Whale phishing is a real threat that’s afflicting corporate bosses all over the world. They are usually the CEOs, CFOs, and other senior executives of the organization. These people hold the highest authority in decision-making and the most access to sensitive business information.
Executives of influence in the organization are being targeted by cybercriminals not to directly victimize them but to use their
What is whale phishing?
Whale phishing is a targeted spear-phishing attack in which cybercriminals impersonate the high-level executives of an organization to send messages to lower-level company administrators in a position to do the acts being requested by the criminals on two things they want most — money and data.
Both higher and lower management executives can be the target of cybercriminals. But lower-ranked employees are more targeted because they are often hesitant to refuse or check a request that appears to have come from a higher authority in the organization.
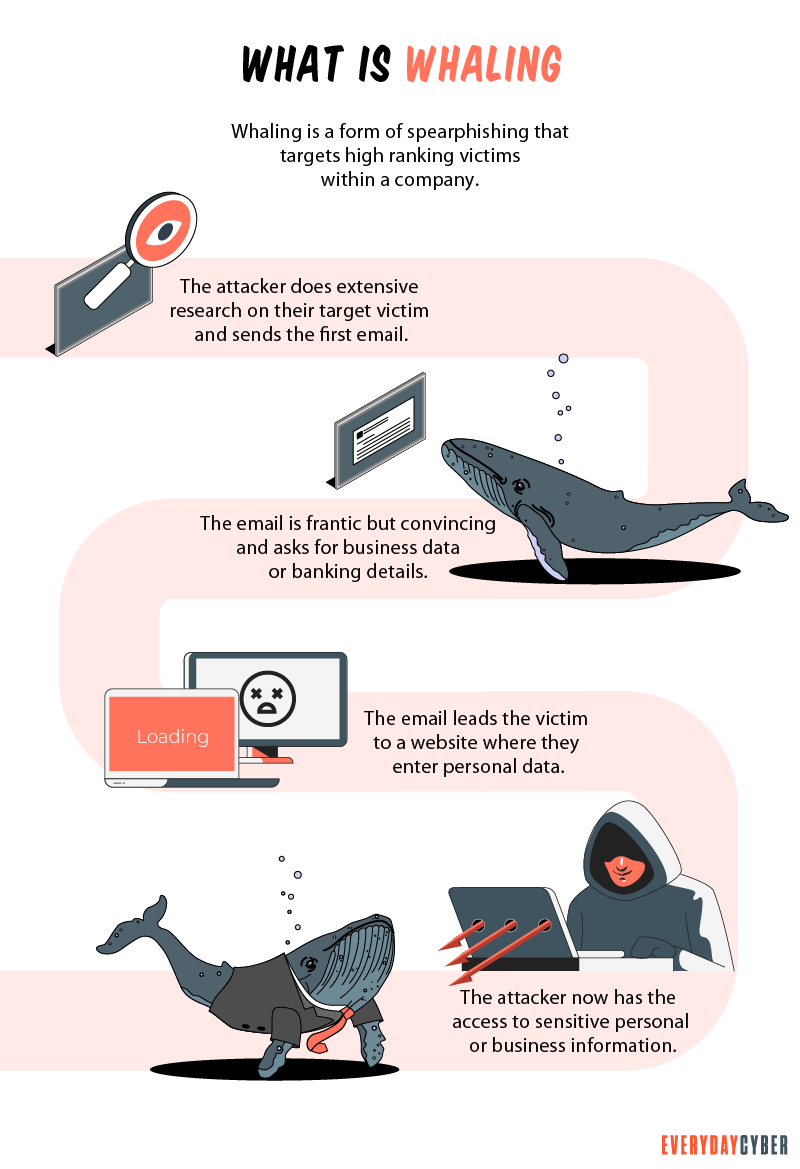
As with all phishing attacks, whale phishing uses emails, SMS, calls, website spoofing, social media, and other platforms to trick their high-value targets. The messages may contain requests to:
- Pay an invoice or send a wire transfer
- Open an attachment
- Click a link
- Send the requested company information via return email
- Visit a fake website where login credentials are required
How does whale phishing work?
