Spyware is simple: it’s software that spies on you. But knowing you have spyware on your device is anything but simple. This stuff is sneaky by design, running in the background, hidden from sight, or even operating in plain sight, but always collecting information and sending it back to its creator for dangerous purposes.
Spyware is generally not considered a virus because it doesn’t replicate like a computer virus. Also, where viruses may damage the device it installs onto, spyware is there to steal data. Data on you, your business, or any other digital asset or information it finds useful. It is one of the most dangerous types of malware circulating the internet.
How do I know if my device has spyware installed?
Generally, if spyware was only there to spy on you, you probably would notice it on your own. But bad actors tend to bundle spyware with other forms of malware – like trojan horses and adware, so things like your device slowing down, constant ad popups or unexpected tool bars or search boxes in your browser are a tell-tale sign that your device has been hit and likely has spyware installed.
What can Spyware do to me?
Spyware can collect financial information such as online banking account numbers, login passwords or credit card data. It can track your online habits and then deliver you more relevant ads. Institutions like governments can use it to collect all kinds of data on you. Spyware used by governmental institutions is also known as “policeware” or “govware”.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
What are the types of Spyware?
There are 4 commonly recognized kinds of Spyware.
-
- Adware: Displays unwanted advertising on your system.
- System monitoring: Software installs on your devices with the intent of monitoring all activity, including key presses (keylogger), video from your camera or audio from your microphone.
- Trojan Horses: Infiltrates your device with software that could take control over your device.
- Tracking cookies: Sends information about your shopping practices, searches and general internet behavior and sends it to a data aggregator.

What can different types of Spyware do?
-
- Steal stored credentials (user id, password, pass phrases, etc.) from a web browser, the operating system, or 3rd party applications. The stolen credentials will be collected by the spyware and transferred to the bad actor.
- Watch and record computer activity – this includes keystrokes, web and search history, communication logs (sms, email) as well as system credentials as they are being used to access internet sites, applications, etc.
- Take screenshots at scheduled intervals, making it easy to capture sensitive information shown on screen. They might also grab and transmit images, audio and video from the infected device.
- Specialized spyware, in the form of trojan horses will target financial institutions with the goal of collecting protected credentials. They search for vulnerabilities in browser
security to change web pages, modify transaction content, sometimes adding false transactions to mask activities, all while staying invisible to both you and the financial entity. They target banks, brokerage firms, financial portals, and even digital wallets.
How does Spyware get on my device?
To be effective spyware has to be installed on your device without your knowledge. Common pathways to spyware include:
-
- Passive download: If you click on an unfamiliar link or attachment in an email, you may trigger a download of an executable file. Even visiting a malicious website and viewing a page or banner ad can result in a “drive-by download” of spyware.
- Misleading marketing: Spyware creators will often present their spyware programs as useful tools and trick you into downloading them. Often Spyware is presented as an Internet accelerator, download manager, hard disk drive cleaner, or an alternative web search service. They convince you that you need the tool/product they are promoting but are just enticing you to download software whose primary function is to spy.
- Software bundles: Sometimes a genuinely useful software package may conceal a malicious add-on, extension, or plugin. These may look like necessary components but are spyware that tend to remain even after the chosen software bundle is uninstalled.
- Worms, backdoors, trojans: These items will often include spyware in addition to their primary malicious intent.
