering?
Social Engineering in the digital world is the intentional deception and manipulation of victims to cause the release and sharing of confidential information used to commit fraud and other cybercrimes.
What is Malvertising?
Malvertising is advertising malware that infects digital devices with malicious software using online ads and advertising networks as their delivery platforms.


