Have you ever tried typing a website address into your browser and was led to a page other than what you were looking for? You may have missed a letter, number, dot, or character, or interchanged characters, or misspelled the domain name. That is why you were sent to the wrong website, a typosquatter’s website.
What is typosquatting?
When you occupy a piece of uninhabited land or building that is not yours and without the permission of the owner, that is squatting. It is illegal.
In the same manner, when you register a domain name that looks closely similar to another domain name, particularly popular brands and businesses, that is typosquatting.
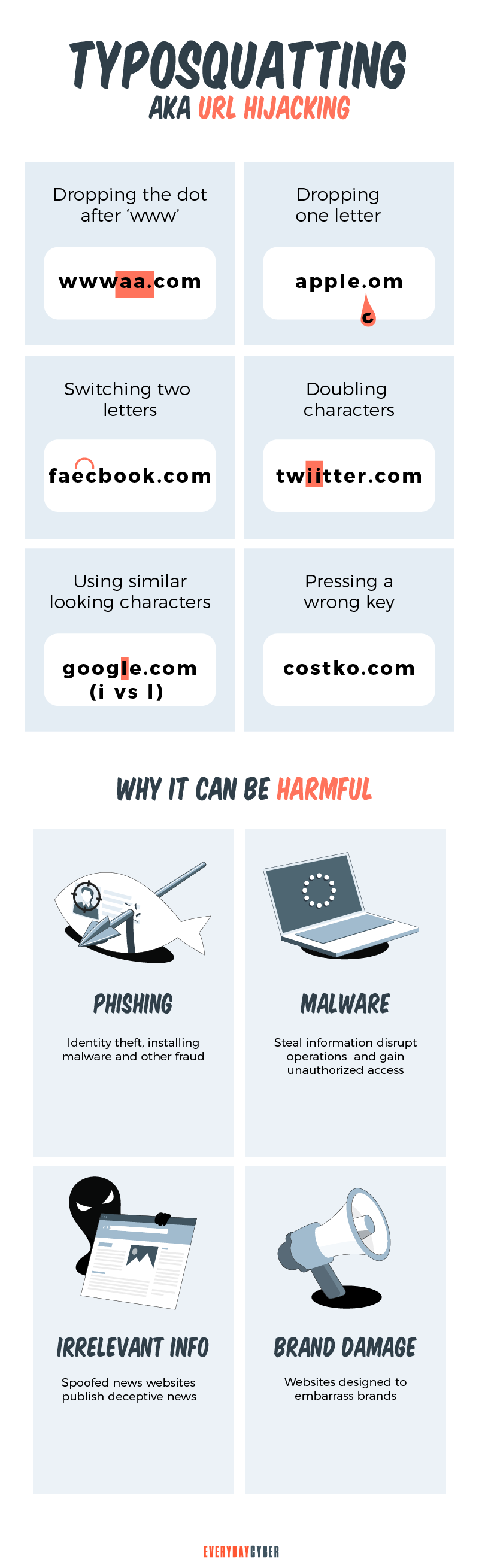
Cybercriminals target visitors that accidentally mistype website addresses directly into their browsers. They use typosquatting, also called URL hijacking, to deceive visitors and lead them to malicious sites they themselves have set up.
When users get to these alternative websites, this is a chance for hackers to gather personal information, such as bank and credit card details. Counterfeit website owners can also sell competitive products or advertise adult content, which generates high revenue streams for the hackers.
How does typosquatting differ from cybersquatting?
Typosquatting and cybersquatting work similarly, but they differ in their uses. Hackers use typosquatting for malicious activities. On the other hand, they use cybersquatting to buy or register typosquatted domains with the intention of selling them back to the owners of the real brand or website for a hefty amount.
Many popular companies are willing to buy back fake URLs of their websites to prevent misuse and potential revenue loss. They can also use the URLs to drive traffic back to their original website.
