Viruses, worms, hacking, break-ins, denial of service attacks, ransomware, malware and many more are roaming the wide expanses of the Internet. Hackers are out there, always trying to find their way into our computers.
It takes only one careless click to compromise an entire network. And if that network is infected, the consequences can be damaging, most commonly in the form of:
- Information theft
- Business disruption or closure
- Revenue loss
- Equipment damage
Business closure is the most damaging, but information theft is the most expensive and fastest rising repercussion of cybercrime.
The scope, scale, speed, and frequency of cybercrime are far from abating. As digital technologies advance, they introduce new vulnerabilities faster than they can be secured. While the big players may have the resources to protect their systems, small businesses are most vulnerable.
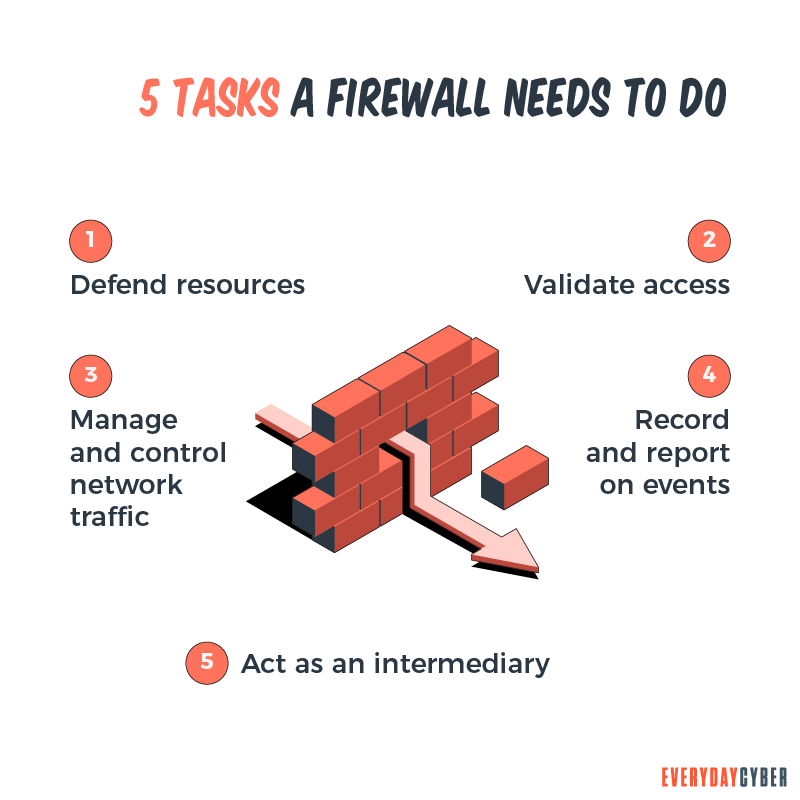
The first line of defense is a firewall.
What is a Firewall?
A firewall is a
What is the difference between a software firewall and a hardware firewall?
A hardware firewall is a physical device laid out between your computer and the Internet or other network connections. It has actual network cables connected to ports inside and outside the firewall. Many vendors offer it as a small office or home office router that has firewall features. It is a separate equipment that requires trained professionals to configure and maintain.
A hardware firewall is particularly useful as an additional line of defense by controlling the incoming network activity that passes through it. It examines the data that flows in from the Internet such as its source and location. It then compares the information gathered to a list of established permissions to determine whether the information should be allowed or dropped.
The main advantage of a hardware firewall is that it can protect all computers connected to it. Its major drawback is its inability to analyze information leaving your computer. You may need another layer of firewall for this, such as a software firewall.
A software firewall is a
One advantage of a software firewall over a hardware firewall is that it can monitor outgoing data traffic. It is also customizable so you can adjust it to meet your needs. One downside, though, is that it can protect only the computer it is connected to. You will need to install a firewall in each of your network computers.
