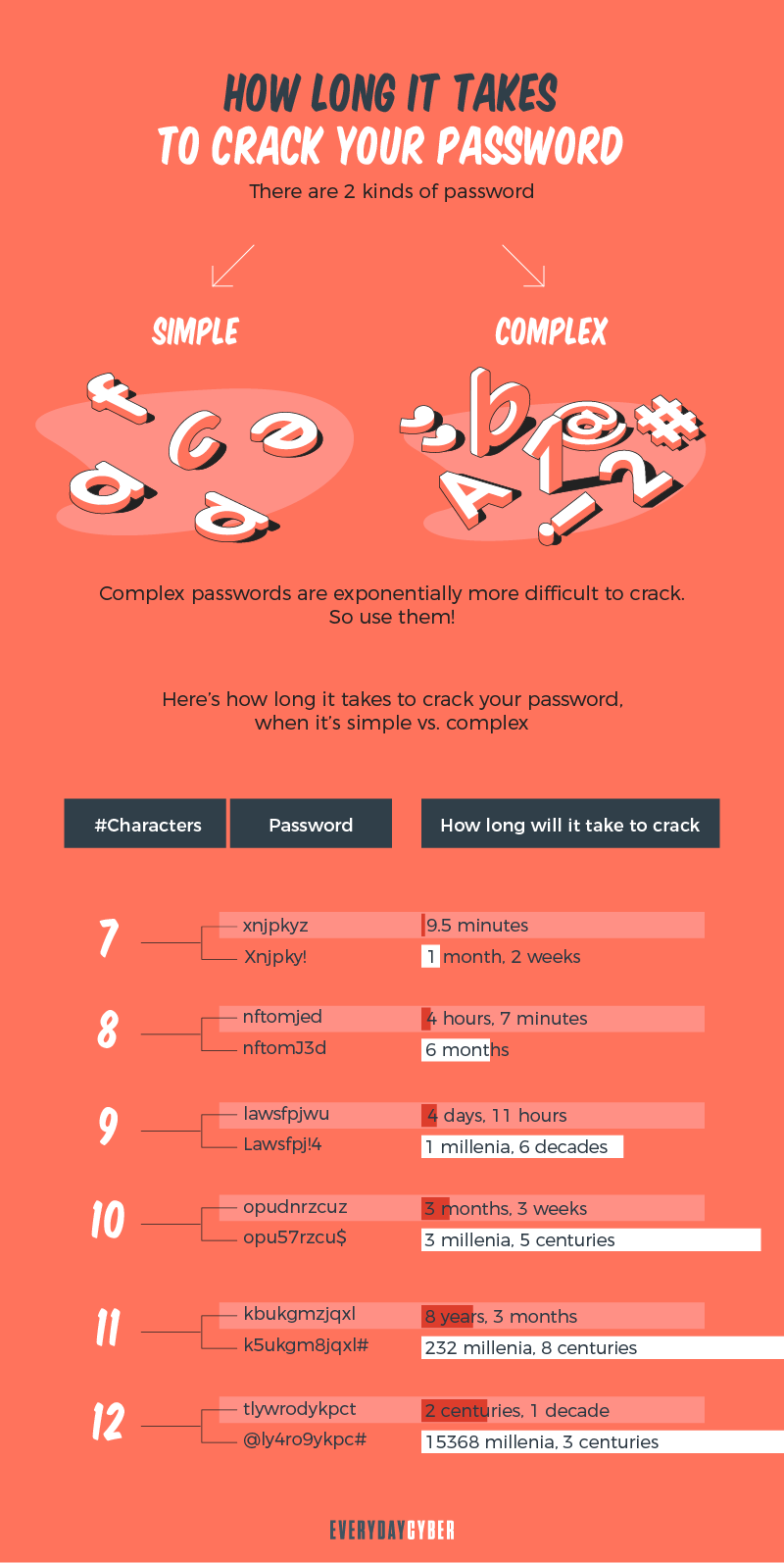
Passwords have long been used to secure online accounts. But have you ever wondered how long a hacker can crack your password?
