DNS hijacking is no laughing matter. It is a serious
The results of the 2021 Global DNS Threat Report done by
The figures depict the critical role of DNS for network
Attackers targeted organizations relying on remote work as a result of the pandemic. They have also diversified their toolkits to enable them to carry out more sophisticated attacks.
About 87% of organizations surveyed suffered DNS attacks, experiencing an average of 7.6 attacks. The report estimated the cost of each attack to be around $950,000.
The most affected country was India with an average of 10 attacks. Malaysia, Spain and France also experienced significant increases in damages.
Aside from DNS hijacking, the EfficientIP report included other forms of attacks that increased, such as:
- DNS phishing at 49%
- DNS-based malware at 38%
- DDoS (Distributed-Denial-of-Service-Attack) at 29%
- DNS tunneling for command and control at 24%
- Zero-day bugs at 23%
- Cloud misconfiguration abuse at 23%
The report also showed a noticeable increase in data theft caused by DNS attacks. Among the organizations surveyed, 26% reported that sensitive customer data were stolen.
That is the sad state of the world’s DNS
- Strengthening the privacy of remote workers with a private DoH (DNS over HTTP) solution
- Automating the life cycle management of IP resources to eliminate cloud service downtime caused by misconfiguration
- Enabling DNS as the first line of defense against attacks
What is a DNS?
To better understand DNS hijacking, let us look at some basic things about a DNS or domain name system.
Every device connected to the Internet has its own Internet Protocol (IP) address to identify itself when communicating with other devices. When browsers want to connect to a website, they type the domain name of that website in the search bar instead of the IP address, which is a string of alphanumeric characters.