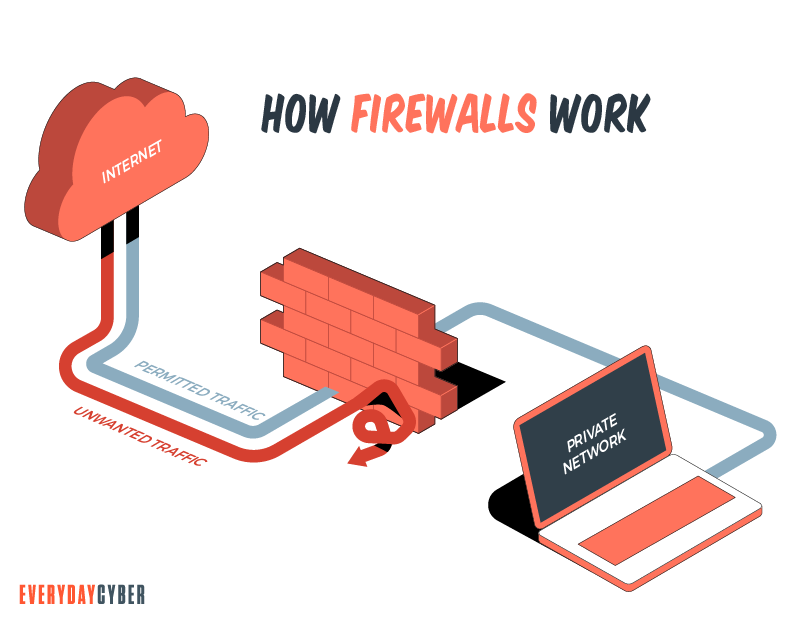
How a Firewall Works
The main function of a firewall from a
Packet filtering
Packet filtering is a standard means of defense against attempts from computers outside a local area network (LAN). During network communication, packets are filtered and matched with predefined sets of rules.
The filtering process involves checking the source, destination IP addresses and destination protocols. Some packet filters can memorize previously used packet information while some cannot. After matching, packets are either accepted or disallowed.
Proxy service
A proxy service is a go-between function done by a dedicated computer system or software between an endpoint device and a client requesting the service. It allows the client to connect to another server for easier access to files, Web pages and other connections.
A proxy service filters requests by applying strict routing rules to ensure that no dangerous traffic creeps in. When a request comes in, it looks for pages already cached and returns them to the client. If the page is new, the proxy service fetches the page for the client.
Proxy service has two main types. One is the forward proxy used to retrieve a range of sources. The other is the reverse proxy used particularly to protect and secure the server. It carries out tasks like authentication, decryption and caching.
Stateful inspection
This method does not analyze the contents of each packet but compares certain information to a cache of trusted databases. The firewall monitors specific defining characteristics and compares them with the incoming information. If the information provides a reasonable match, the request is accepted. Otherwise, it is denied..
Firewalls can also be configured..
If an identified IP address is reading too many files from a server, you can block all activity to and from that IP address.
Domain names are readable human names that all servers have on the Internet. You can configure your firewall to block certain domain names or allow specific domain names.
You can set firewall filters on certain protocols. They include:
- IP (Internet Protocol)
- HTTP (HyperText Transfer Protocol) for Web pages
- FTP (File Transfer Protocol) for downloading and uploading files
- TCP (Transmission Control Protocol)
- SMTP (Simple Mail Transport Protocol) for sending text-based information such as emails
- ICMP (Internet Control Message Protocol) for collecting system information from remote computers
- Telnet for performing commands on remote computers
You can also configure your firewall for certain specific words and phrases, such as obscene, vulgar, swear or offensive words. For example, you could set the firewall to block any packet with the words “asshole”, “piss off”, “son of a b*tch”, etc. and include as many variations as possible.
