Remote access tools are especially useful for accessing and controlling workplaces and devices across vast physical distances. They help maximize the efficiency of IT systems and provide timely response and support to end users.
However, if remote access falls into the wrong hands, you can just imagine the chaos that follows. Malicious minds have seen an opportunity in remote access technology to infiltrate computers and networks to pull off their harmful activities. One such tool is a remote access Trojan or RAT.
What is a RAT?
Remote access Trojan derives its name from the Trojan horse in Greek mythology. In the tenth year of the Trojan War, the Trojan horse was constructed by the Greeks. It was a giant hollow wooden horse intended to be given to the Trojans as a peace offering to signal the end of the war. It was a tricky strategy because the hollow horse carried Greek warriors in its belly that later ravaged the City of Troy.
A remote access Trojan or RAT was created in much the same way. A user might be led to believe that a file looks safe to run but instead, delivers malicious content. A remote access Trojan is a software used by hackers to gain unauthorized access and remote control on a user’s computer or
A RAT gives the hacker the ability to silently browse network resources, such as personal information, files, usernames, passwords, screenshots, emails and chat threads. Since a RAT bypasses firewalls, authentication tools and intrusion detection systems, it also allows the hacker to monitor user behavior, copy files and change computer settings.
How does a RAT work?
A RAT works just like standard remote software but it is designed to stay hidden from the device user or anti-malware software.
A hacker needs to convince a user to download a RAT software by clicking on an email attachment from a seemingly known sender or downloading a software from a presumably legit source. This is social engineering at work.
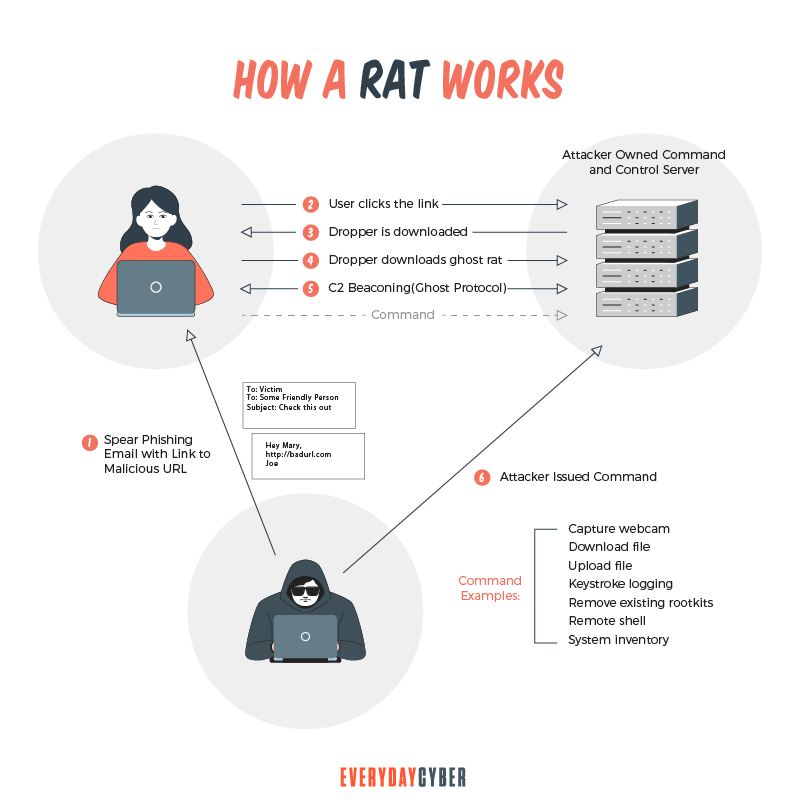
RATs are often bundled with other malware like a keylogger. A keylogger allows attackers to obtain credentials from personal accounts, collect financial data or steal intellectual property from corporate accounts.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How did RATs come into being?
