You’re in rush hour, traffic is moving at a decent speed. You’re under an overpass. On the other side is the onramp from a cross street. Additional cars enter at a rapid pace onto the freeway. The number of vehicles entering the freeway increases quickly and the freeway slows to a crawl. It comes to a complete standstill. Now you’re stuck. Everyone on the freeway is stuck. You cannot move.
A DDoS attack is like this, except the freeway is the website you want to visit. It’s overloaded with traffic. It stops working and everything grinds to a halt. The difference with a DDoS attack is it’s happening on purpose.
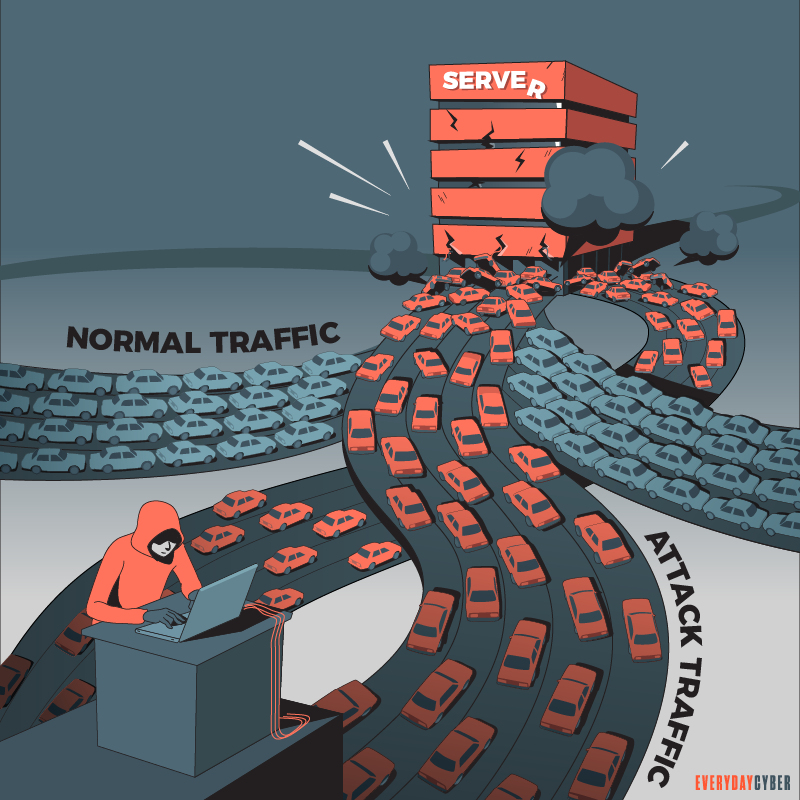
When you see reports about a website being “brought down by hackers,” it often means it has become a victim of a DDoS attack.
So what is a DDoS (Distributed Denial of Service) attack?
DDoS stands for Distributed Denial of Service It’s a coordinated attack intended to crash websites or online systems by overwhelming them with data. Attackers initiate DDoS attacks for various reasons including
- political revenge
- online activism
- young hackers just causing havoc
They can result in minor annoyances for users or long-term downtime for businesses and, in the worst cases, cause severe economic harm.
Most cyberattacks, such as ransomware, generally produce a financial return for the cybercriminal. DDoS attackers, on the other hand, focus primarily on being disruptive and annoying.
An example of DDoS attack is the one launched against World of Warcraft. The attack took the game down, affecting thousands of gamers for hours. But the attackers didn’t make any money off the attack. They simply did it to cause pain.
How Do DDoS Attacks Work?
The strategy behind DDoS attacks is fairly simple. Overwhelm a website or online service.
Attacks can range in their level of sophistication but the basic idea of a “denial of service” is to flood a website/service so that it becomes inoperable.
A DDoS cyberattack targets components of a website/service, such as the webserver, the network router, firewall, etc., with various types of requests and overwhelming volumes of data so the targeted site or system crashes.
