For most people, the term “hacker” or “hacking“ has negative implications. They see images of young individuals in hoodies bent over computer keyboards doing evil deeds.
Get up to $105 off McAfee Total Protection – Includes premium antivirus, identity protection, and Secure VPN!
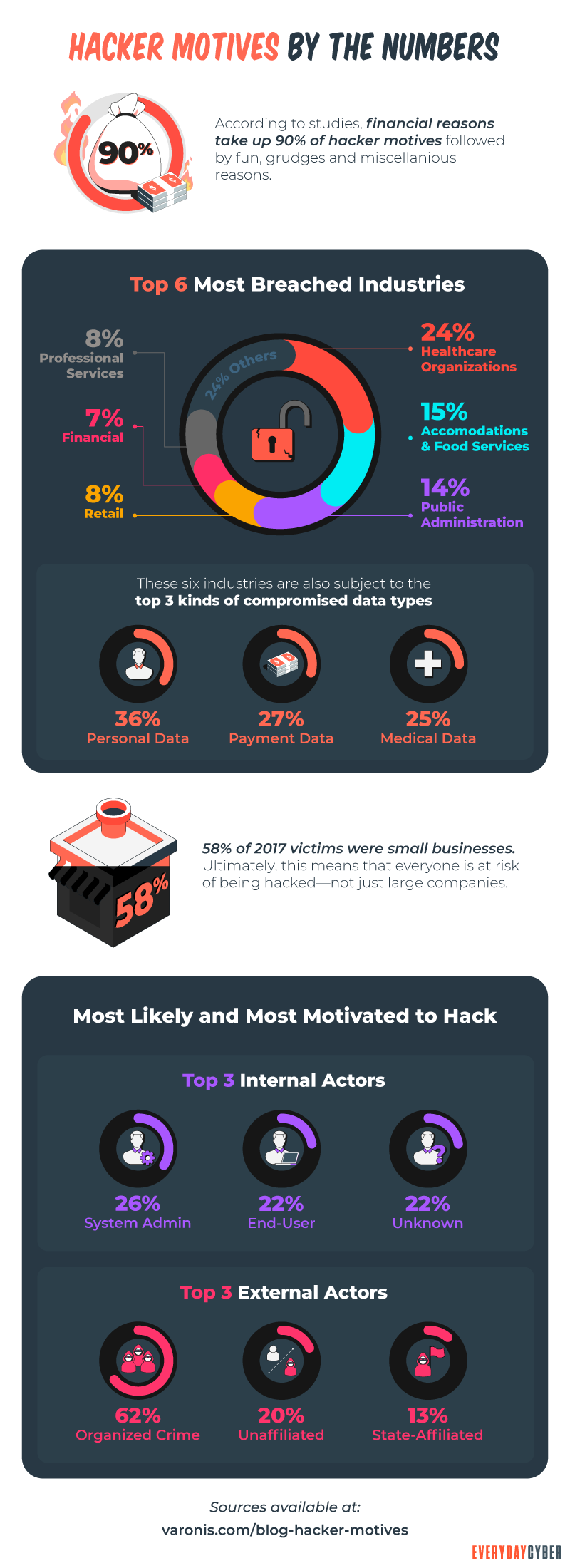
Yes, hacking and hackers have generally been associated with compromising computer systems, networks, and digital devices. But those activities are not always done with malicious intent. Hacking is really just challenging technology to see if it can be bypassed, broken, infiltrated, or compromised.
So what is a hacker? Based on the previous description, a hacker is one who leverages technical skills and knowledge to solve a problem or challenge, sometimes using unorthodox approaches. By that definition, there is really nothing inherently evil about hacking.
The Three Types of Hackers
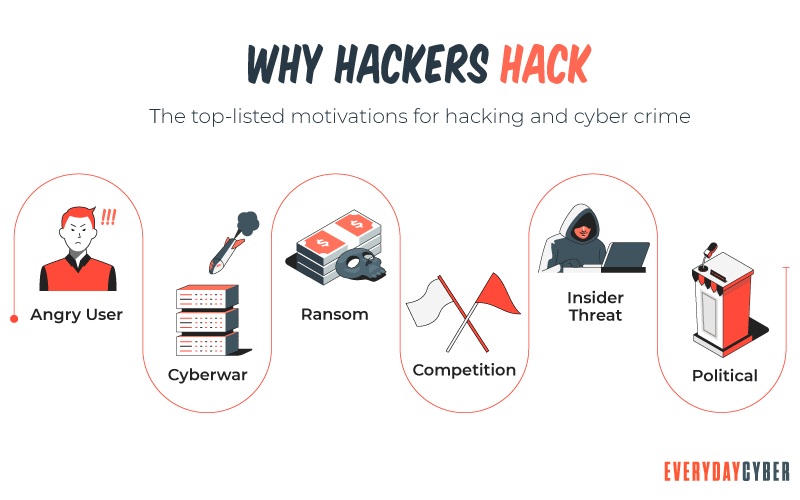
Hackers come in multiple colors and are motivated by a number of reasons.
Criminal hackers create malware to commit crimes, such as stealing information and money. Good hackers use their skills to test systems to expose vulnerabilities so that they can be fixed so criminal hackers can’t exploit them.
Criminal hackers work for themselves, criminal organizations or nation states. Good hackers typically work for big companies or governments to protect those entities from the bad actors.