A common guideline is to block everything. But that defeats the purpose of having an Internet connection. So you will need to select what types of traffic you will allow to specific users depending on your needs.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
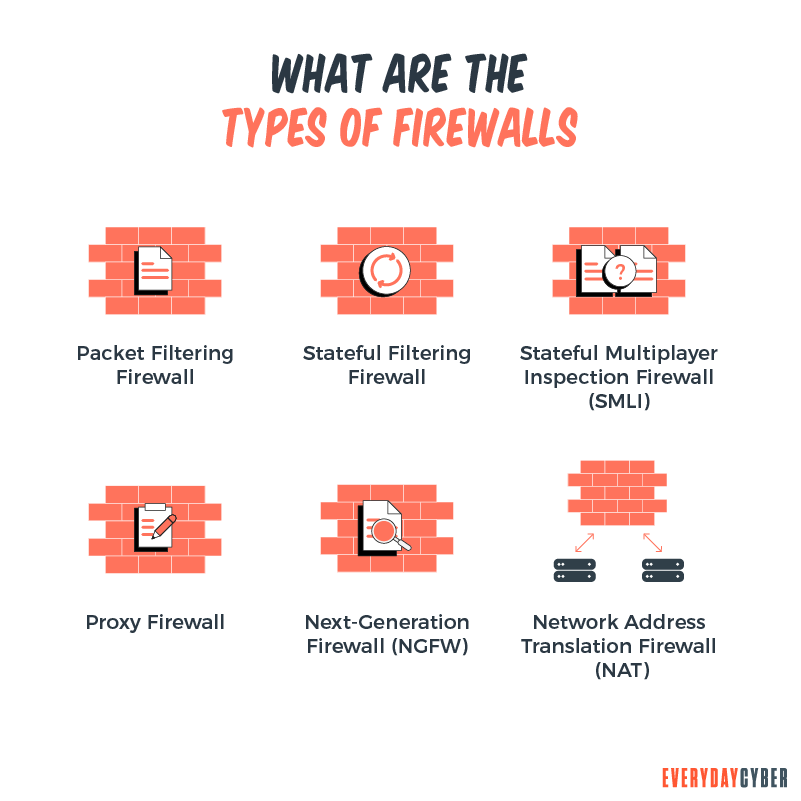
6 Types of Firewalls
Firewalls are classified according to functionality. Here are the most common types:
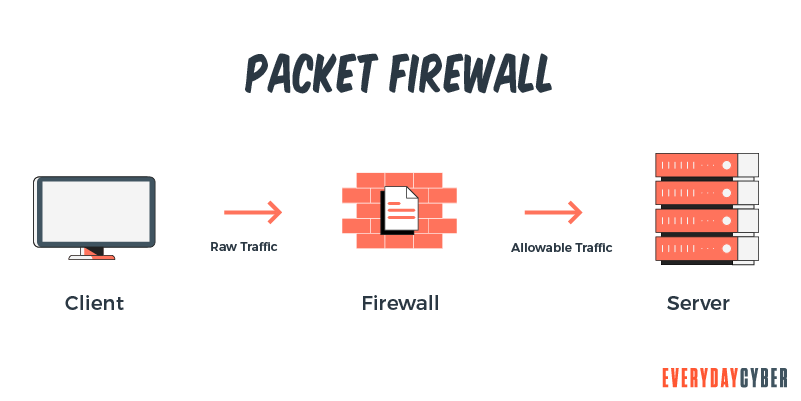
1. Packet filtering firewalls
Packet filtering involves checking all data packets coming from the network server. The firewall inspects pre-established specifics such as the source and destination IP addresses, protocol, port number and other available data.
These firewalls provide only basic protection and are vulnerable to being bypassed because they are not resource-intensive.
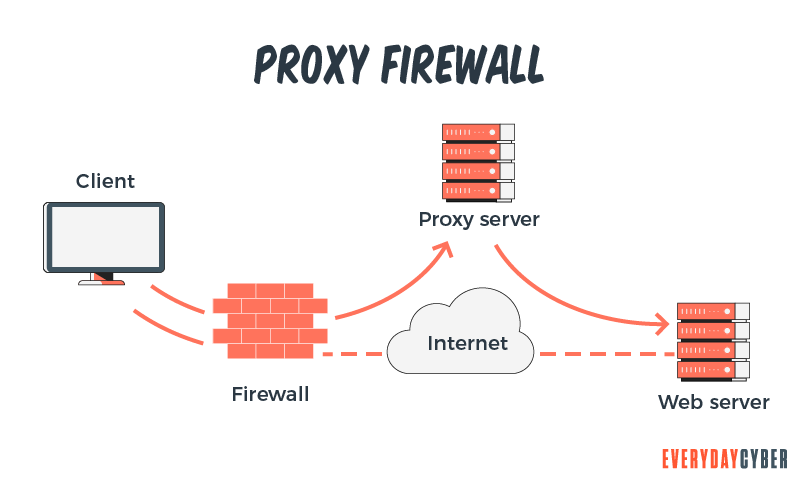
2. Proxy firewalls
Also known as application level firewalls, proxy firewalls work at the application level. They prevent outsiders from directly accessing your internal network. They analyze the content of data packets against a set of user-defined rules. Since a proxy firewall is essentially an added barrier between the server and the client, it can cause considerable slowdowns.