Depending on the length and mix of numbers, upper case letters, lower case letters, and symbols that make up your password, a good hacker can get through your account instantly. With a complete mix of at least 10 characters, it may take years for your password to be broken.
Cybercrooks are getting better at their trade. They are always hungry for passwords. Passwords alone can no longer be a guarantee for online
Take the case of some of the biggest data breaches in history.
The Yahoo hack compromised three billion user accounts in two separate attacks in 2013 and 2014. MySpace, the once powerhouse social media site, experienced a leakage that resulted in the sale of 360 million of its user accounts on the dark web.
Add to that the 147.9 million victims of the Equifax breach in 2017.The eBay attack in 2014 is another disaster that exposed 145 million customer accounts.
Even giants with sophisticated
An extra level of
So what exactly is two-factor authentication?
Two-factor authentication is a
For more protection, you can add another level of
Businesses with highly critical applications and services may go further in their authentication processes by using a multi-factor system (MFA). This system involves not only two but three or more

Types of authentication factors
Authentication factors are the ways by which you can validate your online account to be able to access it. When you log in to your account, you normally enter your username and password. Today, as hackers keep pace with advancing technology, passwords, even strong ones, are becoming more and more vulnerable to hacking.
Thanks to 2FA, you can better protect your account with any of the following authentication factors:
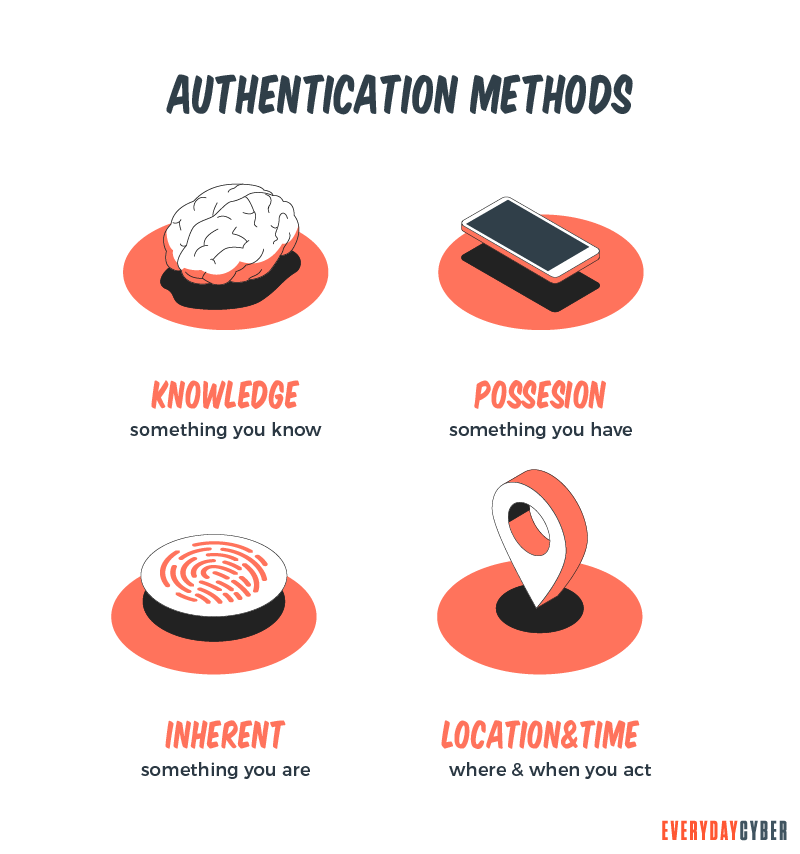
Possession factor
You can use something you own, such as a smartphone or laptop, to receive a one-time authentication code via SMS code or email. You can also use a bank/credit card to withdraw money from your bank account.
Other gadgets that can fulfill the function of 2FA are smartcards and physical
Inherence factor
This involves something inherent or unique in your physical self. It may be your fingerprint, voice or retina.
The downside of this factor is that fingerprint readers and facial recognition software may not always work on all phones. Only high-end phones, such as smartphones, that have biometric scanner capabilities may benefit from this type of factor.
