Managing critical assets, intellectual property, customer data, and other sensitive information involves risks. This is where risk assessment comes in.
Unfortunately, cybersecurity risk assessment isn’t a top priority for many small business owners. Some say it’s too complicated, time-consuming, and expensive. Others say it’s just for compliance or show. Still, many others feel they are not prime targets of cyber attacks.

Numbers don’t lie: 10 pieces of cyberattack statistics you need to know
Cyber risks are real. This has been shown in study after study. The statistics on cybersecurity are not comforting. But knowing them might help you develop
Here are shocking figures that should open your eyes to the dire state of cyber
- Small business cyber incidents increased by 424% in 2020. This is five times the figure of the previous year.
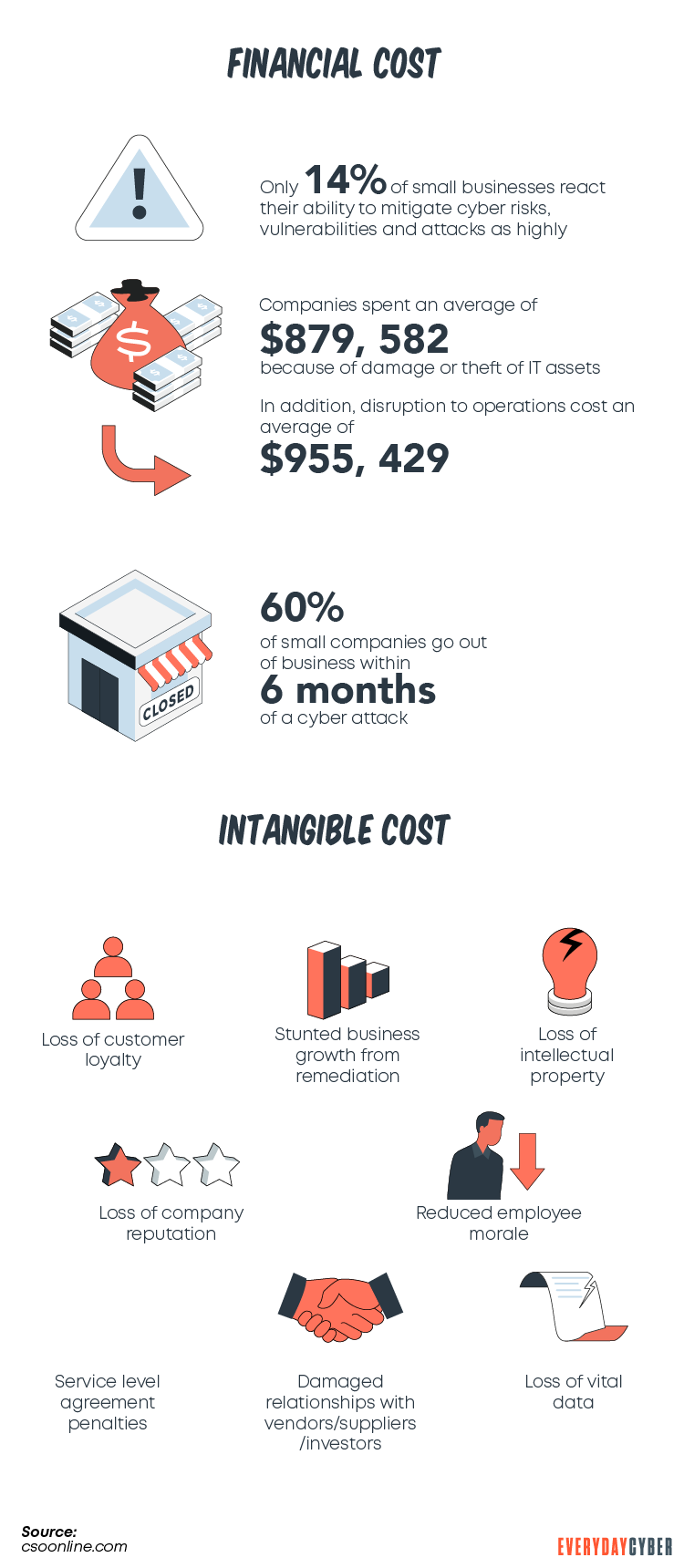
- 60% of small businesses that are victims of cyber attack attempts go out of business within six months.