Whale phishing is social engineering at its best. Attackers do extensive research on their targets. They will use every resource they can lay their hands on to discover as much information as possible on the people or organization they want to impersonate. They will also conduct a similar level of reconnaissance on the targeted victims who will do the action.
Whalers go to social media to scour personal profiles and insights to show that they and their victims know each other to make the email seem trustworthy. The criminals also visit company websites to learn their target’s business culture and their victims’ work habits.
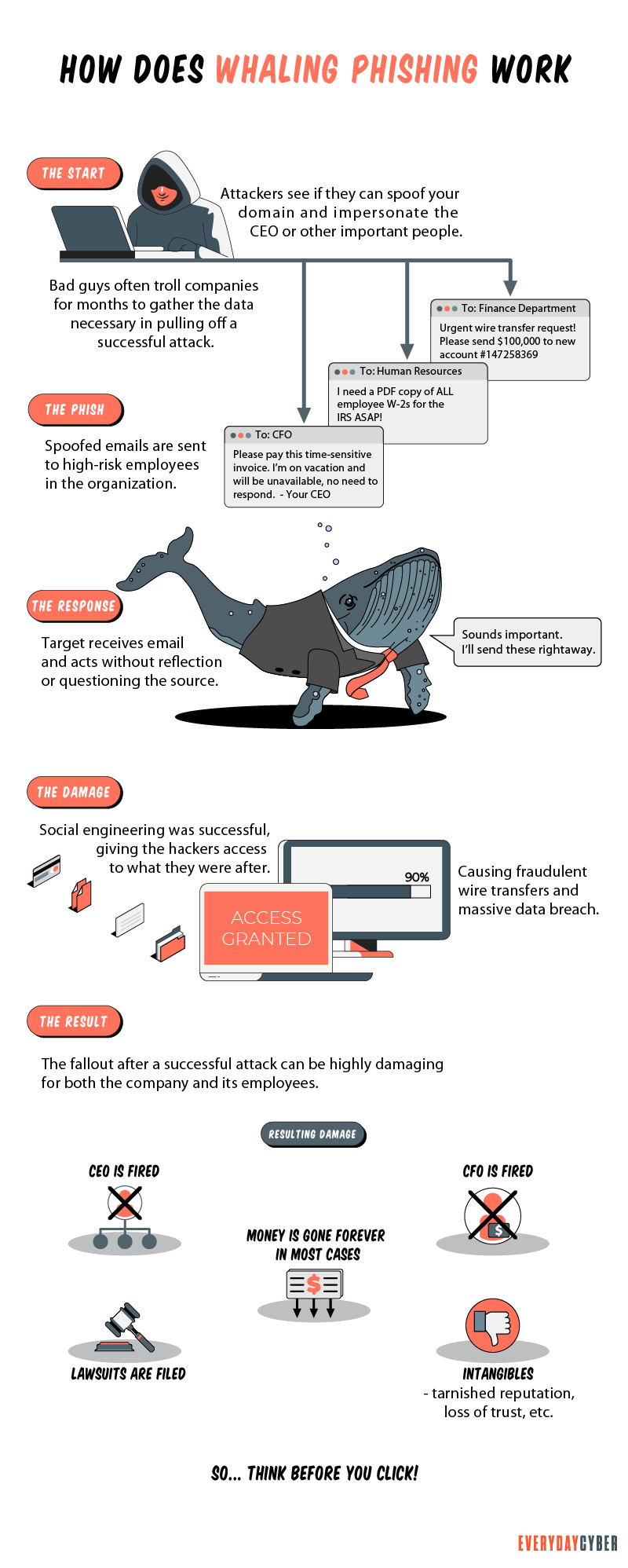
The criminals also study the website design and layout so they are able to replicate them in fraudulent websites. They use the information they are able to gather to tailor their attack to their specific targets. The more customized an attack, the more it will work.