Time factor
This is a time-based authenticator that controls user logins based on time. It permits access within a specific time window and restricts it outside that window.
Location factor
Companies that need to protect sensitive data may use an authentication factor denoted by the location from which the authentication initiative is being made. It works by limiting authentication efforts to specific devices in specific locations. This may include the Internet Protocol (IP) address or geo-location of the devices. A good example of a geolocation authenticator is the Global Positioning System (GPS).
Knowledge factor
The knowledge factor or something you know is the most common authentication method. It may be a password, personal identification number (PIN) or answers to certain secret questions. You usually use a password when you want to access your online accounts or a PIN when you want to withdraw cash using your ATM card.
Some expert opinions argue that two knowledge-based authentication factors don’t represent true
Real
- 2FA = Password + Device + OTP
- 2FA = Password + Device + Biometrics
- 2FA = Password + Device + IP Address or geolocation
- 2FA = Password + USB or Bluetooth
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
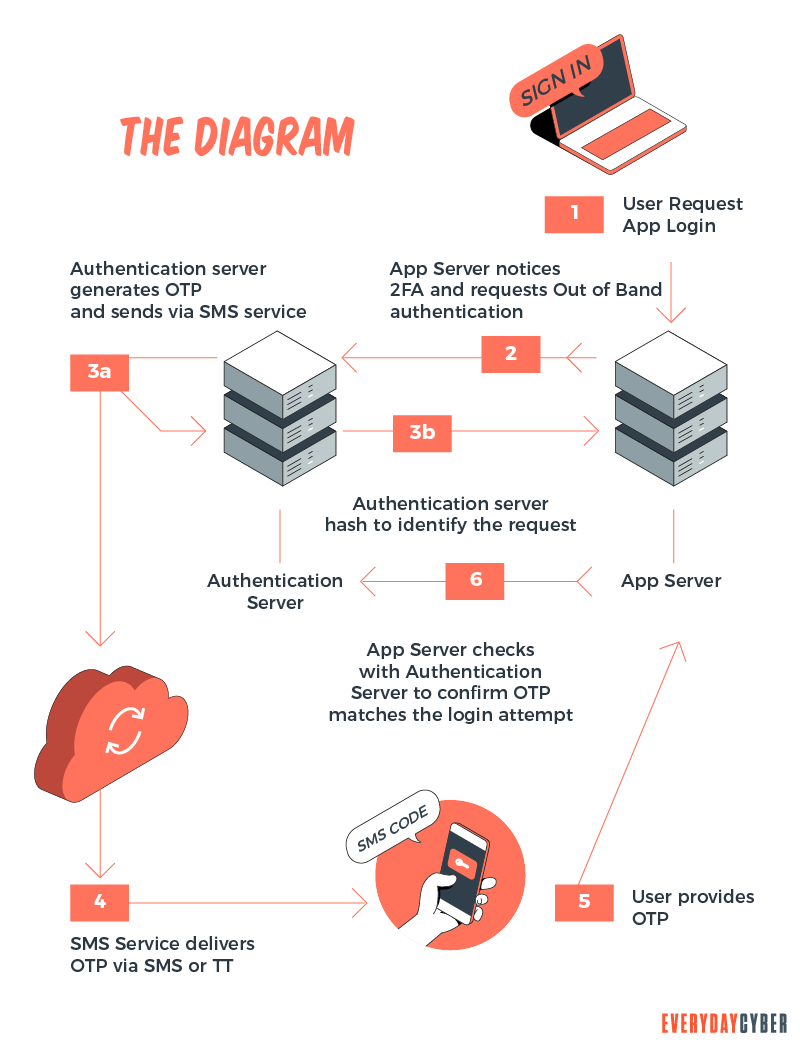
How does 2FA work?
Here are the basic steps when logging in to your account or site in a
- You’re asked to enter your username and password or use biometrics, such as your fingerprint, voiceprint, or iris scan.