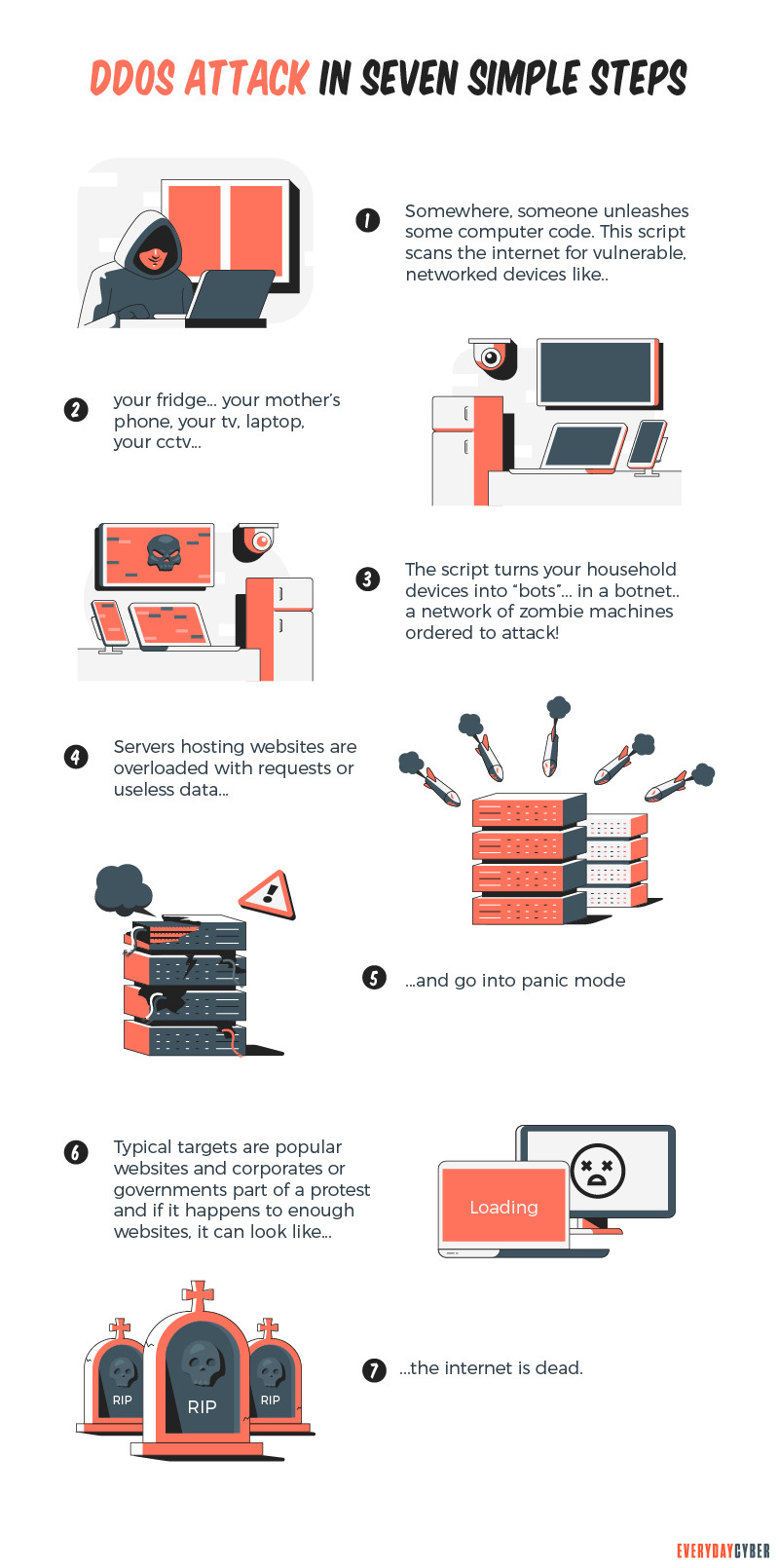
DDoS attacks require an army of devices to generate the level of traffic necessary to overwhelm a website. To make this happen, cybercriminals use botnets that consist of tens, hundreds, or even millions of devices spread across the internet.
Botnets are networks of devices that are infected with malware and are activated when the DDoS attack begins. These devices act as bots. They execute commands to generate the desired network traffic and service requests that ultimately overload the targeted website.
Botnet devices could be laptops, desktops, phones, IoT devices, even printers. Before a DDoS attack, the bad actors infect devices with the botnet malware using a variety of methods: viruses, worms, trojan horses, phishing emails, etc. Once infected, these devices can then participate in a DDoS attack.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
What are the Types of DDoS Attacks
DDoS attacks typically fall into one or more categories, with some sophisticated attacks using multiple approaches. These categories are:
Volume based attacks
They send massive amounts of traffic to overload a network’s bandwidth.
Protocol attacks
They exploit vulnerabilities in network devices or servers.
Application attacks
They target web services and web applications primarily and are the most sophisticated form of DDoS attack.
Best Options for Protecting Against DDoS Attacks
Unfortunately, protecting networks and online services from DDoS attacks can be a difficult task. Companies need to build a plan to defend and mitigate such attacks.
The first part of that plan is determining what the company’s vulnerabilities are. This will then determine what the protection protocol will need to be.