Whaling phishing tactics
Criminals don’t run out of tricks to fool their targets. They always do their best to create innovative ploys, often going a step ahead of new
They exploit the existing trusted relationships of their victims. They study the business so well they are able to adopt the business lingo and customize their attacks according to their targets’ personal preferences. This is the reason why whaling emails are difficult to spot, even by a meticulous eye.
Here are the common whale phishing tactics cybercriminals use:
Whale phishing emails from “colleagues”
This practice is most effective when the whaler uses the spoofed email address of a high-level company executive to send an email to a targeted junior executive whose email address is also compromised. The whaler uses social engineering and the collection of personal information of both executives to convince the recipient that he or she is receiving a legitimate request from a boss.
Whale phishing emails from “partners”
Partners may include suppliers, contractors, consultants, law firms, think tanks, or charities. Before launching the attack, whalers find ways to comprise the partner’s network in order to gain access. Based on accessible information on the partners, the attackers then send emails that appear credible.
Confirmation phone calls
Confirming email messages through
Social media whaling
Social media networks offer a wealth of information. Hackers revolve around social media because they provide informal platforms where people tend to be carefree and less vigilant. Here, attackers are able to gather the information they need to enable them to create more targeted attacks according to their victims’ personal preferences.
Other tactics whalers use are:
- Business email compromise (BEC) using compromised corporate emails
- Credential phishing aiming to steal login credentials
- Wire transfer phishing often involves invoice fraud
- Smishing using SMS
What the statistics say
Whaling attacks using executive impersonations in Q1 2021 have increased by 131% from Q1 2020, according to the email
The same report shows that 59% of organizations say an executive has been targeted for whaling attacks and 46% of these executives have fallen victim to these attacks. The most common technique used was “links” to malicious websites at 51% and gift card requests at 46%. Targeted executives also received whaling emails once every 24 days.
The FBI also reported that phishing attacks cost companies nearly $215 million in 2014. Likewise, the Verizon DBIR reported an increase of nearly 200% in phishing attacks from 2016 to 2017.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
What are the consequences of whale phishing?
The consequences of a successful whale phishing attack can be devastating to both the individual victims and the organization they belong to. Here are some of them:
Financial loss
In most whaling attacks, cyber thieves impersonate a high-level executive requesting a wire transfer. Thieves may also demand ransom money to bring back lost data or remove malware. Couple these with potential fines for data breaches and lost sales and you have a problematic financial position.
Loss of data
In whaling, company executives are usually tricked into clicking through malicious websites that contain malware. Once this is done, the malware immediately finds its way around the targeted information, resulting in data theft or breaches.
Reputational damage
Companies that fall victim to whale phishing stand to lose significant trust from their customers, partners, and other stakeholders. Financial institutions, such as banks, investment houses, and credit card companies, could potentially lose the confidence of customers in their ability to protect their money and data. Companies that are hit so hard may have a difficult time recovering or never recover at all.
Business disruption
When financial losses are huge, company operations may slow down due to insufficient capital to run the business. Data loss may also disrupt customer services while reputational damage may drive customers away. Instead of doing business as usual, affected companies spend more time informing their customers about the loss and crafting new
Real examples of whaling attacks
Whale phishing is a real, clear, and present danger. It attacks both small and big organizations. Here are some examples of whaling attacks:
The Snapchat incident
Snapchat fell prey to a common whale phishing email that appeared to have come from the highest executive of the company. CEO Evan Spiegel purportedly sent an email to an HR staff requesting that staff to provide the payroll information of some former and current employees.
The HR staff responded to the request, effectively handing over sensitive information to the scammer. Fortunately, none of Snapchat’s user data was given to the criminal, only those of the affected former and current employees.
The Seagate attack
Like the Snapchat case, Seagate also faced a data leakage of about 10,000 former and current employees. The information handed over to the criminal included salary information, tax data, Social
The data breach led to a lawsuit on malpractice, lack of surveillance, and poor handling of sensitive data.
The FACC hack
FACC, an Austrian aerospace company, lost $56 million to whaling perpetrated in 2015 but made public in 2016. Using CEO Walter Stephan’s spoofed email address, the hacker sent an email to the company’s finance department requesting a $56 million wire transfer to the hacker’s account. The money purportedly represented payment for an acquisition project. The transfer went through successfully.