Security researchers Veronica Valeros and Sebastian Garcia worked on a paper that presents a timeline of the most well-known RATs in the last 30 years. Here are the highlight of that study:
1990 to 1999
Legitimate remote access tools first emerged in 1989. One of them was NetSupport which was created for remote classroom management. The following decade saw a rapid growth of RATs. This first phase of the RAT timeline was marked by home-made RATs but were not heavily used and did not prosper. The most prominent RATs during this time were:
- Back Orifice
- SubSeven
- NetBus
2000 to 2009
During the second phase, more mature RATs began to surface. They were intended for fun, but were later used for attacks and profits. Some prominent examples are PoisonIvy, Gh0st and DarkComet.
2010 to 2019
The third phase showed a significant shift. As the market for remote access tools matured, RAT sellers were expected to provide new features and support, and in some cases, host part of the infrastructure. Some of the RATs that stood out in their particular area of expertise are:
- FlawedAmmyy
- Quasar, a free and open-source RAT
- PhoneSpector for iOS
- AndroRat for
Android - Havex for industrial control systems (ICS)
Why are RATs useful for attackers?
Hackers love remote access Trojans. It gives them complete administrative control over the infiltrated system while doing their job quietly and secretly. It provides them unrestrained hacking activities to accumulate data over time without causing any alarms that the victim will notice.
When paired with a keylogger, RATs give hackers the ability to acquire credentials for bank, credit card, loan, investment and other financial accounts. Add to that the capability of RATs to wipe out hard drives, impersonate victims on the Internet and download illegal content. They can also turn on computer cameras and microphones and access sensitive photos and files.
From a geopolitical perspective, RATs can do extensive damage to rival nations. They can wreak havoc to infrastructural facilities, such as traffic control, intelligence, energy generation or communications systems. This happened in Georgia when Russia launched a DDoS (Distributed Denial of Service) attack against Georgian military systems and news agencies to sow disinformation.
How do devices get infected with a RAT
Remote access Trojans can be installed on targeted devices in a number of methods similar to malware infection vectors. Cybercriminals often use social engineering to trick victims into downloading malicious documents attached to emails, advertisements, pop-ups, infected web links and SMS. They can also be acquired from poisoned links in social media accounts. RATs can likewise be injected directly to a victim’s computer.
How do you detect a RAT infection?
RATs can be difficult for the average user to identify because they are planned out to avoid detection. They use randomized filenames and file paths to prevent them from identifying themselves. They don’t show up in the list of running programs and act like legal programs.
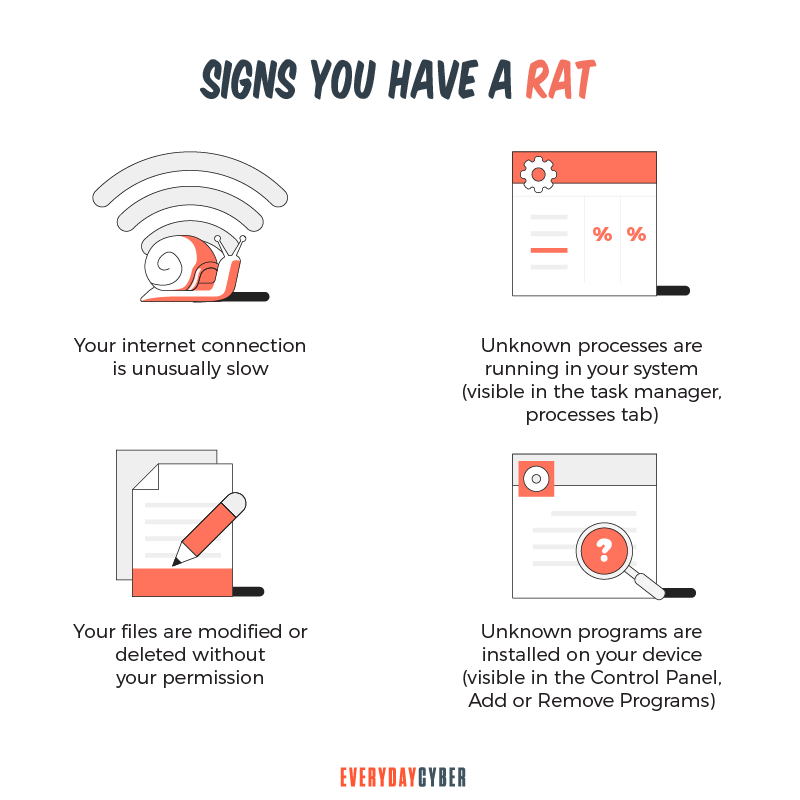
Moreover, RAT spyware will use computer resources to prevent the slowing down of device performance so that the user will not be alerted. They also don’t delete files or move cursors while the user is using the computer, but they do it when the user is not on the computer.