- Once the site’s server finds your
identity , the second step usually involves the use of something you have, such as a mobilephone , USB, or computer to view your OTP. - You’ll then key in the OTP sent via your mobile
phone or email, or - In push-based authentication, you’ll get a prompt from your
mobile device to confirm if you’re logging in to your account, or - Use your
security key, such as a USB, NFC ( near-field communication device), or Bluetooth. - You’re now ready to access your account or the site.
Why is two-factor authentication so important?
Two-factor authentication is all about online
Usernames and passwords remain the most common forms of account authentication. While passwords provide some level of protection, they’re not foolproof. Hackers tend to revolve around weak passwords to gain access to online accounts.
In December 2017, researchers from 4iQ discovered a massive breach involving more than 1.4 billion clear text credentials that were circulating on the dark web. Weak passwords and password reuse across people’s email, social media, work, banking, and e-commerce accounts were the main culprits of the breach.
People that get more comfortable doing almost everything online are likely to open more and more accounts. Many of them tend to have lousy memories so they use the same password in all their accounts. The common passwords used were:

You can see a pattern that any amateur hacker can easily crack. However, if additional authentication factors are put in place, the attacker would face one more obstacle. It’s important to make sure that the factors are independent from one another so that the compromise of one does not lead to the compromise of the others. That is, use something you have, something you know, something you are, or somewhere you are.
Being secure is daunting. But the bad guys are waiting for you to get lax in protecting yourself online. While it may take a little longer to log onto a new device with a
Best authenticator apps
Authenticator apps provide better
Google 2-Step Verification
This Google authenticator app allows you to set up a 2FA by using the inherent
You can enter a password to access your account for almost any service. The app offers multiple options to enter the second step. If 2-Step Verification is on, Google Prompt will instruct you to tap on your
You may also opt to receive a verification code sent to your
As an added feature, you can visit your Google account
Microsoft Authenticator app
The app is available for iOS and
If you choose the authentication app, you have two options. You may sign in with a notification from the Microsoft Authentication app or a verification code from the same app.
You can also use alternative methods to sign in including any of the following:
- Use verification from my mobile app
- Notify me on my
mobile device - Text me at (your mobile number)
- Call me at (your mobile number)
- Sign in and sign out with another account
- More information
LastPass Authenticator
LastPass Authenticator features one-tap push notifications that allow you to sign in to select sites with a click instead of a code. This function also works with other third-party sites including Amazon, Dropbox, Facebook, Google, and Evernote.
The app can integrate with other sites that include LogMeIn Pro/Central, LogMeIn Rescue, GotoAssist, and Zively.
When a user logs in to a third-party site, the LastPass browser extension transmits a push notification to the user’s
Yahoo Account Key or 2-Step Verification
Look for the link to sign in on the upper-right hand corner of any Yahoo page. Go to Manage Accounts > Account Info and click on Account
If there’s a Yahoo app on your
After you’ve set up either the 2-Step Verification or Yahoo Account Key, you can generate a new unique password to access other Yahoo services with no direct support.
WhatsApp Two-Step Verification
Setting up the verification app starts by going to Settings > Account > Two-Step Verification. Tap Enable to create a six-digit PIN to enable you to register your
Instagram Two-Factor Authentication
Facebook owns Instagram. To set up the authentication app, go to your profile and click on the Hamburger menu on the top right. Go to Settings > Security and tap Two-Factor Authentication where you’re given two choices to get your authentication code:
- Via Text Message – Open Text Message and register your
phone number, including the country code. You’ll receive a confirmation code via SMS text message. - Authentication App – Since you can’t scan a QR (Quick Response) code with your mobile
phone when you’re using it to access the app, the app will teach you the process to set it up.
The app also provides five recovery codes to get access to other devices or to turn off
Twitter Two-Factor Authentication
To activate the Twitter authentication app, click the More Menu on the left hand portion of your desktop screen. Select Settings & Privacy > Account > Security > Two Factor Authentication. You then choose to receive codes from your
In the authentication app, Twitter will generate backup codes that you can use when you lose a device. It also provides one-time temporary passwords at devices or services where you can’t get
You can likewise use the Twitter app as your authentication app. Click the Login code generator to get a six-digit code that updates every 30 seconds.