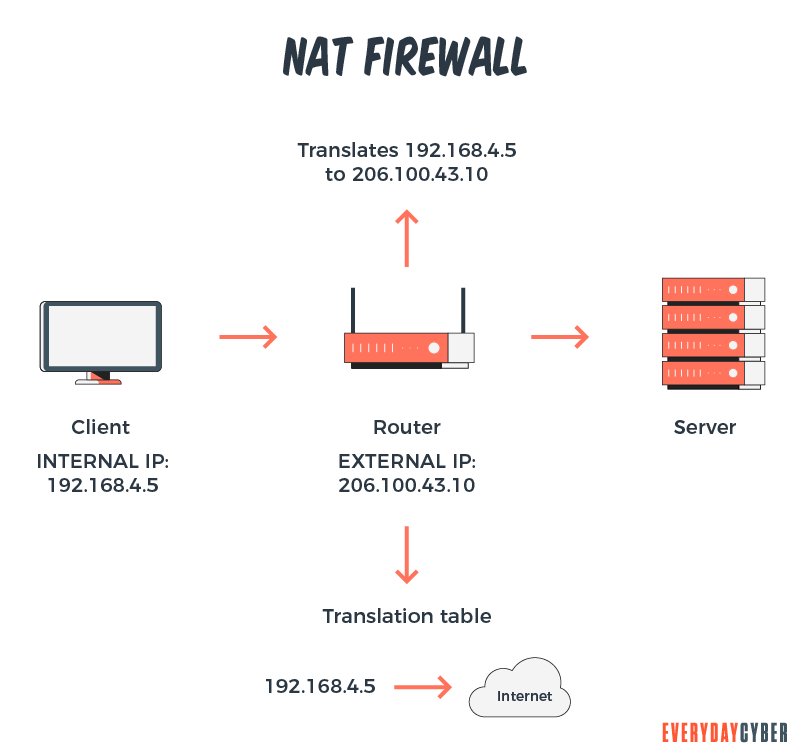
3. NAT (Network Address Translation) firewalls
NAT firewalls work by assigning a public address to a group of computers inside a private network. They hide the individual IP addresses to prevent hackers from finding their way into your network. They block unsolicited communication and only allow inbound web traffic if a device in your network requested it.
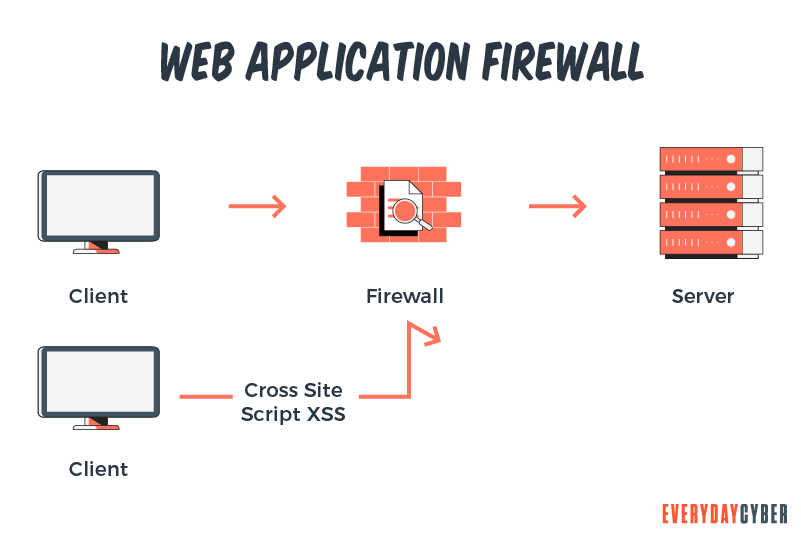
4. WAF (Web Application Firewalls)
A WAF takes care of filtering and blocking data packets as they travel in and out of websites or applications. A WAF can reside either on the network, at the host or in the cloud. WAFs are available as plugins, network appliances or cloud services. They are similar to proxy firewalls but focus more on defending the application layer against attackers.