Apparently, the hacker studied Stephan’s writing habits to make the message look legitimate. Stephan, his CFO, Minfen Gu, and the finance department employee who fell for the scam were removed. In 2018, FACC sued Stephan and Gu for $10 million in violation of their duties, but the Austrian courts threw out both lawsuits.
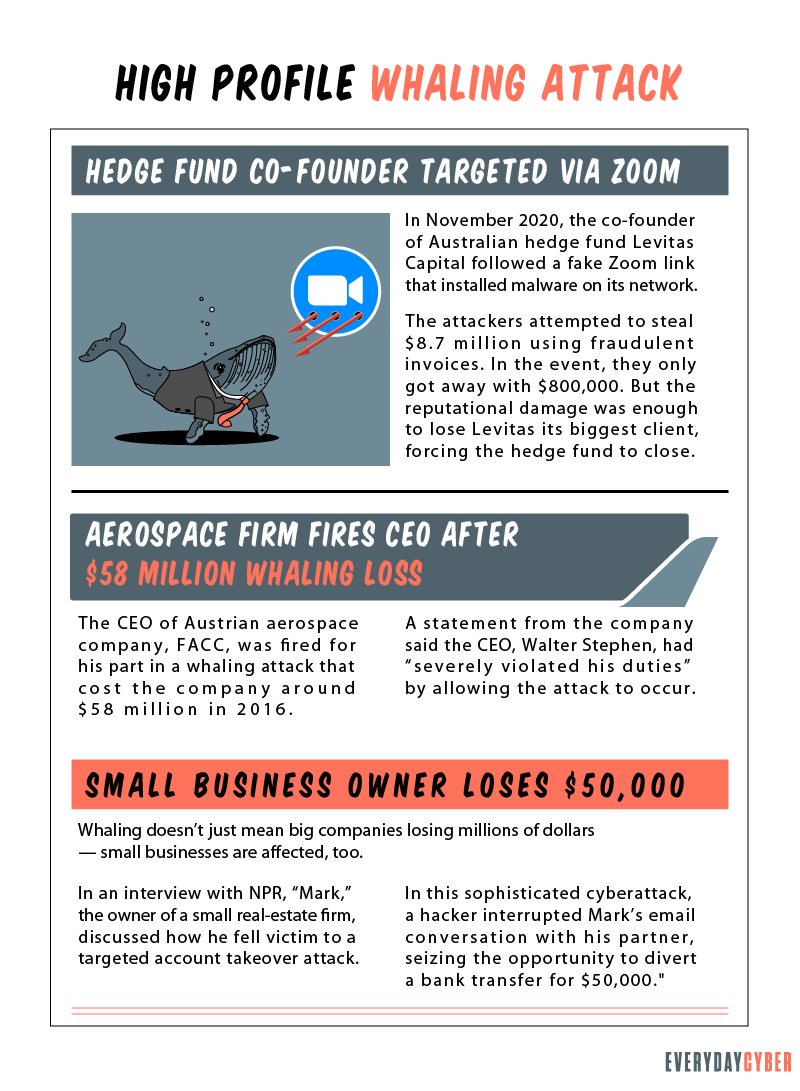
The whaling attempt on Australian hedge fund co-founder
The hackers used a fake Zoom invitation to compromise the email account of Sydney-based Levitas Capital co-founder Michael Fagan. Using Fagan’s compromised email, the criminals sent three invoices worth $8.7 million to the company’s trustee and administrator. The message assured the administrator that there was no need for the usual confirmation through the
On September 23, 2020, Fagan discovered unauthorized money transfers from the hedge fund’s Commonwealth Bank account in three tranches:
- $2.5 million sent to the Bank of China in Hong Kong
- $5 million to the United Overseas Bank in Singapore
- $1.2 million to an ANZ account in western Sydney’s Blacktown
The hedge fund was able to recall most of the money, but the hackers’ money mules were able to withdraw $800,000 from the ANZ account.