To detect a RAT initially, open the Task Manager and check on all applications and programs running on your machine. Malware creators give legit-sounding names to their malware, so watch out for suspicious content and look them up online to determine if they are RATs or other malware types.
What to do if your machine has been infected with a RAT
How then would you determine if your computer is infected with a RAT if the RAT keeps hiding? An anti-malware software can usually detect and remove it from your system.
If indeed your machine has been infected, disconnect your device from the Internet to stop the RAT from further attacking your system. Install
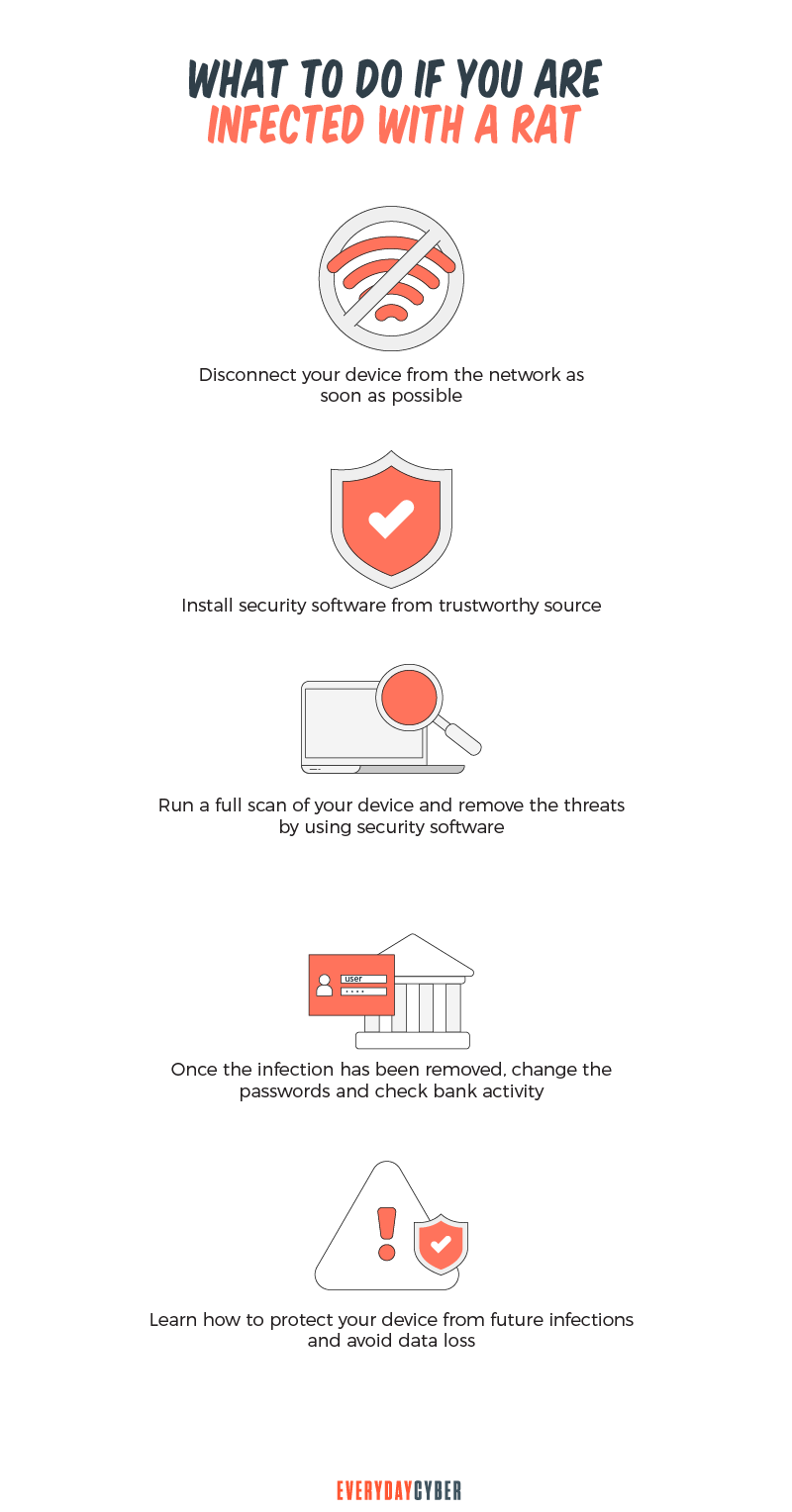
After removing the RAT, change passwords across all your accounts. If you notice some unusual bank transactions that you did not initiate, report them immediately to your bank.