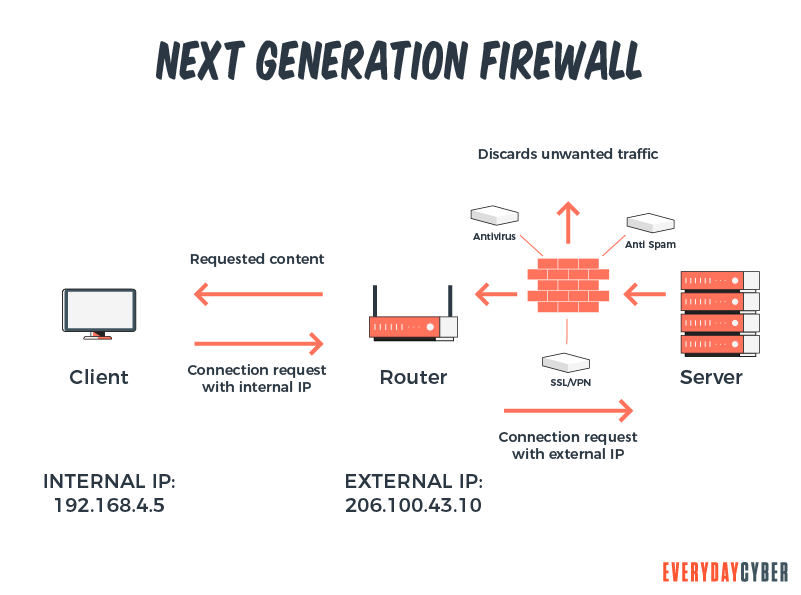
5. NGFW (Next Generation Firewall [10]
NGFWs provide capabilities beyond traditional firewalls. They offer additional functions such as:
- Breach prevention and advanced
security - Comprehensive network visibility
- Flexible management and deployment features
- Fastest time to detect a threat
- Automation and product integration
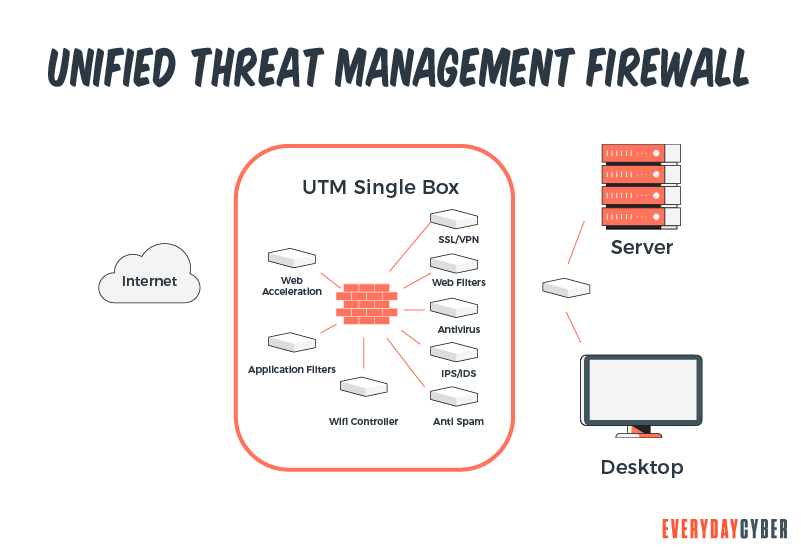
6. UTM (Unified Threat Management) firewalls
UTM firewalls are single
- Antivirus
- Anti-spyware
- Network firewalling
- Intrusion detection and prevention
- Content filtering
- Leak prevention
- Remote routing
- Network address translation
- VPN (Virtual Private Network) support
What Firewalls Cannot Do
There are malware threats that firewalls cannot prevent. These threats are usually caused by human-initiated activity..
Stolen laptop or device
Data theft or leakage are potential problems that can arise from stolen devices especially when sensitive data is not encrypted. In most cases, passwords are not enough. We recommend the use of multi-factor authentication to provide much better
Phishing and pharming
Phishing happens when you click on malicious email attachments and links. You could be unwittingly giving away sensitive information such as your bank account password or credit card details.
Pharming is a phishing variation where criminals set up fake websites that look like those you normally use. Once you enter your credentials, they can gain access and potentially ransack your account.
Viruses, worms, and trojans
These malware threats cause annoying symptoms ranging from the slowing down of your computer to the more serious risk of your equipment malfunctioning or being damaged. It can mean great losses for your business or, worse, closure of your business.
SPAM
SPAM is another common danger not covered by your firewall. SPAM often contains viruses and phishing emails that can affect business productivity. SPAM can come from malicious emails, websites that have been hacked and injected with virus or flash drives that have been also infected.
Spyware
This form of threat gathers information about you. It can spy and record everything you do on your computer that can potentially destroy your reputation. Often, hackers make money out this scheme by demanding ransom.