For example, if I want to access the website of XYZ Company, I enter its domain name xyzcompany.com instead of its IP address of, say, 192.120.1.2. The DNS turns human readable domain names into unintelligible numeric IP addresses. This eliminates the need for browsers to memorize boring, lengthy numbers, while feeding machines with something they work best with — numbers.
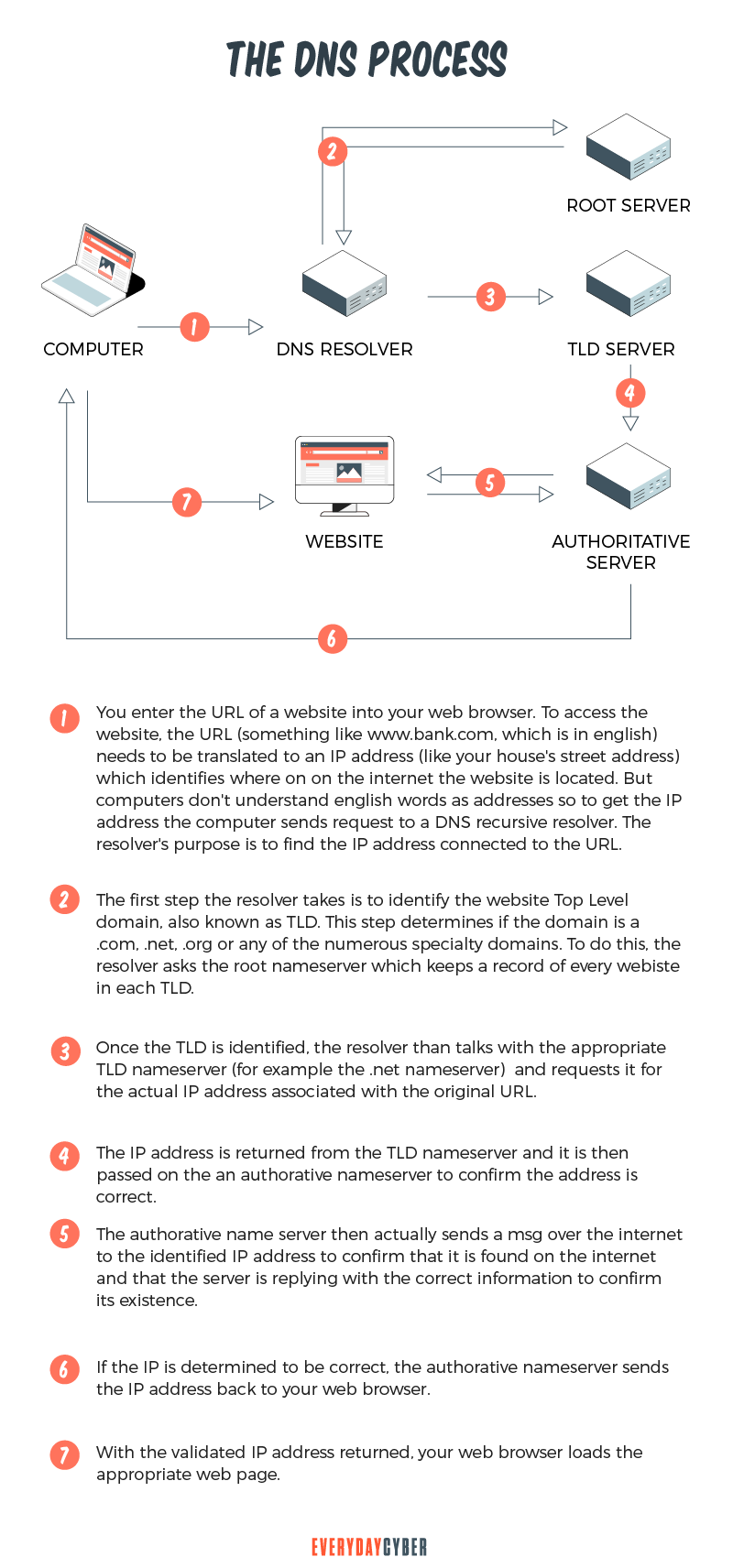
How does DNS work?
When you type a URL into the search bar, this URL has to go through four servers that work together to find and deliver the correct IP address to you. They include:
DNS recursor
Also known as DNS resolver, the DNS recursor receives queries from DNS clients. Then it communicates the queries to the other three DNS servers.
Root nameserver
The root nameserver contains the root zone which is home to various specific locations. The job of the root nameserver is to answer requests sent to it by sending back a list of the authoritative nameservers that go with the top level domain (TLD).
TLD nameserver
The TLD, or top level domain, nameserver hosts the IP addresses of the second level domains contained in the TLD. It then releases the IP address of the specific website and sends the query to the domain’s nameserver.
Authoritative nameserver
The authoritative nameserver is the last stop in the query. If it has access to the requested record, it will return the requested IP address back to the DNS recursor that made the initial request.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
What is DNS hijacking and how does it work?
So now we know the role of DNS when we are surfing the net. It plays the crucial function of helping us go to websites and accounts we need in our businesses, jobs and daily lives. But we also know that domain name systems are vulnerable to attacks.