Who are the favorite targets of RATS?
Remote access Trojans target individual users, businesses, schools, governments and vital infrastructures in energy, communications and traffic management. They are, however, especially attracted to financial institutions.
Cybercriminals attempting to commit online banking fraud deploy RATs because they require minimal technical know-how. They can hijack online banking sessions with the help of RitB or Rat-in-the-Browser alongside a RAT.
The RAT that has already been downloaded onto the user’s device alerts the attacker when the user logs in to his or her banking account. At this point, the attacker remotely suspends the user’s session, opens an invisible browser on the victim’s computer and works on the fraudulent transaction without the user knowing it.
In the meantime, the user will think he or she is interacting with the bank, and vice versa, while the attacker manipulates what the user and the bank see at either end of the interaction.
For example, if the user initiates a money transfer, the attacker can change the value or recipient of the transfer with neither the user nor the bank knowing what is happening.
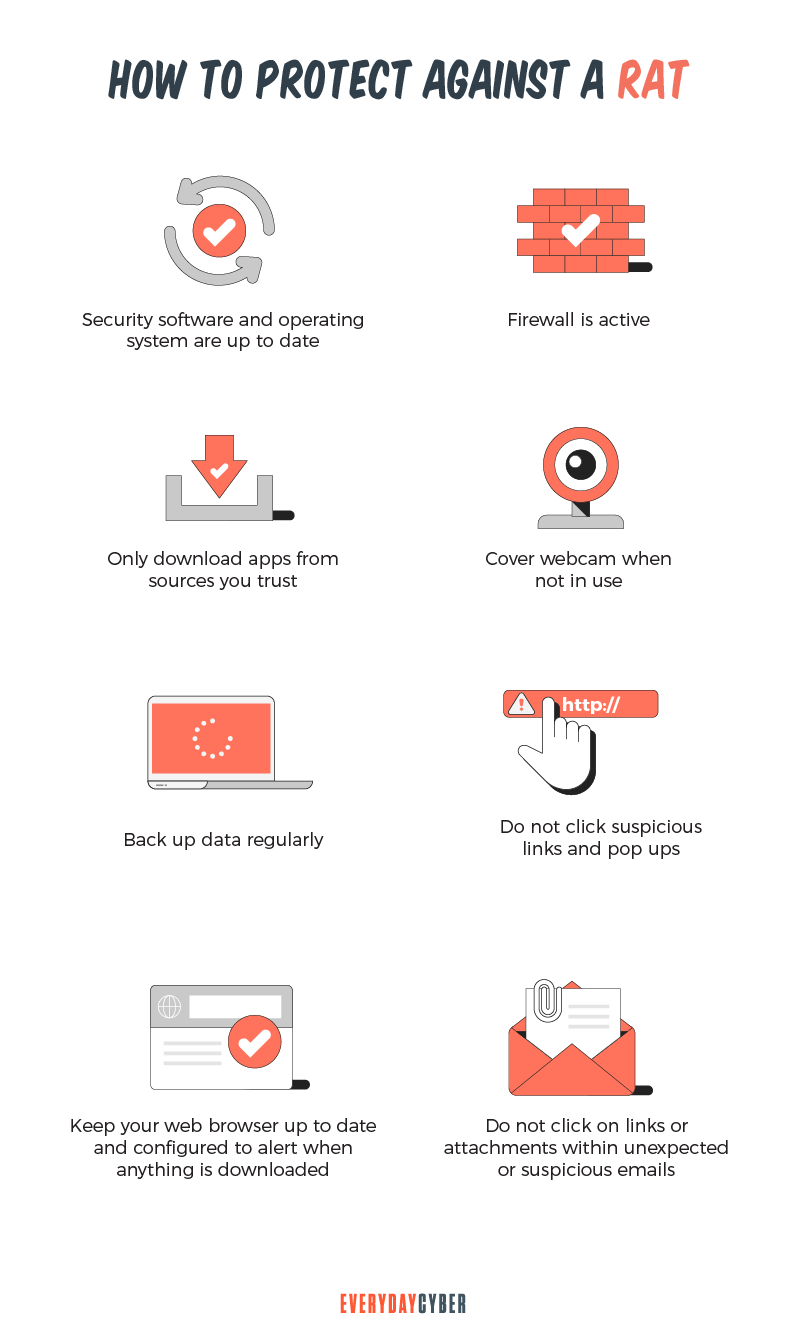
How to protect yourself from RATs
Remote access Trojans are covert by nature, enabling them to create chaos on your computer silently. This is why users need to do and not do some things to protect their devices from RATs, such as the following
- Install and run an anti-malware suite on your device.
- Automate diagnostic scans to follow regular intervals.
- Update your operating system’s software and other applications as soon as updates are available from a trusted provider.
- Protect your accounts with unique and strong passwords.
- Use firewalls.
- Back up your files.
- Avoid unsafe websites.
- Refrain from opening emails from senders you don’t know.
- Avoid downloading programs and applications from questionable publishers.
- Don’t open a link in an email unless you’re sure of the content and trust the sender.
- Don’t click on pop-ups that offer promos or prizes from an activity you never participated in.