How has cybersquatting changed over the years? Cybersquatting has evolved to keep pace with the times. It hit mass adoption in the 21st century as hackers registered more typosquatting domains as well as the names of celebrities, such as politicians, actors, and business magnates.
Today, cybersquatting generally involves the emergence of new TLDs, such as .xyz, .coffee, .tech, .actor, .space and .yoga.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How does typosquatting work?
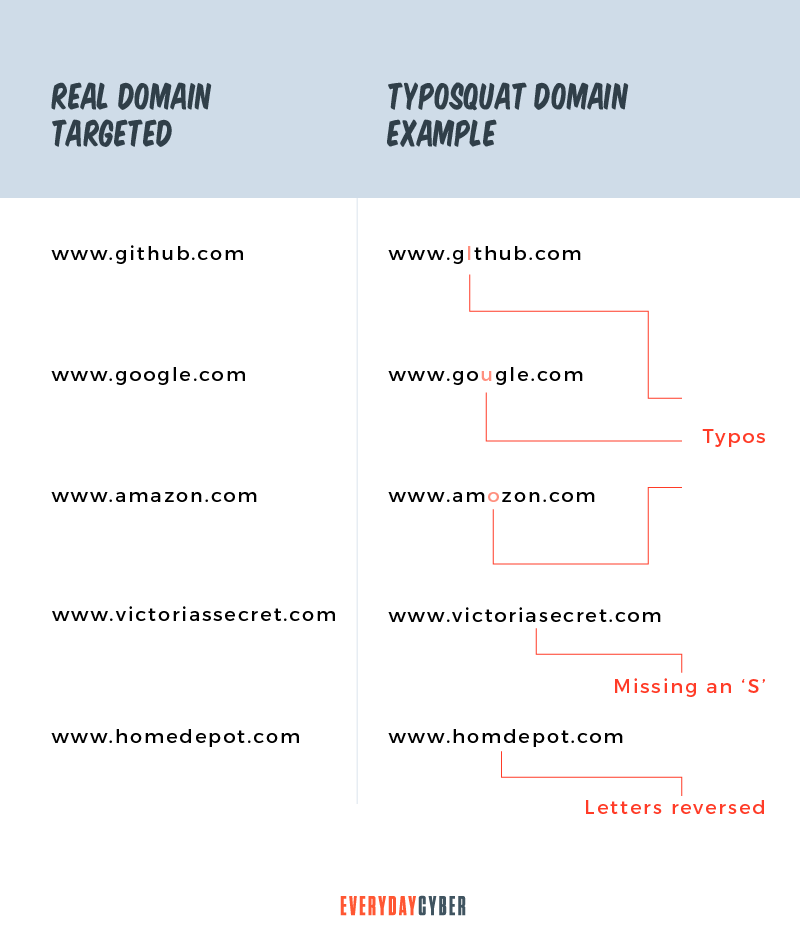
Cybercriminals start their typosquatting scheme by registering a domain name that may be a misspelled name of a popular website. They even go so far as buying or registering multiple domain names of a single website, taking into account all possible typing mistakes a user may make.