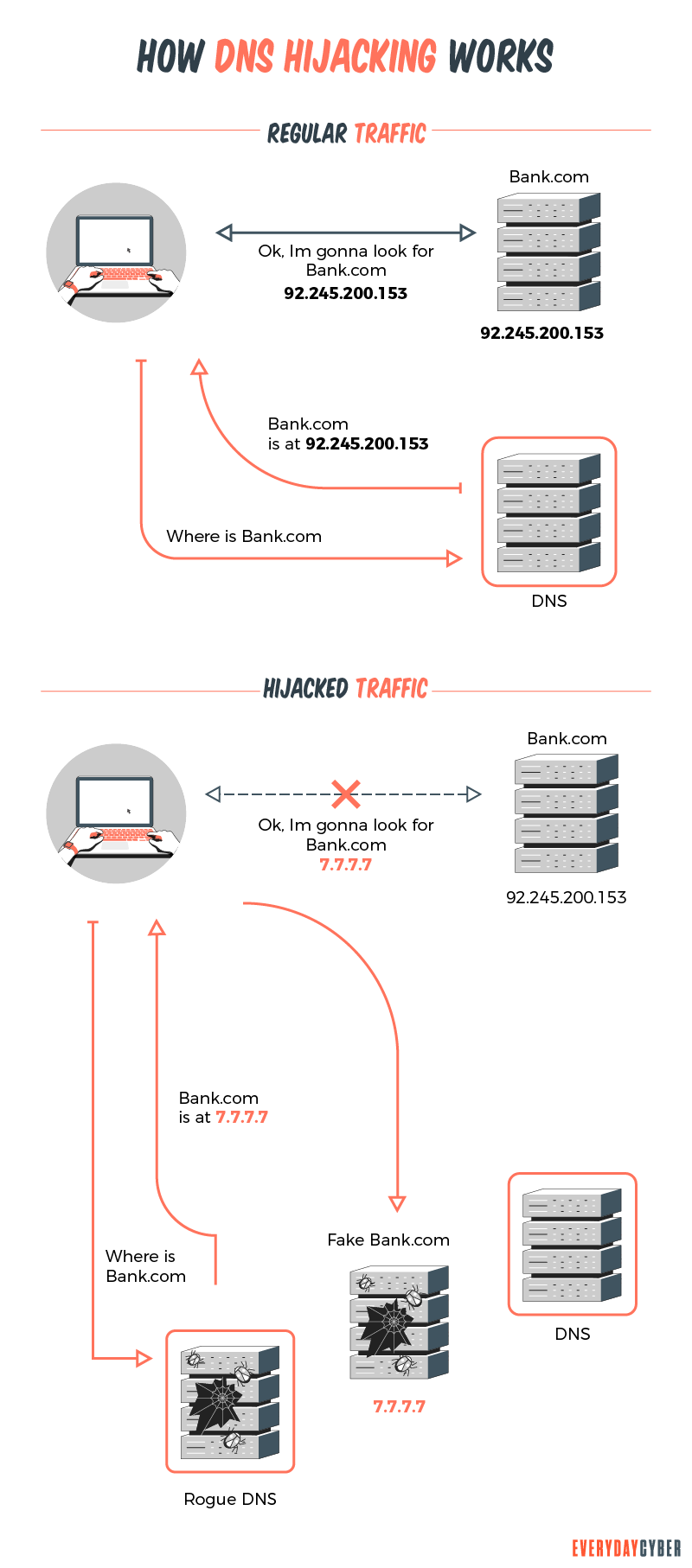
Cyber criminals are aware that a domain name system is a trusted protocol and use it as a significant part of the attack process. Also called a redirection attack, DNS hijacking is an attack on a domain system. It could be a vicious move to redirect website users to malicious websites or an attack on the DNS to make it unavailable.
Why would attackers want to hijack a DNS?
The most obvious reason for hijacking DNS is money. Profiteering hijackers steal money from users’ bank accounts, credit cards or sell stolen personal data on the dark web.
In other cases, crooks resort to DNS hijacking for phishing purposes. They hijack the DNS to redirect users to malicious websites that are aimed at stealing users’ credentials and other data. Some hackers also use DNS hijacking for pharming, a scheme similar to phishing in that users are redirected to fake sites. In pharming, these fake sites display unwanted ads which, when clicked, generate revenue for the hackers.
It is also common knowledge that some Internet Service Providers (ISPs) use DNS redirection to collect data from users to tailor ads in line with their preferences. A few government agencies also use DNS hijacking for censorship.
What are the types of DNS hijacking?
When attackers hijack your DNS, they are able to intercept your email communications and entire web traffic. They do it in various ways which brings us to the types of DNS hijacking.