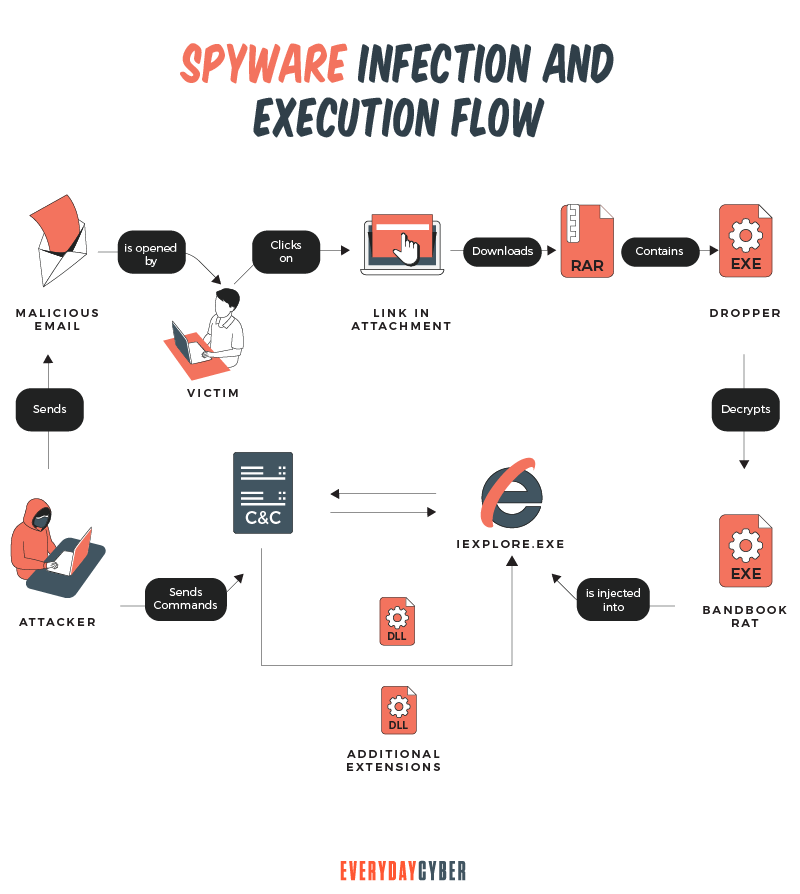
Do mobile devices get Spyware?
Smartphones are a significant target for spyware. Creators use all of the methods mentioned above for distributing their software plus they exploit public wifi (airports, malls), wifi hotspots (cafes, libraries, businesses), porous mobile operating systems, and app stores as platforms for distributing their software.
How to protect yourself from Spyware?
The best defense against spyware, as with most malicious software, begins with user behavior and is supported with
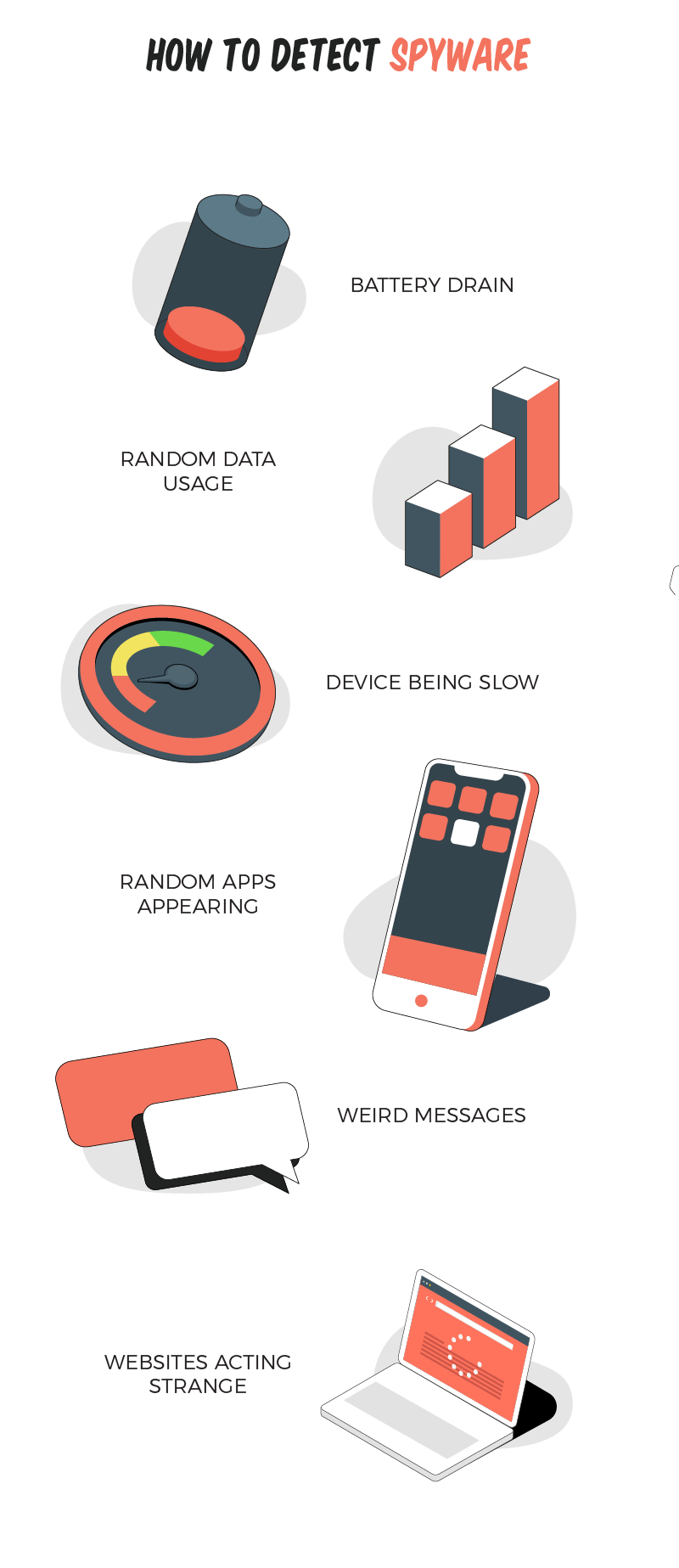
If you follow some simple best practices when you browse online, you’ll greatly reduce the chance of downloading any kind of malware, spyware included:
-
- Educate yourself. Understand how to identify emails and attachments from unknown or suspicious senders. Learn to be diligent about mousing over hyperlinks, to check them before actually clicking through.
- Don’t trust anything online: The hacker’s favorite trick is to create fake websites, pop-ups, or send phishing emails to try to dupe you into downloading a mysterious or misleading file. Don’t fall for it. If you aren’t 100% sure what the file is, or where the link goes, don’t click!!!
- Keep your eyes peeled: Make sure the websites you’re on are legitimate. Pay close attention to the URL to make sure nothing is misspelled, and confirm that you’re on an HTTPS site. It will help you avoid inadvertently downloading malware or experiencing a phishing attack.
- Consider an adblocker: Malvertising from infected banner ads can transmit malware onto your device even if you don’t click on it. This can affect even large, trustworthy sites, so your best solution is simply to block all the ads.