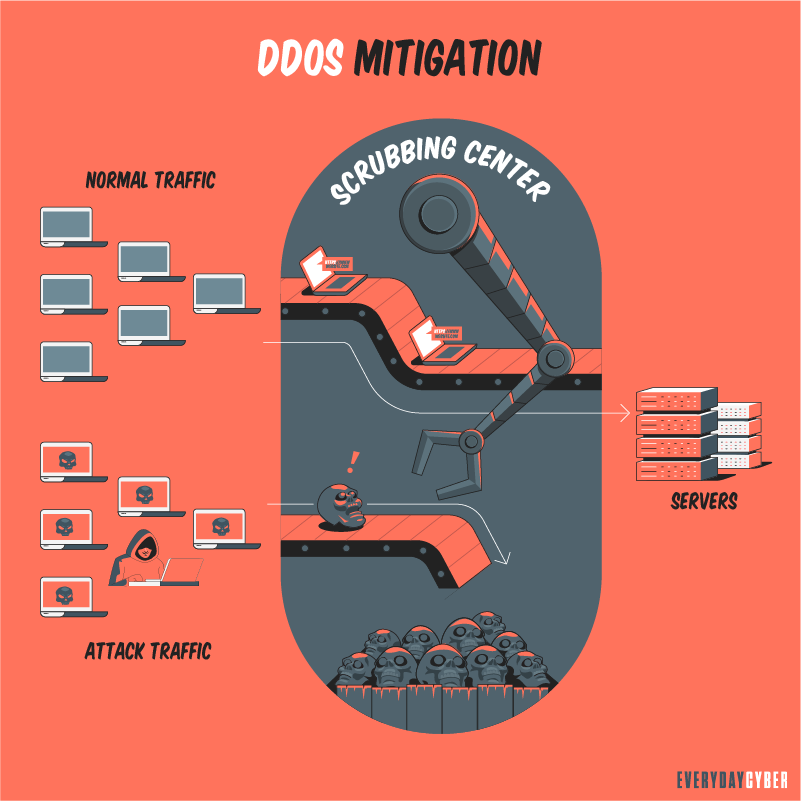
In general, the protect protocol will need to focus on two capabilities:
#2 So here we are at the middle of the post. We still think it's a good idea to signup.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Quick action response
Identifying a DDoS attack early improves the ability to contain or mitigate harm. Advanced networking technologies and anti-DDoS services can help recognize abnormal spikes in traffic. In other words, they can thwart a possible DDoS attack.
But if an attack is already happening, the best defense is to engage your ISP ASAP to re-route traffic. This is particularly useful if the ISP supports Black Hole routing, which directs all DDoS traffic to a null destination.
You should also consider a backup ISP to which services could be redirected. This can help keep the website up even under the DDoS threat.
Also, consider services that disperse the massive DDoS traffic among a network of servers to render the attack ineffective.
Active Network devices (firewalls and routers)
Network devices, such as firewalls and routers, are the first line of defense.
Modern networking devices support configurations that will reject bogus traffic and become an active participant of a company’s defensive position against DDoS attacks.
It is critical to maintain all network devices and keep them up to date with the latest operational and
How to Prevent Your Devices from Participating in DDoS Attacks
DDoS attacks are best defended at the source. Unfortunately, the source falls on users, whether they’re individual consumers, corporate users, or companies themselves.
While there are cases where malware (specifically botnet malware in the case of DDoS attacks) can be deployed without someone downloading them, the vast majority of attacks happen because of human error, such as:
- visiting unsafe web sites
- hovering over popup ads (drive-by-download)
- clinking links in phishing emails
- not maintaining devices with current
security patches
To defend your business against a DDoS attack, the best strategy is to apply basic cyber
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Social Engineering?
Social Engineering in the digital world is the intentional deception and manipulation of victims to cause the release and sharing of confidential information used to commit fraud and other cybercrimes.
What is a Hacker?
A hacker is someone who challenges technology to see if it can be compromised. A hacker can black hat or white hat.
5 Powerful Ways to Protect Your Business from Vishing
Vishing is a cybercrime that’s threatening people all over the world. And it’s not expected to go away anytime soon.
What is Whaling?
Whale phishing is a targeted spear-phishing attack in which cybercriminals impersonate the high-level executives of an organization to send messages to lower-level company administrators in a position to do the acts being requested by the criminals on two things they want most -- money and data.
What is 256 Bit Encryption?
256 bit encryption has quickly become the industry standard for ensuring security of your data, security of your communication and is really now minimum encryption level for securing your digital environment.
A Step-by-Step Process for Creating an SMB Cybersecurity Plan
Failing to plan is a plan to fail. The vulnerability of your small business's digital infrastructure is dramatically increased without a sound cyber security plan. Business plans help achieve desirable outcomes. You don't want to be a cyber attack victim, so build a plan.

