Pharming is when a bad actor (or “the pharmer”) re-directs you to a fake website instead of the legitimate one you intended to open. “Spoofed” sites capture your confidential information, including usernames, passwords, credit card data, or install malware on to your device. Pharmers usually focus on websites in the financial sector, including banks, online payment platforms, or other e-commerce destinations, often with identity theft as the ultimate goal.
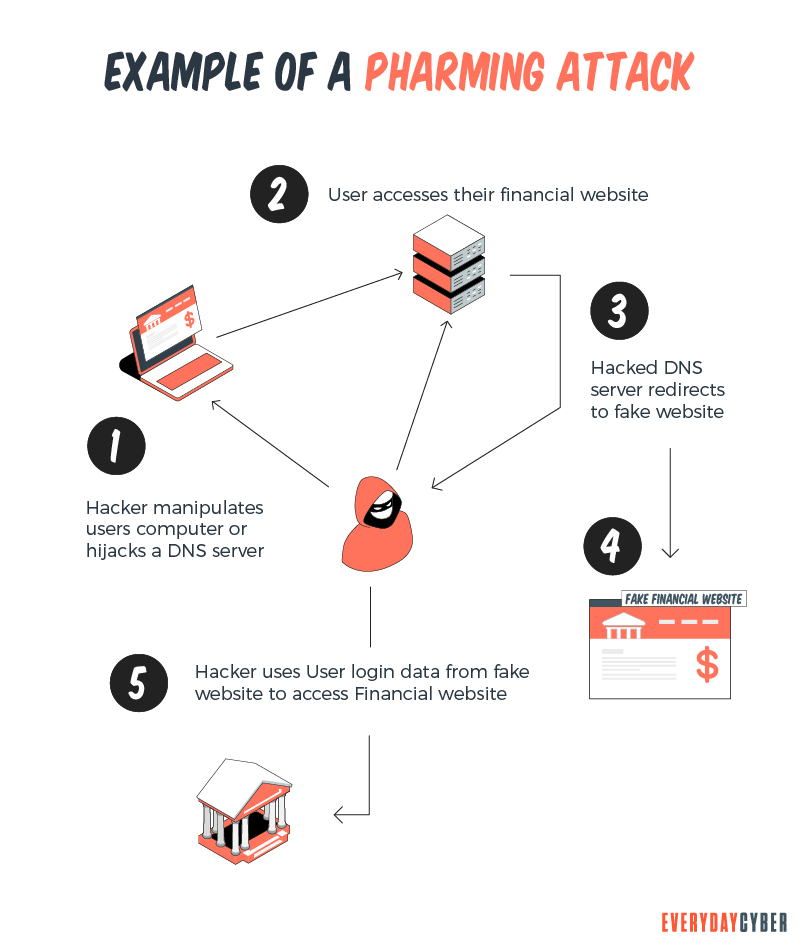
Pharming attacks have become effective because they fool you and your devices into thinking the spoof sites are legitimate. The pharmer tricks your device into sending you to the pharmer’s spoof website rather than the legitimate one.