A small business $50,000 whaling case
Mark is the owner of a real estate company in Seattle. The scam started in 2017 when criminals hacked into his email conversation with a business partner over a $50,000 payment owed to the partner.
While monitoring the conversation and pretending to be the partner, the hackers inserted a message requesting the money to be sent to a bank account they controlled. Mark did. He only realized what had happened when his partner told him he never received the money. They alerted the bank but it was too late, the $50,000 had been withdrawn by the hackers.
What are the best ways to spot whale phishing?
Whale phishing attempts are difficult to identify because they are carried out over communication mediums commonly used in the course of business, such as emails, SMS and calls. Still, organizations should take all the precautionary steps to prevent these attacks from becoming successful.
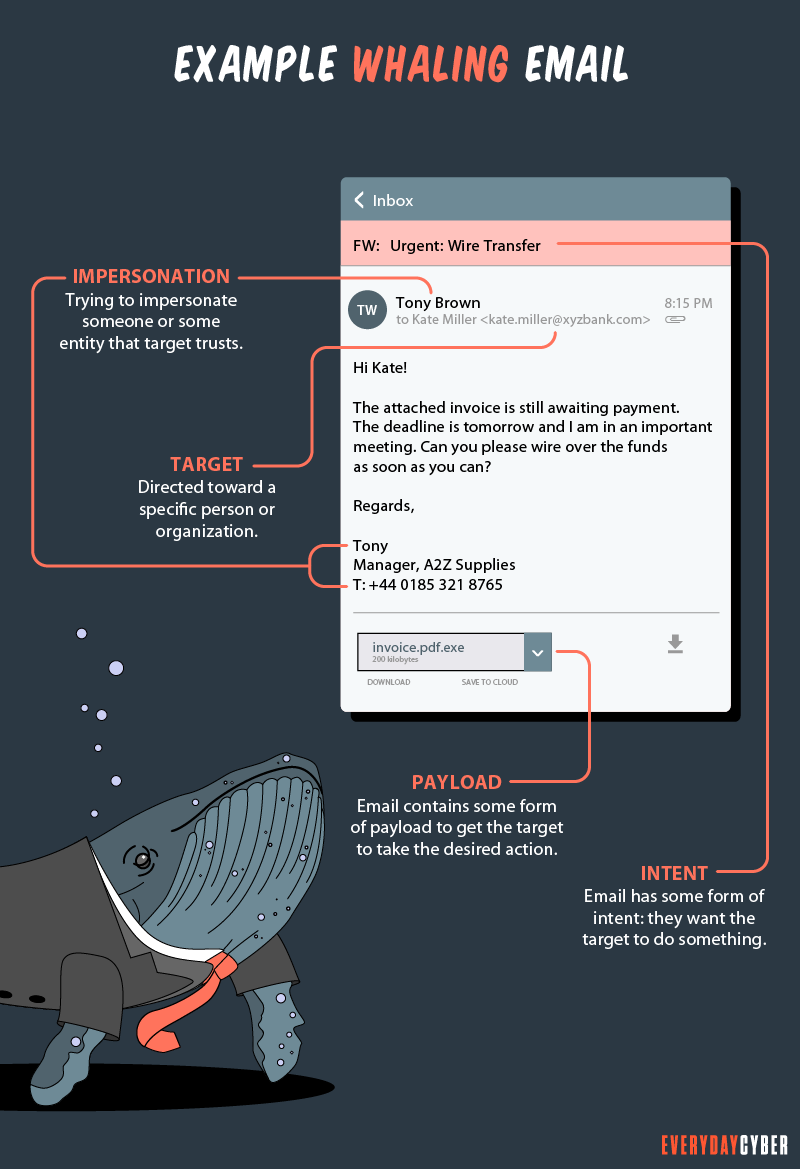
Here are the best ways to do it:
1. Filter incoming emails
Most whale phishing emails come from outside the company email network. As such, one of the basic ways to mitigate whale phishing attacks is to flag down suspicious external emails. The email management team should pay particular attention to unusual requests. If they discover something odd, they should immediately alert the concerned higher authority for verification.
