Keyloggers, which is the abbreviation for keystroke loggers, are a particularly nasty piece of malware (malicious software).
Their primary objective is to track and capture all actions executed on your device. Most keyloggers are used for evil intent but there are cases where keyloggers can be used for legitimate purposes.
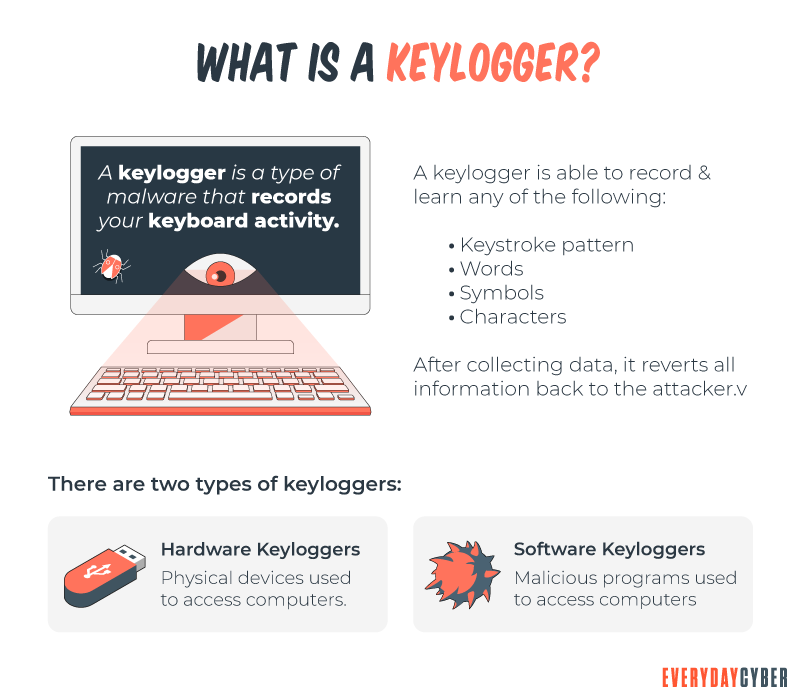
Keyloggers, sometimes referred to as spyware or monitoring software, are essentially digital surveillance. They can track every click, touch, keystroke, download, and conversation carried out on the device you install them on. The list of specific information keyloggers are known to capture are:
- usernames and passwords
- credit card numbers and verification codes
- chat histories
- lists of websites you’ve visited
- apps used
- documents opened
- screenshots
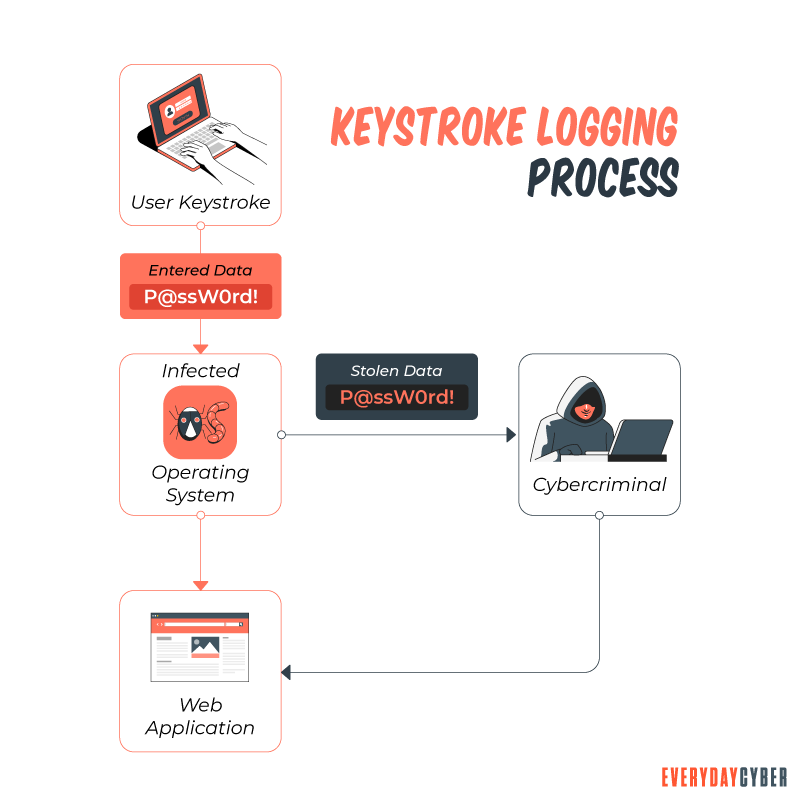
For bad actors this information is used to steal your data typically for financial gain, but also for other things like extortion and
- parents monitoring their children’s online activity
- law enforcement to track incidents linked to the illegal or misuse of digital devices
- employers monitoring that their employees are doing work and not just surfing the web all day
So how does a keylogger get on my device?