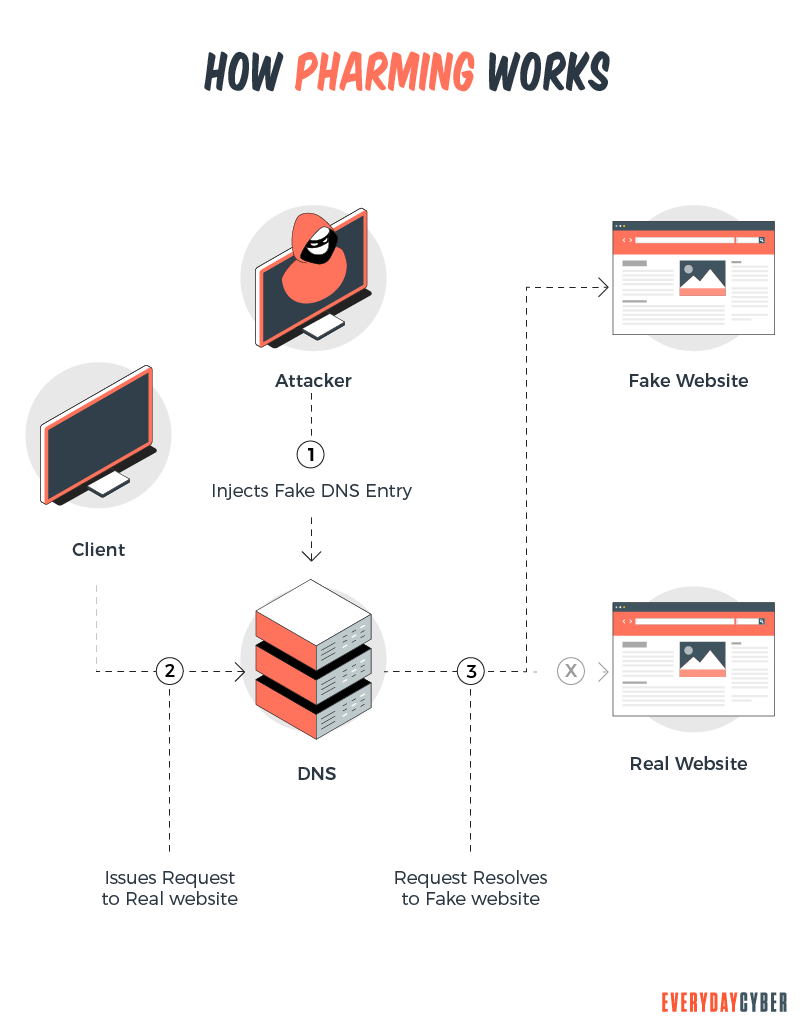
Here’s the general theme on how pharming works. When you navigate to a website, you will enter a website’s URL (e.g., www.abc123.com). This name is associated with an IP address – it is like your
To convert your URL name to its IP address, your web browser looks up the address using something called a DNS (domain name server). This of DNS as the yellow pages or the
Pharming comes in when the bad actors edit the
Don’t confuse Pharming for Phishing?
Often users think pharming and phishing are the same things? They are similar, but not the same. Phishing, as the name implies, uses bait to lure victims. Bad actors use official-looking or inviting emails or SMS messages to lure victims to visit spoofed websites and enter their personal information.
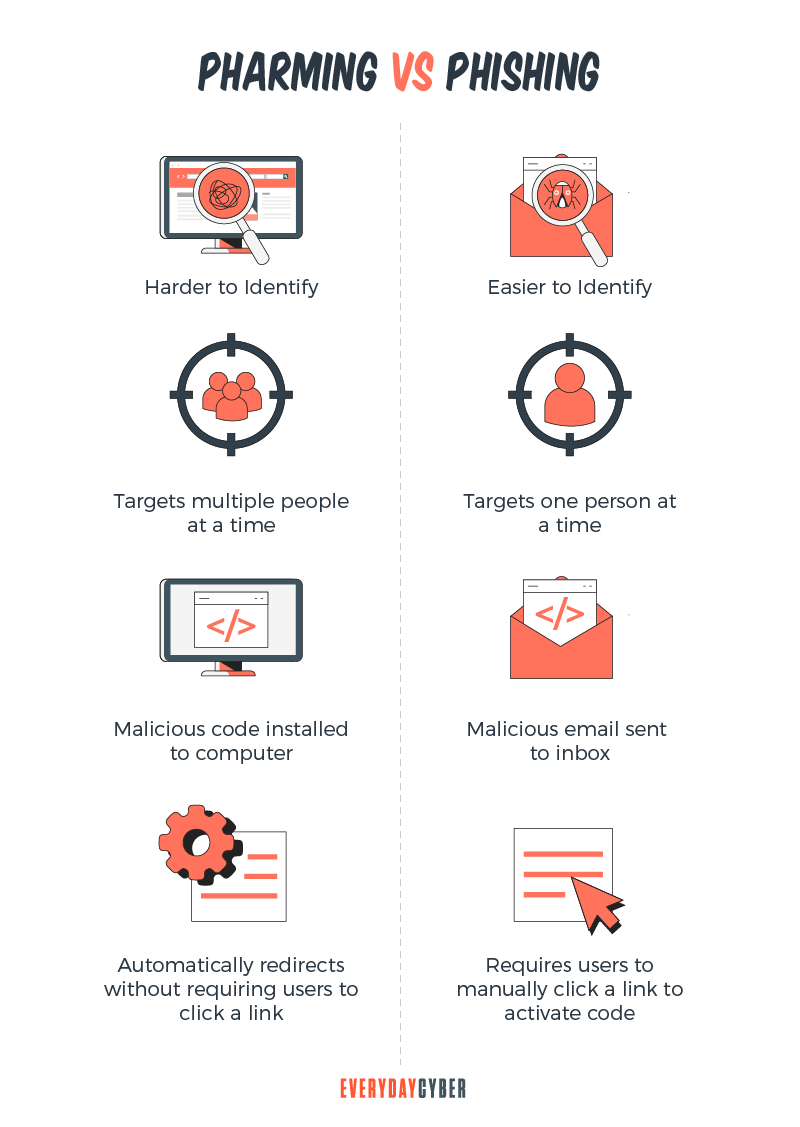
Pharming skips the bait step and sends victims directly to the fake website without your knowledge or consent. Because victims are typing the URLs themselves, they may be less likely to recognize the fraud rather than clicking links in a sketchy email. It’s a sneaker type of scam compared to more direct phishing techniques.
How to protect yourself against being Pharmed?
There are strategies you can use to protect yourself against pharming attacks.
- Use a trustworthy internet service provider (ISP) – Quality ISPs automatically filter out a pharmer’s bogus redirects, preventing you from ever reaching the pharming website.
- Watch URLs for typos – When going to a website, let it load completely, then examine the SITE closely. Pharmers often disguise their sites with minor spelling tricks, including swapped letters or letter replacements: “gooogle.com” instead of “google.com,” for example.
- Avoid websites that don’t use HTTPS – Sites using HTTPS have their websites encrypted. HTTPS sites encrypt communications so third parties can not intercept them. Websites with this enhanced
security level will automatically change their URL from HTTP to HTTPS, letting you know that your data is safe. - Avoid questionable websites – Use common sense and good judgment when browsing the web. Stick to websites you know you can trust. Avoid anything that looks suspicious.