2. Watch out for near-similar email domains
Hackers spoof email domains with very subtle variations, often passable to a busy and stressed recipient. Email receivers should keep an eye out for minor alterations that may come in the form of additional, deleted, or altered characters. For example, the legitimate john@everydaycyber.net email domain can be spoofed as john@everydaycyber.com. If the recipient isn’t paying close attention, the email may pass for legitimate.
3. Double check unusual requests
This is most applicable to large payment requests, especially if such payments have not been arranged before and now require urgent action. Emails from the network admin requesting you to enter your password for some vague reason are also suspect. Whenever possible, crosscheck the request with a
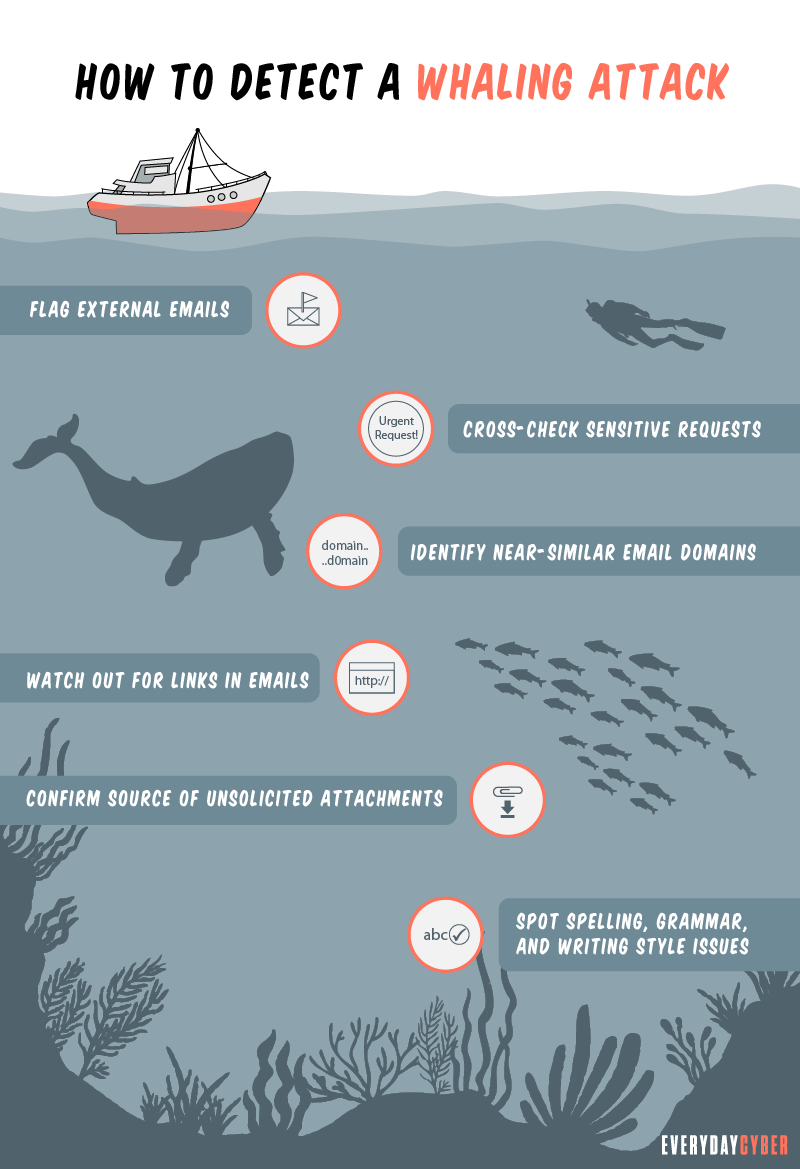
4. Be wary of email links and attachments
To find out if an email link cannot be trusted, hover the cursor over it and verify where it’s going to head. If the URL doesn’t match the email or SMS message, don’t click the link or download the attachment and proceed to delete the email.
Some malicious actors have found a way to hyperlink the entire email. A single accidental click on any portion of the email may open a malicious web page or download poisoned content. If this happens, close the opened web page and report the incident to the IT team immediately.