Install antivirus, anti-malware software onto your devices to help keep you safe when you connect to the internet
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Shoulder Surfing?
Shoulder surfing is a form of social engineering that enables cybercriminals to gather information just by looking over their victims’ shoulders. The aim of shoulder surfing is to obtain personal data, such as usernames, passwords or personal identification numbers (PINs), bank account numbers or credit card numbers.
What is Hacking?
Hacking is an old game in the cyberworld with ever changing players and techniques. It may be done with good intentions or malicious motives. It is growing rapidly because of the proliferation of devices.
What is a Trojan Horse?
Trojan horse computer viruses are malware disguised as or hidden in legitimate software. Hidden from view and ready to attack.
What is DNS Hijacking?
DNS hijacking is no laughing matter. It is a serious security threat that is consuming the cyber world. The critical role of DNS for network security has made a primary target for facilitating mass data theft.
What is a Potentially Unwanted Program (PUP)?
PUPs refer to programs, applications and other software downloaded onto computers or mobile devices that may have an adverse impact on user privacy or security. The term “potentially unwanted program” was coined by McAfee to distinguish the program from malware.
What is a certificate authority CA and what do they do?
Certificate authorities are the guardians of digital identity. They come in both public and private capacities. Certificates issued by them are trusted because information are validated from the requester’s own records and/or from third party sources.