- Validate websites before taking action – If a website doesn’t look like it usually does, or something seems off, you could be on a pharmer’s version. Click around a bit and make sure all the pages are present and accounted for. Look to see if the site has terms of service or privacy policy pages. Most Pharmers won’t bother going through the trouble to include those pages.
- Don’t click links or download files from unknown sources – Verify files and links before clinking. It hard for Pharmers to get you if they can’t install their malware onto your device.
- Avoid “to-good-to-be true” e-commerce deals – Many Pharmers will lure you in with significant price discounts compared to legitimate stores. Price-check on competing sites before making a purchase.
- Trust your
antivirus software – Pay attention when your browser or antivirus software warns you against navigating to a particular website. A warning may be an indication that it’s been infected since your last visit. - Get quality
antivirus /antimalware software – quality tools can make the difference between a good day and a bad day. Investing in a quality antivirus/antimalware toolset will be one of the best digital investments you can make.
“Check twice, click once – advice to live by”
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Computer Worm?
A computer worm is not a cute, squiggly little creature. It is an evil, malicious piece of software destined to wreak chaos and disaster on many devices.
What is a Rogue Certificate?
A rogue certificate is a valid certificate issued by a legitimate certificate authority. However, it’s untrustworthy because either it was compromised or was issued to the wrong party.
What is a Website Security Certificate?
A website security certificate is a digital certificate that asserts the identity of a website. It’s a virtual file approved by an industry-trusted third-party called a certificate authority (CA)
What is Hacking?
Hacking is an old game in the cyberworld with ever changing players and techniques. It may be done with good intentions or malicious motives. It is growing rapidly because of the proliferation of devices.
What is Spear Phishing?
Spear phishing is a targeted cyberattack to steal your information. You should be aware of the dangers of this and how to address them.
10 Cybersecurity Trends for Small Businesses in 2022
Knowing the latest cybersecurity trends spells the difference between keeping your business safe and opening it up to cyber attackers.