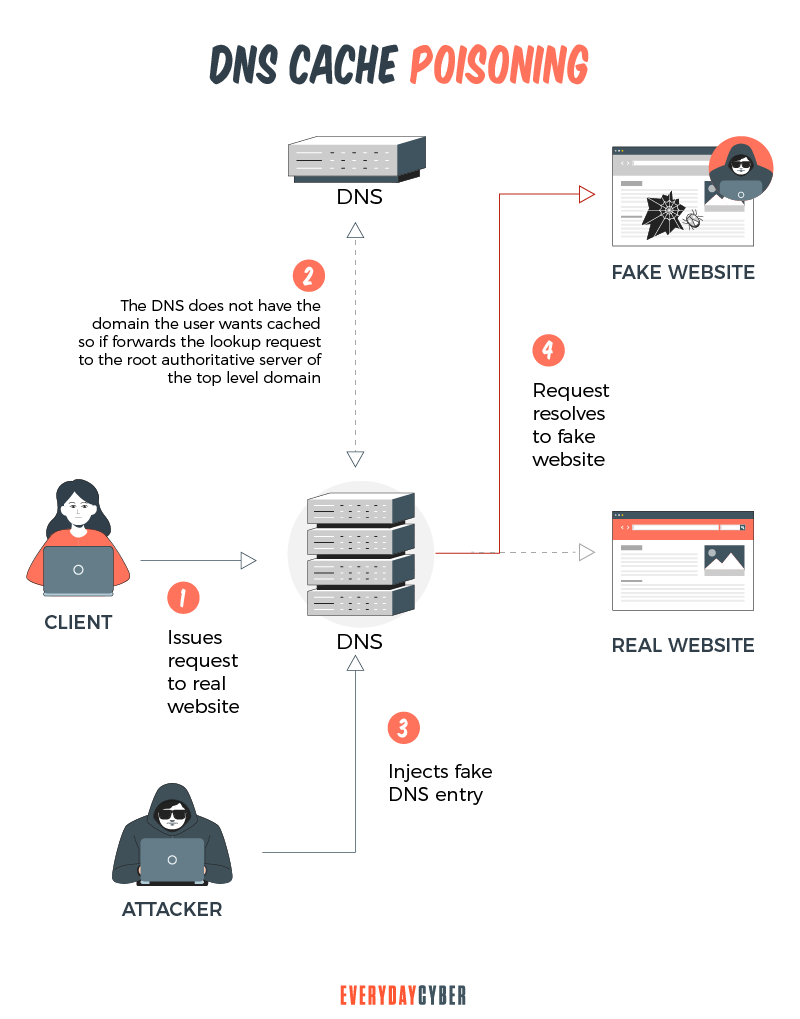
DNS Cache Poisoning
DNS cache poisoning is how hackers achieve DNS spoofing, by replacing DNS data that redirects users to an unsafe, hacker controlled website.
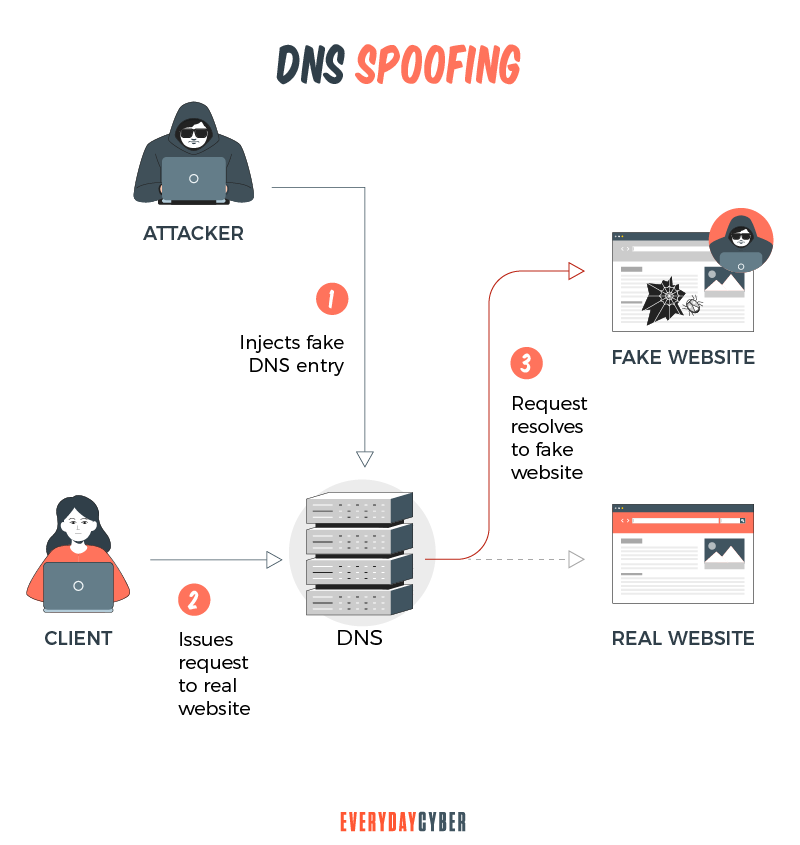
DNS Spoofing
DNS spoofing is the process where users are actually redirected to an unsafe or hacker controlled website because the cache poisoning process worked, making users vulnerable to cyber threats and data being stolen.
Local DNS hijacking
This type of hijacking happens when cyber criminals hack an internal computer to install Trojan malware disguised as legitimate software. Once inside the computer, the Trojan gives hackers access to the computer’s network systems to steal data and change the DNS settings to redirect requests to fake websites.
Router DNS hijacking