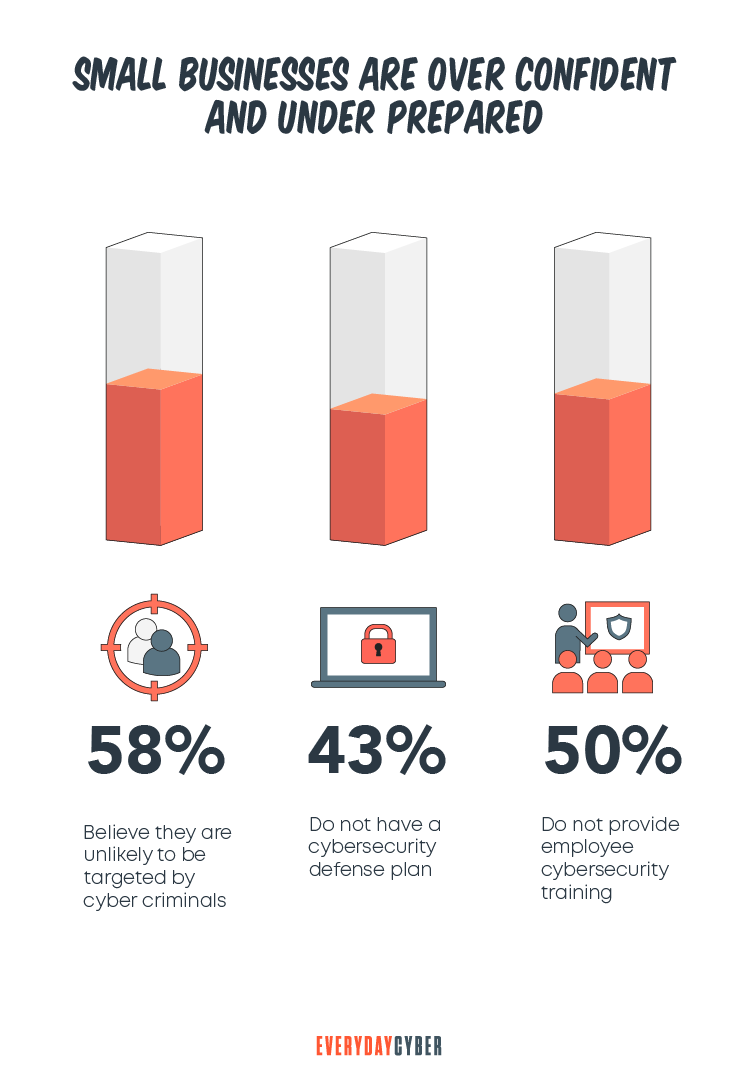
- 43% of cyber attack efforts target small businesses.
- 54% of small businesses believe they’re too small for a cyber attack.
- 65% of small businesses didn’t know what to do following a cybersecurity attack.
- 63% of reported data breaches happened due to weak, stolen, or default passwords.
- 66% of small businesses are worried or extremely worried about cyber risks.
- 94% of detected malware in small businesses came through email.
- 65% of small businesses failed to rectify their cybersecurity system after an attack.
- Projections show cyber attacks will cost $6 trillion in 2021.
What is cybersecurity risk assessment?
A
It also includes a careful analysis of all potential threats and identifies the vectors for vulnerabilities in the IT system where sensitive data resides.
Risk assessments should be ongoing activities, not one-off affairs. IT experts recommend an assessment every two years. But you can do it more often as risks arise and new threats develop all the time.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Why you need to conduct cybersecurity risk assessments
Conducting complete risk assessments is expensive and can take time. But the money and time you invest are worth it.
What benefits can your business get from a complete risk management process?
It helps you become prepared for cyber threats
If you’re aware of the cyber threats, you can prepare for them. As they say, it’s always better to be on the side of caution than to be sorry when it’s too late.
In short, a risk assessment highlights your preparedness to combat cyberattacks. It also strengthens your ability to recover from such incidents if they occur.
If you overlook risks and fail to identify threats, you can always go back to the risk assessment process. Review what went wrong, improve your cybersecurity frameworks, and change your preventive measures.
Risk assessments also help you mitigate the impact of the damage immediately. This is so you can take steps to patch the vulnerability and make sure it doesn’t happen again.
It helps you discover hidden threats
You can’t fight an enemy you can’t see. An assessment with a risk-based approach helps you identify hidden risks that usually exist in social media and in public Wi-Fi networks.
It helps you mitigate future risks
Risk assessments help your business mitigate future hacks and breaches. They save time, money, and resources. These assessments also help you prepare for the worse, even if the worse never comes.
Existing risk assessment programs can serve as templates for future assessments. Consider them a recurring maintenance need for your business.