For legitimate uses, it would be installed on each device much like any other application. For bad purposes it spreads in the same way that other malware spreads – emails, SMS, downloads, trojan horses, etc.
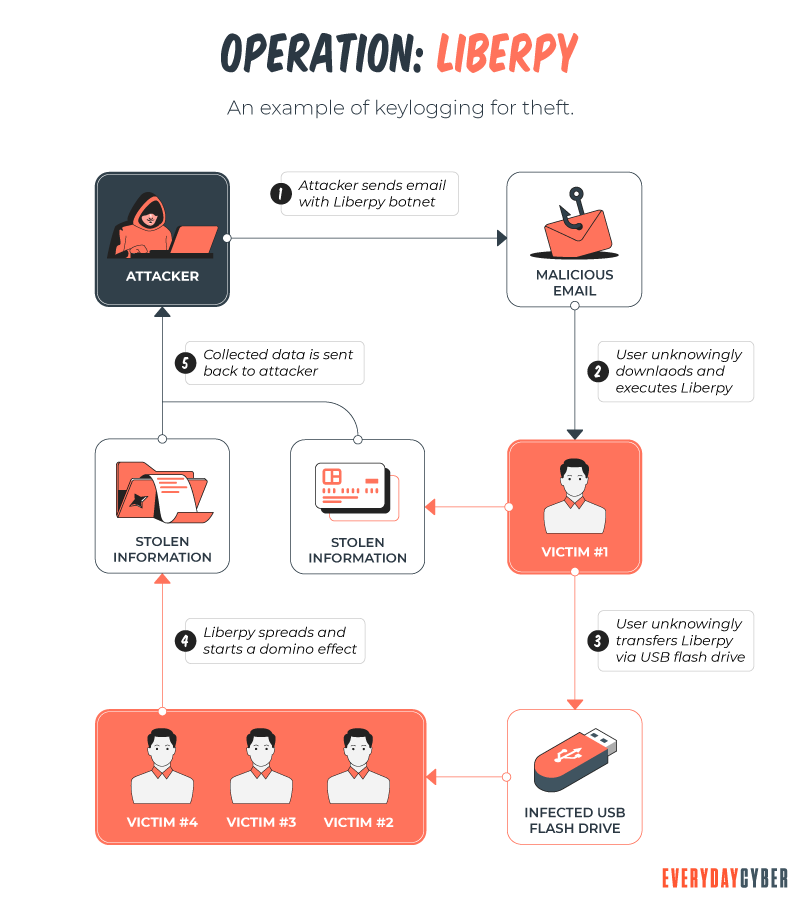
So how do you detect a keylogger?
Unfortunately, keyloggers can be tricky to detect. Some indicators that a keylogger may be on your device include: slower performance when web browsing, mouse movements or keystrokes pause or don’t show up onscreen as you expected or if you receive error screens when loading graphics or web pages.
You can also proactively check your device to see if a keylogger is running by:
- reviewing what processes are running on your device. For example, on Microsoft windows use “Windows Task Manager” to see if there are any suspicious apps or processes running.
- reviewing your firewalls activity log for suspicious traffic. Check what is going into and out of your device and what sites such communication is coming from/going to.
- Install an effective Antivirus/Antimalware tool to scan for and remove Keyloggers.
One last point on checking for keyloggers. There are also hardware keyloggers that can be installed between your keyboard and your device. These can be non-obvious attachments or dongles that may appear normal but are in fact a hardware device that captures keystrokes. So be diligent and always check for unusual items connected to your computer or
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
So how do I protect myself from a keylogger?
Like all malware, the best tools to avoid being contaminated with such nasty things is to stay away from untrusted websites, don’t download any software or app that you don’t trust 100%, and do not click on any link you are not 100% sure is safe.
But as we all know, sometimes in our busy lives we have “Duh” moments and end up clicking, downloading or surfing the wrong link, file or website. So you need to protect yourself with tools.