DNS routers are often the first points of attack because criminals know that many users do not change their default admin login credentials from the time the devices were delivered. A DNS router is a piece of hardware used by domain name service providers to link domain names to their corresponding IP addresses.
Hijackers target vulnerable DNS routers and once logged in, they override and reconfigure the DNS settings to redirect traffic to their own server to control the conversion of a domain name to an IP address. They then send users to malicious sites to enable them to do their craft.
Man-in-the-middle DNS hijacking
In a man-in-the-middle attack, fraudsters operate within the communication of a network server and a DNS server to intercept information. Many DNS requests lack encryption. This enables criminals to read, manipulate and map out the communications to a malicious IP address. The genuine DNS server is bypassed and never gets to receive the request.
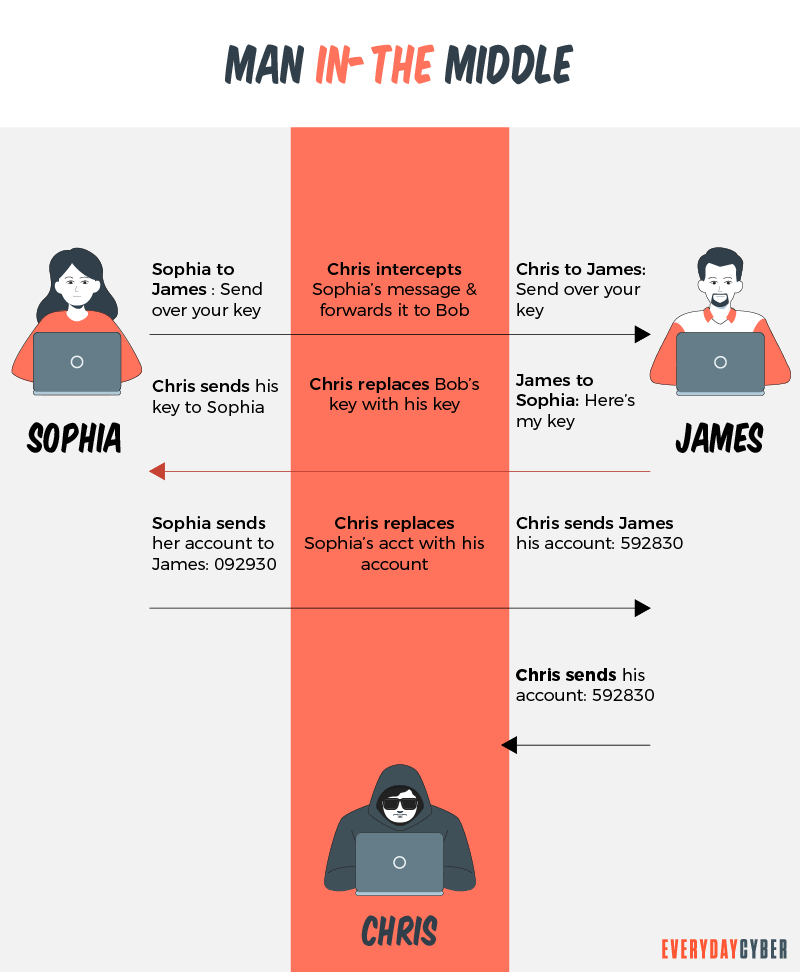
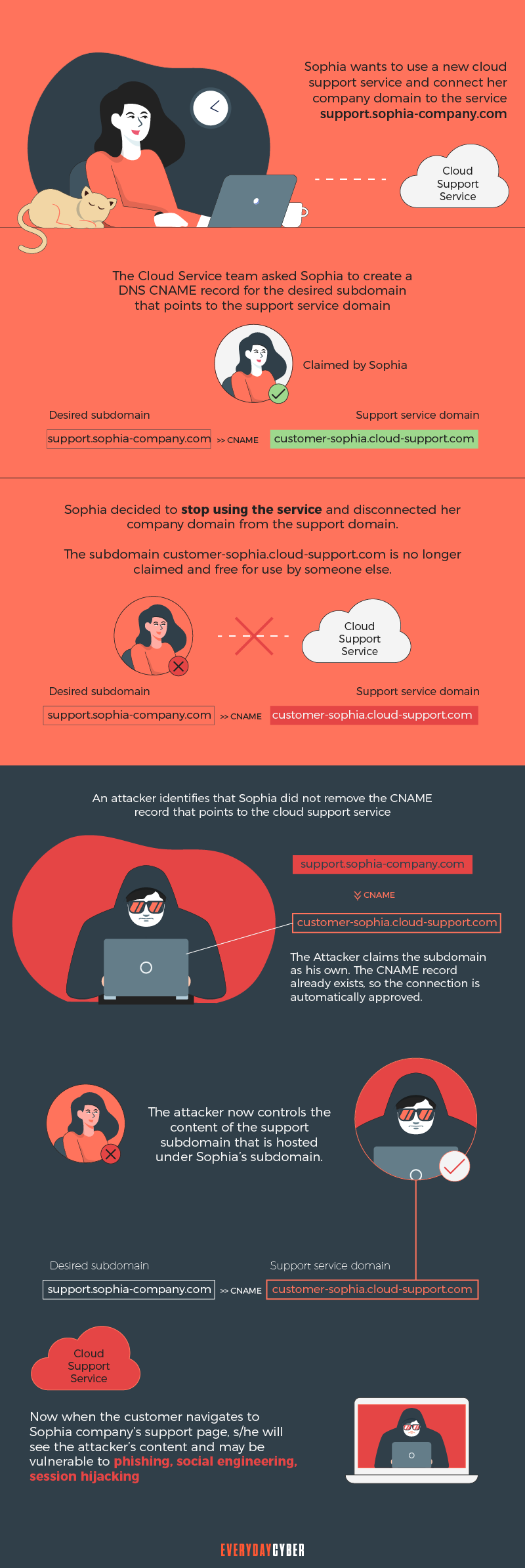
Rogue DNS hijacking
Rogue hijacking involves the Internet service provider’s domain name server. Hackers get partial control of the server so that even if users technically access the “correct” server, they can still be redirected to harmful websites.
Domain name server providers with sufficient resources at their disposal have boosted their
How to prevent DNS hijacking
Have you ever experienced site unavailability, browser redirects, slow downs, frequent pop-ups and other unusual behavior of your device when browsing? Chances are you may be a victim of DNS hijacking attempts. Here are some ways of mitigating DNS hijacking.