10 Firewall Best Practices for Businesses
Your network firewall is your most essential
We have compiled firewall best practices that you may consider to protect your network from present and future danger.
1. Set up your firewall properly
The details of firewall deployment may differ depending on your network needs and the vendor you have chosen. But there are general practices that apply to all systems such as the following:
- Protect your firewall. Delete all default accounts and passwords and create new passwords that are strong. Change passwords as often as possible.
- Group similar assets together. Design your network so that similar firewall zones and IP addresses are each grouped depending on their function and data sensitivity. For example, servers accessed through the cloud are grouped together while internal servers should have their own group.
- Streamline your firewall rule base. This means clearing your rule base of obsolete, redundant, conflicting or vague rules.
2. Use a least privilege policy
Create firewall rules that are as tight as possible when matching data and permitting traffic. Only allow traffic that is permitted by your company
3. Monitor user access
It is advisable to limit access to some specific traffic to certain services and applications. User permission is necessary to ensure that only authorized staff have access to firewall configuration change. Each and every access must be recorded in a log for audits and compliance and to detect any unauthorized configuration changes..
4. Create a firewall configuration change policy
You will need to update your firewall configuration as the needs arise to ensure that your firewall is strong and can protect your network from new threats. Your firewall configuration plan should include the following factors:
- Definition of the required changes and their objectives
- List of the risks that may result from the change, its impact on the network and a plan to minimize the risks
- Proper audit trails on who made the change and the reason for and location of the change
5. Watch out for firewall software updates
And do it regularly. Updates involve minor changes in the firewall software to address new potential
6. Use a firewall monitoring system
A comprehensive firewall monitoring system helps you track the performance of your firewall. Your firewall capacity increases as your company grows. This means more traffic as more packets are accepted and dropped every second. You don’t want to overload your firewall so keep monitoring.
7. Automate manual tasks
Maintaining firewalls is tedious and time-consuming. You may also need to do firewall-related tasks like enabling and disabling various features, deploying new services, validating configuration and maintaining high availability. Keeping up with these activities is labor-intensive and people doing the tasks are vulnerable to error.
Automation can replace many of these tasks. It can run commands and identify issues to assess the health of your firewall system. Network automation also helps reduce costs and while providing more accurate information on performance.
8. Manage your firewalls centrally
If you have multiple firewalls from multiple vendors, use a centralized management tool to ensure that all are functioning. This tool allows you to have a unified view of your whole firewall network, policies and rules. It also enables you to compare the systems and determine which are performing better.
9. Do regular firewall configuration and security audits
It is important to do configuration audits to find out if there is redundancy or failover and to ensure that no firewall becomes a single point of failure.
Security audits are also important for compliance with company and external
10. Conduct regular cyber security training
Quarterly or semi-annual training doesn’t work anymore. Your
It would be a good thing to continuously train them on basic
- Data
security best practices - Firewall
security best practices - Incident response plans
- Password management
- Updates on new malware, among others
In conclusion, whether you own a computer or a network of computers, firewalls provide the first line of defense against
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
Is Cyber Security Awareness Training Critical for SMBs?
You might think that cyber security awareness training is not for small businesses. You might also think that the bad guys are more interested in bigger companies. You probably should read this because you would be wrong on both counts.
The #1 Cyber Threat Small Businesses are Facing
Phishing attacks are the most widespread and most damaging threat to small businesses, accounting for 90% of all cyber security breaches.
What is Typosquatting?
Cybercriminals target visitors that accidentally mistype website addresses directly into their browsers. They use typosquatting, also called URL hijacking, to deceive visitors and lead them to malicious sites they themselves have set up.
Do You need to Conduct a Cyber Security Risk Assessment
Small businesses experience cyber security risks in varying forms and sophistication every day. Being complacent about the risks and ignoring the importance of a cybersecurity risk assessment can damage the health of their businesses.
What is 256 Bit Encryption?
256 bit encryption has quickly become the industry standard for ensuring security of your data, security of your communication and is really now minimum encryption level for securing your digital environment.
Things About Ryuk Ransomware You Need to Know Right Now
Ryuk ransomware is one of the most dreaded malware to date. It encrypts or steals corporate data to extort millions of dollars from its victims. The Covid-19 crisis greatly influenced the recent rise in ransomware. The remote work response to the pandemic created huge gaps in the worlds cyber defenses. Threat actors saw these vulnerabilities as opportunities to spread large-scale ransomware attacks.