LinkedIn Two-Step Verification
It’s relatively easy to activate or deactivate the LinkedIn Verification app. You can use SMS text or an authentication app. Start by going to Me Menu > Settings & Privacy > Account > Two- Step Verification.
The app will immediately provide you a six-digit code. You’re allowed to register only one
Twilio Authy
To set up the app, you’ll need to provide your
Authy’s redeeming feature is its encrypted cloud backup. But it may be risky to add the account to a new
Two-Factor authentication best practices
Strong passwords and PINs. Secure verification codes and devices. Multiple authentication factors. When combined with
We’ve put together a list of common two-factor authentication best practices. Read on to find out what works best for you.
Craft the right mix of authentication factors
Our world is plagued by cyber threats and the attacks are becoming more intense and more frequent. Strong passwords alone can no longer guarantee full
Security scientists have come up with additional layers of protection. SMS texting through
Your
The push notification technique is quicker and easier to use. It’s less vulnerable to phishing because it doesn’t need a passcode. Also, if the approximated location comes from an unusual area, your
Not all users are aware of a physical
These keys are relatively inexpensive and easy to install.
Can two-factor authentication be hacked? It’s possible, but if you use the right combination of factors and devices and add extra layers, the odds are low.
Secure your devices, gadgets, and tools
The widely used way of accessing services is through digital devices. The Internet of Things makes possible the interconnectivity of all things, such as:
- Smartphones
- Laptops
- Personal digital assistants (PDAs)
- Tablets
- Wearables
- Smart home appliances
- Medical equipment
- Business, banking, and financial systems
While these devices need to be intelligent, adaptive, and responsive, they should be fully secured. The healthcare sector, for example, is a critical area where
Other groups that can be impacted by unsecured devices are banking and financial institutions, online shopping and e-commerce businesses, government entities, and social media companies.
Always offer two-factor authentication option
A dependable two-factor authentication system starts with no less than two options. Don’t be complacent with employees and customers because any compromised device or malware from any of them could infect your whole network.
Some argue that it may be overkill to offer
Watch out for trends
Trends give us an idea of the general direction the market is taking during a specified period of time. While trends indicate what people like, you must be able to tell real trends from hype or fad.
As two-factor authentication becomes more popular, it’s likely that cybercrooks are likewise keeping pace. Cyber threats are increasing. Phishing and hacking are commonplace. But all these activities could create opportunities to refine your
What’s next after two-factor authentication?
It started with the good old usernames and passwords. Then came the passcodes, passphrases, TOTPs, OTPs, push notifications,
Today,
However, we’ve found out they’re not all foolproof. In some instances, it’s possible to deceive fingerprint sensors and facial recognition systems. Behavioral biometrics aims to further tighten
For example, you may have an inherent pattern in typing your password. If a bad guy learns your password but enters it differently, they may have a hard time accessing your account. Behavioral biometrics may also analyze the way you walk, the way you hold and touch your device, or the way you move the mouse.
We’re hoping specialized sensors, radars and locators may be able to do the analysis for us.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Password Manager?
A password manager is an encrypted storage system for keeping and managing passwords usually protected by a master password. Some password managers use biometric data to protect the vaults instead of master passwords. Still others support the use of two factor authentication for higher security.
What is a deep fake video and how to spot It
People can easily be fooled into believing they are seeing or hearing something that has no basis in truth in a culture filled with misinformation and deception. Deepfake videos have forced viewers to wonder whether or not what they are seeing or hearing in a video or audio recording is real.
A 10 Step Plan for Small Business Cyber Security
An effective cyber security plan outlines in simple language the best cybersecurity practices your organization needs to stay safe. It doesn't have to be complicated, but it should be pragmatic.
What is Digital Identity?
Your digital identity is your set of unique features and characteristics identifiable to you. It is all data that can be traced back to you.
What is Bloatware?
Preinstalled and unwelcome. Bloatware is unwanted software installed on your digital device; slowing it down, reducing battery life, consuming space and just destabilizing it.
What is Malvertising?
Malvertising is advertising malware that infects digital devices with malicious software using online ads and advertising networks as their delivery platforms.