5. Pay close attention to unsolicited attachments
Unsolicited attachments, like an official receipt for items you didn’t buy, are tricks whale phishers use to convince you to open tainted files. The message creates some sense of urgency, threat, or fear of a violation. The attachments often contain malware that steals your data or your money. Reach out to the supposed sender via
6. Keep an eye on grammar, spelling, and writing habit flaws
If you’ve been communicating regularly with people you know, you would be familiar with the writing style they use. Anything that goes off tangent is a red flag for scams, such as whale phishing. For example, if your CFO usually starts his emails with a “Hi John” and you receive one with a “Dear John”; flag that email and reach out to your CFO to verify its legitimacy.
Whale phishing messages are also written with poor grammar and spelling errors. Hackers are technical people, not writers. Unless they hire good writers, their messages will sound unprofessional.
How can you prevent whale phishing attacks?
While automated
Here are useful tips to do this:
1. Prioritize awareness of whale phishing
Creating awareness of cybersecurity threats is the first step to educating and training employees and all other users of the company email network. Without knowing the potential threats, employees wouldn’t know what to watch out for. Getting expert speakers, using interactive video and PowerPoint presentations, and testing the employees’ awareness through quizzes all contribute to an effective awareness campaign.
The education process should include:
- What whale phishing is all about
- How it works
- The consequences
- How to identify the signs
- How to prevent the attack
- What to do if you fall victim to a whaling attack
It doesn’t stop at education. Let your employees experience actual phishing attacks in simulation training, taking care that such experience doesn’t pose any risks to
To go a step further, higher management stakeholders should not only give their full support to these training programs but should participate in the training activities. While they are not the direct participants in the whaling exploits, their identities are being used by criminals to make the request more authoritative. They themselves should also learn to safeguard their personal information so hackers can’t get hold of them.
2. Use social media prudently
Hackers love social media platforms because it’s where they can get to know their victims better. A whale phishing email could contain personalized photos, names of victims’ friends, memorable dates, and other sensitive information taken from social media. A good practice is to encourage employees to separate their private social media accounts from their public and business social media accounts.
3. Adopt a comprehensive data protection policy
Company data protection is a broad responsibility. It involves protecting and monitoring sensitive files, such as intellectual property, plans for new ventures, mergers, and acquisitions. The policy also tracks all external emails that arrive in the inboxes of C-suite executives, especially those containing payment requests.