It helps you make more informed decisions
A cyber
4 components of a cyber security risk assessment
Tackling complex risk assessments isn’t easy. The National Institute of Standards and Technology (NIST) endorses various assessment templates. They also offer robust guidance and supporting documents for the risk assessment process.
Small businesses can tailor their cyber
1. Company risk profile
You’ll need to develop the risk profile of your business. Consider your business type, operations, and priorities. A financial company will have different
2. Technology assessment
Technology resources include both hardware and software. They make up the core digital infrastructure of most businesses. But many SMBs can’t bankroll a comprehensive cyber
You can decide on an in-house team or an outsourced partner. In any case, you should sit down with the team and ask the following questions:
Are all devices and software properly configured and regularly updated?
Unfortunately, devices and software are vulnerable to various risks. But many responsible vendors check and track products they roll out. They deploy updates to patch vulnerabilities that bad actors can exploit. Familiar with zero-day attacks? These are attempts to exploit vulnerabilities that the vendor has not identified. New product or new version roll-outs are prone to these attacks.
Are all antivirus and anti-malware programs updated?
Viruses and malware evolve daily. That is why the
Is your Intrusion Detection System (IDS) deployed across your network?
An IDS acts as the last line of defense when all the first lines fail.
For example, an attacker may successfully gain an admin password through phishing. His next attempt would be to access a secure server from an unrecognized IP address. If your IDS is working, it should be able to detect this move and thwart the attack.
Are all incoming and outgoing information traffic secured?
Traffic involves all information coming in and out of the system. It includes all communications through emails, websites, and virtual private networks (VPNs). You can secure emails with encryption and spam filters to block malicious attempts. A centralized spam filter helps sift poisoned communication before they reach employee mailboxes.
Do you adopt a layered approach to cybersecurity?
A segmented approach helps prevent total
- Network perimeter
security - Endpoint
security - Authentication protocols
- Real-time monitoring
- Backup and disaster recovery
3. Governance practices assessment
Governance practices include guidelines, procedures, and policies for risk assessment. Your assessment should include the following:
Access control practices
Limit access only to authorized users who need them in doing their jobs. Ban weak passwords. Restrict password sharing. Prevent access from unsecured networks like public Wi-Fi. Prohibit the use of unauthorized devices to access work.
Supply chain endpoint management
Small businesses do business with outside vendors and third-party partners. They contract them for products and services they need to operate their businesses. They use
Your
security risk assessment should consider a provision for endpointsecurity . Use asecurity integration tool that secures all endpoints run under a unified dashboard. Devices not enrolled in the system cannot be used in any transaction.
Bring your own device (BYOD) assessment
Devices owned by employees are likely targets for malware. Malware may hop to corporate servers and other endpoints through these infected devices. Apply a
4. Assessment of people
The enemy from within is often more dangerous than a hacker from outside. They can cause real risk exposure on purpose or by mistake. Employees have access to systems and know their way around the network. A thorough assessment of your people should include the following:
Implementation of incident reporting
Every employee should report perceived anomalous practices of other employees. These may include unauthorized access, use of unsecured BYOD, and password sharing. They should also watch out for and report abnormal behavior of equipment.
Full-scale end user cyber security training
Some employees think that such training programs are repetitive, boring, or obvious. But cyber threats are always evolving, and you never know when the next attack will happen.
Experience is one of the best teachers. Try to include a phishing vulnerability test in your training. Use an online phishing simulator to send phishing emails to email inboxes anonymously. Observe how your employees respond. The results will help you measure their level of awareness of
Our final thoughts. A cyber
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
Lock the Door. Bad Passwords: The Greatest Threats to Password Security
Bad passwords are the entry way for hackers to get into your accounts. Learn how to protect your cyber assets by using better passwords now.
What is HTTPS?
HTTPs enables web servers and web browsers to establish secure connections. It encrypts data being transmitted in both directions. This helps prevent thieves from stealing sensitive information along the way.
What is Malware?
Malware or “malicious software” is a cybersecurity term used to describe software that steals your data, spies on you, damages your devices, and generally causes chaos and destruction.
5 Powerful Ways to Protect Your Business from Vishing
Vishing is a cybercrime that’s threatening people all over the world. And it’s not expected to go away anytime soon.
What is a Potentially Unwanted Program (PUP)?
PUPs refer to programs, applications and other software downloaded onto computers or mobile devices that may have an adverse impact on user privacy or security. The term “potentially unwanted program” was coined by McAfee to distinguish the program from malware.
What is Business Email Compromise (BEC)
Business email compromise is one of the most financially destructive cyber crimes. These are emails that appear to be sent by known or trusted sources asking for something legitimate.