Preventive measures for nameservers
A “nameserver” is a valuable part of the domain name because it connects a URL to its corresponding IP address hosted in the website’s server. As such, it must be protected with powerful
- Installing firewalls for the DNS resolver with no access from outside the organization to ward off any attacks. As an added remedy, shut down all resolvers that are not needed.
- Increasing restrictions to nameserver access to ensure paths for hijacking inside the firewall are blocked. Further secure the nameserver with firewalls, multi factor authentication and other network
security measures. - Mitigating cache poisoning by randomizing source port, query ID and upper and lower case characters in domain names. Cache poisoning is an attack in which criminals alter old or cached records to redirect traffic to a fake website that resembles its intended destination.
- Patching vulnerabilities as soon as they are detected
- Providing a separate server each for the nameserver and resolver so that an attack on one would not affect the other.
- Avoiding zone transfers whenever possible because a hacker can pose as a nameserver requesting a zone transfer to get a copy of all the data in the zone server.
Preventive measures for website owners
Website owners using a Domain Name Registrar should take the following steps to avoid DND redirection:
- Tightening access to DNS connectivity and allowing it only to authorized IT team members. In addition, implement multi factor authentication and designate a whitelist of IP addresses that are allowed to access DNS settings.
- Implementing client lock to prevent changes to DNS records without approval by a designated individual. Use DNSSEC (Domain Name System
Security Extensions) as an added layer ofsecurity to provide cryptographic authentication.
Preventive measures for website users
Website users can help prevent DNS hijacking by:
- Using strong passwords and changing them frequently
- Installing
antivirus software - Using an encrypted virtual private network channel
- Avoiding interaction with suspicious websites
- Avoiding reliance on public Wi-Fi
Impact of DNS hijacking to business
The impact of DNS hijacking to business varies depending on the threat. If the attack is on privacy or confidentiality, the impact may be minimal.
What could end up with a huge impact is a DNS hijacking that involves data breach on personal information. The business owner could face legal action and hefty damages.
Financial institutions like banks, credit card companies and lenders are especially vulnerable and are the favorite targets of criminals. If personal information of their clients are leaked or stolen in a DNS attack, they could suffer massive financial losses and loss of trust and confidence.
Owners of legitimate sites that are spoofed could also experience irreparable brand damage, lawsuits and financial losses.
For online business owners, lengthy outage bouts caused by DNS attacks could lead to massive loss of sales, opportunity and reputation.
In the final analysis, DNS hijacking is a clear and present danger to all things online. It is one of the most sophisticated, often unnoticed, cyberattacks. The bad actors are stepping up their hijacking strategies on businesses, government agencies, healthcare systems, educational institutions and other important organizations.
While the threats are real, they can be prevented if you stay vigilant to
From now on, be on the lookout for unusual activity on your website and take immediate action on the first suspicion of a threat.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Back Door Threat?
In cybersecurity, a Back Door Threat enables a hacker to gain unauthorized access to a computer or digital device at any time.
What is a Website Security Certificate?
A website security certificate is a digital certificate that asserts the identity of a website. It’s a virtual file approved by an industry-trusted third-party called a certificate authority (CA)
What is Spyware?
Spyware is malware that infects your digital device, spies on you, and sends your private data back to the cybercriminals.
What is a Botnet and How to Protect Your Business from One?
A botnet is a network of computers that work as a collective to infiltrate your device. Here's how to protect your business from botnets.
What is a Password Manager?
A password manager is an encrypted storage system for keeping and managing passwords usually protected by a master password. Some password managers use biometric data to protect the vaults instead of master passwords. Still others support the use of two factor authentication for higher security.
10 Cyber Security Stats Every Small Business Needs to Know
Knowing the right cyber security stats helps your business fight off and recover from cyber attacks. Get informed.