Aside from social media, the company’s website, newsletters, press releases and other public channels where company information is published are also fertile grounds for tons of information that management needs to protect.
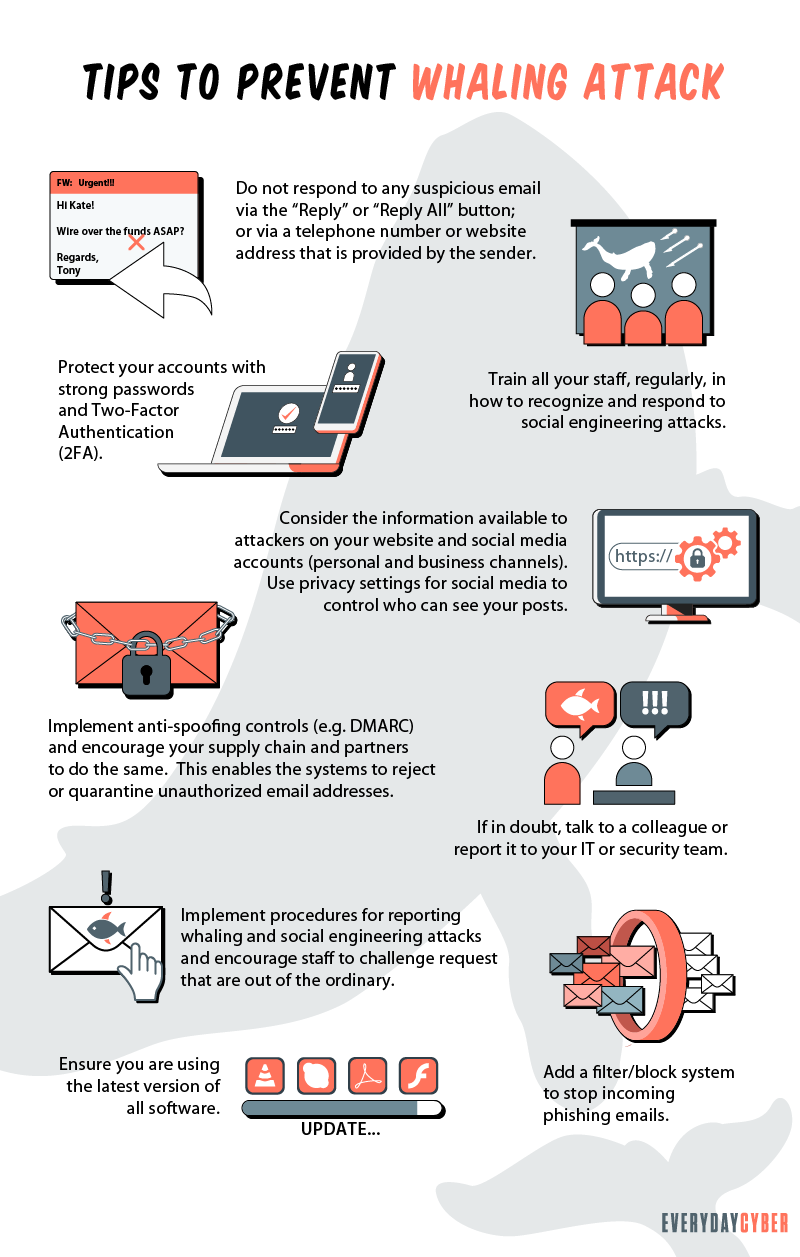
4. Create an all-inclusive cyber threat intelligence strategy
Cyber threat intelligence is a collection of information an organization uses to analyze past, present and future threats that may target the organization. The objective is to gain knowledge about these threats, build effective defense systems and mitigate the risks that destroy their reputation and bottom line. This offers a proactive approach to cybersecurity threats.
5. Build a comprehensive security plan
Securing data is getting more challenging but it has to be done. The plan should complement the business strategy rather than get in the way of people trying to do their jobs. A
Here are the steps needed to build a comprehensive
- Start with a well-thought-out
security risk assessment - Develop and adopt preventive measures to keep potential threats at bay
- Create a culture of
security throughout the organization with continuing employee training - Monitor networks and conduct regular audits to find out what’s working and what’s not working
- Be transparent in order to build trust among peers and other stakeholders
- Consider using automated
security tools
Our final thoughts: Whale phishing is here to stay with increasing force and sophistication. While company executives are at the forefront of the attacks, everyone should do his or her own part in cybersecurity no matter how small it is because one false click or response can bring the whole organization down.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is HTTPS?
HTTPs enables web servers and web browsers to establish secure connections. It encrypts data being transmitted in both directions. This helps prevent thieves from stealing sensitive information along the way.
What is a Computer Worm?
A computer worm is not a cute, squiggly little creature. It is an evil, malicious piece of software destined to wreak chaos and disaster on many devices.
What is Shoulder Surfing?
Shoulder surfing is a form of social engineering that enables cybercriminals to gather information just by looking over their victims’ shoulders. The aim of shoulder surfing is to obtain personal data, such as usernames, passwords or personal identification numbers (PINs), bank account numbers or credit card numbers.
What is AD tracking?
Digital and online ad tracking is the process of gathering data and insights about the performance of online advertising campaigns. Digital systems use methods like cookies, unique tracking URLs, tracking pixels, and other tools
What is a zero-day threat?
A zero day threat is a security flaw known or unknown to the software vendor which hasn't had a patch made to fix the vulnerability.
What is a DDoS (Distributed Denial of Service) Attack?
DDoS attack or Distributed Denial of Service, is a coordinated attack intended to crash and make unavailable targeted websites and online systems by overwhelming them with data.