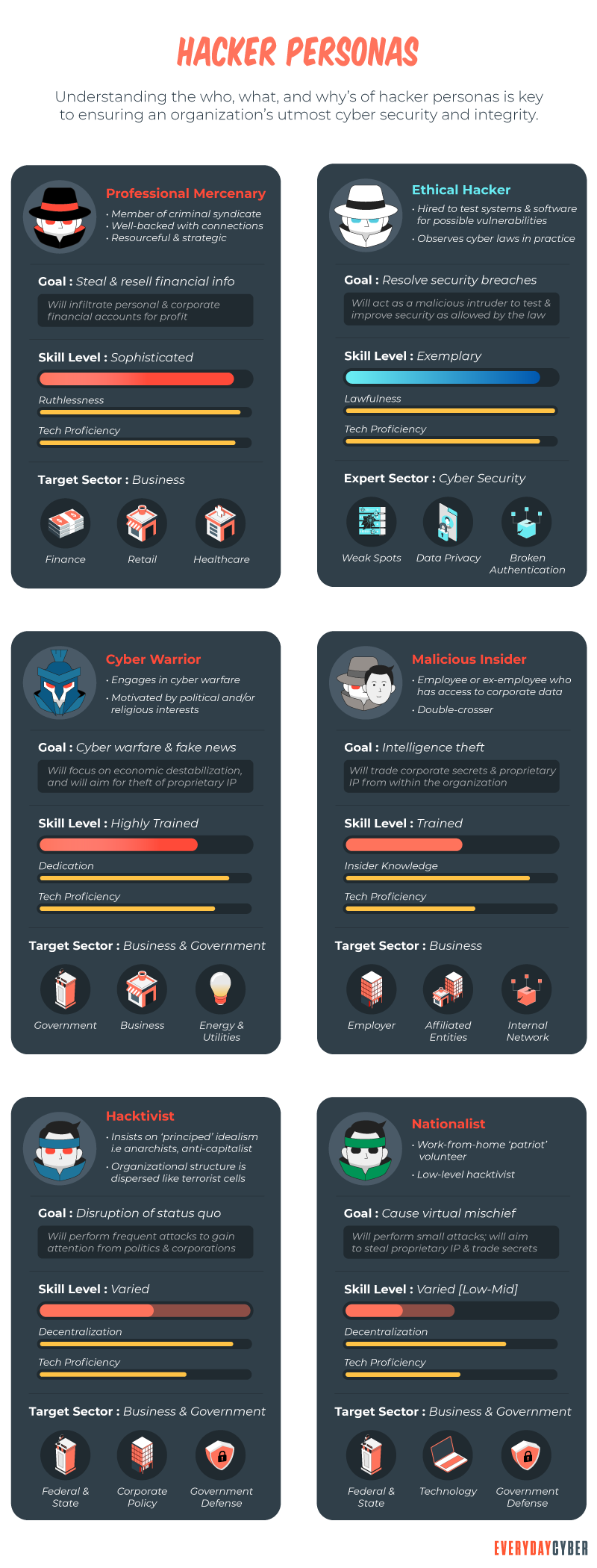
The industry groups hackers into three primary categories: black hat, white hat, and gray hat. There are other variants of hackers but these are the most common definitions.
Black hats
These hackers gain unauthorized access into computer systems or networks with malicious intent. They may use technology to attack systems for fun, for profit, or for political motivations. They could also use it to destabilize countries or as part of a social cause. Black hat system penetration often involves modification and/or destruction of data and distribution of computer viruses, Internet worms, and spam.
White hats
Generally known as “ethical hackers,” they are computer
Grey hats
As with the color, these skilled hackers operate in the grey zone, sometimes with good intentions and sometimes not. They are a hybrid between white and black hat hackers. They usually do not hack for personal gain or have malicious intentions, but may or may not occasionally commit crimes during the course of their technological exploits.
A hacker is generally used to refer to any individual who deliberately tries to compromise a computer system—regardless of objective. Or it can also refer to someone who likes to tinker around with the innards of computer systems, and it may also mean a smart person who can solve any computer problem.
So, while many in the mainstream may think of hackers as criminals, the term describes a range of people with different technical skills and motives. It’s important to use qualifying descriptors, such as “white hat hacker” or “criminal hacker,” so we have a better idea to whom we are referring.
Hackers are usually very talented people We just need more of the good variety, the white hats.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
Why every small and medium business needs a cybersecurity strategy
A truck full of security studies show nearly every small businesses has exposed data and poor cybersecurity policies. Either build and execute a cybersecurity strategy or expect to be a victim of cyber crime. Be prepared, be proactive, and be safe.
What is a VPN?
A VPN is a virtual private connection to a VPN host server to hide your identity, address and online activity when using a public Internet connection. It does this by encrypting your data and turning them into “rubbish” so no one can make sense of it even if they get their hands on it.
What is a Botnet and How to Protect Your Business from One?
A botnet is a network of computers that work as a collective to infiltrate your device. Here's how to protect your business from botnets.
10 Cybersecurity Trends for Small Businesses in 2022
Knowing the latest cybersecurity trends spells the difference between keeping your business safe and opening it up to cyber attackers.
What is a Computer Worm?
A computer worm is not a cute, squiggly little creature. It is an evil, malicious piece of software destined to wreak chaos and disaster on many devices.
What is AD tracking?
Digital and online ad tracking is the process of gathering data and insights about the performance of online advertising campaigns. Digital systems use methods like cookies, unique tracking URLs, tracking pixels, and other tools