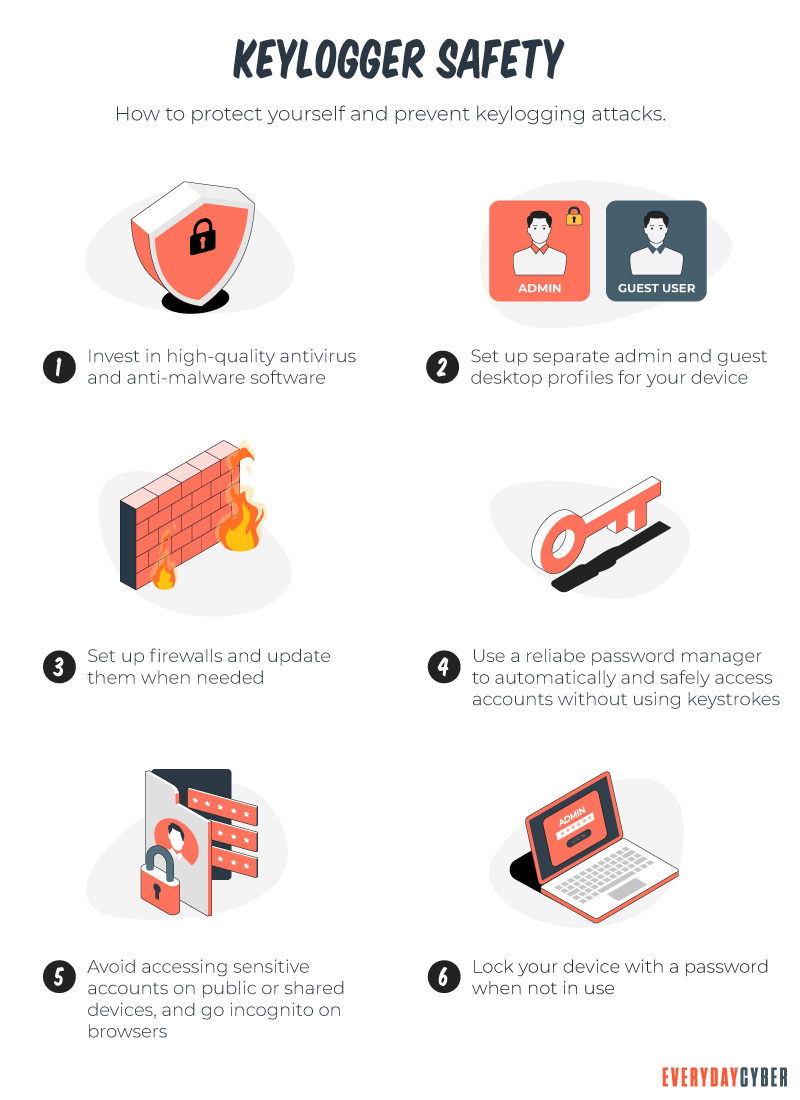
Install quality antivirus/antimalware onto your devices. These tools are designed to scan for, locate and remove malware including and especially keyloggers.
- Setup firewalls on your network and if your device has a personal firewall, enable it.
- Lock your device when not in use. Hopefully you can trust people in your household but for sure lock it when you are in public. Best practice is to ALWAYS lock your devices when not in use.
- Use other tools like password managers, to help protect your sensitive and confidential credentials and information.
- Be hyper careful on public or share computers. These are a hacker’s playground. Just assume all public computers and digital devices are watching you.
Keyloggers are not your friend.
Installing specialized tools like antivirus,
Be skeptical of everything online!! The biggest threat having malware installed on your device is “social engineering”. The bad actors understand human behavior and use everything imaginable to lure unsuspecting victims through tantalizing offers via email, alerts, sms messages, fake profiles and all kinds of offer mechanisms to get you to click.
Once you click, the damage is probably done. Do NOT trust any link or file or document unless you are 100% sure it is from a trusted source. Do not click if you don’t know.
Triple check before you download
Doesn’t matter if it’s a file, a document or an app. Like the previous item, don’t trust anything online at face value. Check, check and then check again before you download anything.
Be careful where you browse
Malware is becoming more sophisticated every day and it is now possible for certain types of malware to cause your devices harm without actually downloading onto your device. Simply browsing to a website that is designed to execute, what is describe as “drive by” infection, can cause you harm. So be aware of every site you navigate to, search for information about the site before you go to it. See if there is any information indicating that it could cause you damage. Be diligent, take a second before you go to a site you don’t know, it could save you a world of pain.
Get an ad-blocker
Malvertising is a particularly nefarious form of malware which presents itself as a popup ad or banner on a website. Bad actors use these as platforms for launching all kinds of malware simply by you hovering over the ad or banner. Get an ad-blocker it will make your browsing a lot more pleasant.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Hacking?
Hacking is an old game in the cyberworld with ever changing players and techniques. It may be done with good intentions or malicious motives. It is growing rapidly because of the proliferation of devices.
Strong Passwords. One giant step to protect our digital lives
Here's how to create long, complex, and unique passwords to protect your accounts and keep your sensitive info safe from hackers.
What is a Firewall?
A firewall blocks outsiders from gaining unauthorized access to your computer and helps stop malicious software from infecting your computer.
Element Chat Review: How Secure Is It, Really?
Element is a secure messaging app for safer personal and corporate communication and other group chats.
12 Ways to Help Older Adults Stay Safe Online These Days
Seniors, like everyone else, have special vulnerabilities in addition to the common Internet risks. They have specific characteristics that make them vulnerable online, particularly to online fraud. Isolation and lockdowns caused by the pandemic have forced seniors to embrace technology like never before. Here are 12 ways to key seniors safe online.
What is 256 Bit Encryption?
256 bit encryption has quickly become the industry standard for ensuring security of your data, security of your communication and is really now minimum encryption level for securing your digital environment.