Individual users may be able to keep watch on their accounts, but businesses and other organizations are at risk for more RAT attacks. Compromising just one machine in an organization could provide a backdoor for crooks and encourage them to keep coming back.
Again, our simple advice is to treat prevention as a first line of defense.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
Things About Ryuk Ransomware You Need to Know Right Now
Ryuk ransomware is one of the most dreaded malware to date. It encrypts or steals corporate data to extort millions of dollars from its victims. The Covid-19 crisis greatly influenced the recent rise in ransomware. The remote work response to the pandemic created huge gaps in the worlds cyber defenses. Threat actors saw these vulnerabilities as opportunities to spread large-scale ransomware attacks.
What to do if your phone is lost or stolen
When your phone is lost or stolen, it is more than just a pricey handheld that is lost. Our phones keep track of our lives. If you’ve lost your phone, there are things you can do to track, locate, and recover it depending on the type of phone you have. Read this to get tips on how.
What is a Potentially Unwanted Program (PUP)?
PUPs refer to programs, applications and other software downloaded onto computers or mobile devices that may have an adverse impact on user privacy or security. The term “potentially unwanted program” was coined by McAfee to distinguish the program from malware.
5 Biggest Cybersecurity Mistake SMBs do
Small and midsize companies can’t afford to learn cybersecurity haphazardly while cyberattacks are steadily rising. If you’re a decision-maker, you can’t ignore the 424% increase in cyber breaches in 2021.
What is a deep fake video and how to spot It
People can easily be fooled into believing they are seeing or hearing something that has no basis in truth in a culture filled with misinformation and deception. Deepfake videos have forced viewers to wonder whether or not what they are seeing or hearing in a video or audio recording is real.
What is Whaling?
Whale phishing is a targeted spear-phishing attack in which cybercriminals impersonate the high-level executives of an organization to send messages to lower-level company administrators in a position to do the acts being requested by the criminals on two things they want most -- money and data.