For example, domain.com, the legit website a hacker wants to mimic, may have variations, such as:
- dommain.com
- domain.cm
- domain.co
- domiin.com
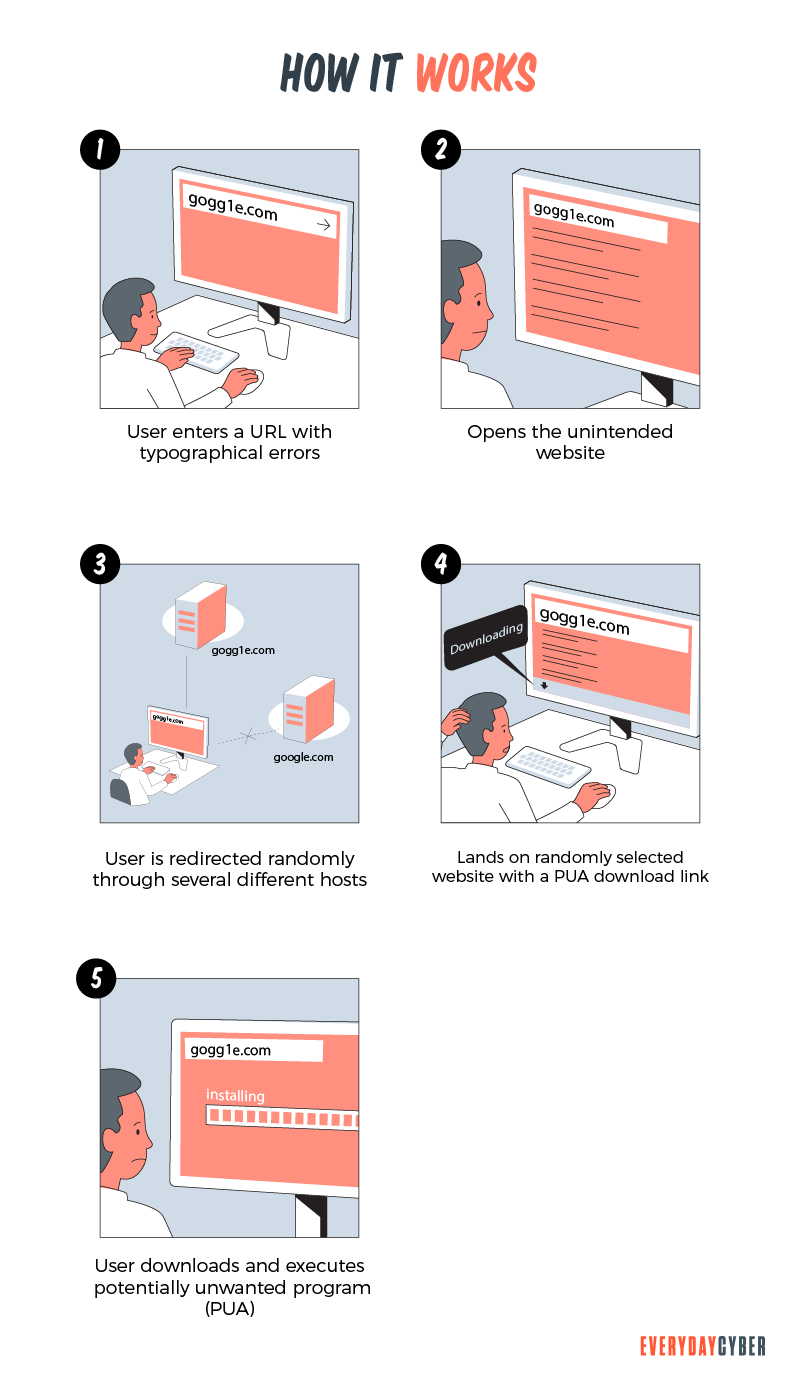
Typosquatting relies largely on human error. That is why hackers design fake domain names with simple differences, such as adding or deleting an obscure letter, number, symbol, or punctuation mark. These are the common typing mistakes that hackers leverage:
Typos
Typos are a product of haste. Searchers who type quickly often end up hitting the wrong letter, number, or symbol. Even simple words like “the” mistakenly typed as “teh” can mean a lot for hackers.
Errors in spelling
It is common for people to misspell long words that contain a lot of vowels. Typosquatters love to scoop up domains with such words and wait for searchers to make spelling mistakes that result in people landing on their malicious websites. Some examples are:
- infosecinstitutte.com instead of infosecinstitute.com
- scienederect.com instead of sciencedirect.com
- cheapslsecurity.com instead of cheapsslsecurity.com
Spelling variations
Alternative spellings are common between the American English and British English languages. These can confuse Internet searches looking for common products and services. For example, the American English word “labor” is spelled “labour” in British English. If the website address you are typing contains words with spelling variations, this can result in a wrong URL possibly leading you to a typosquatter’s website.
Domains with hyphens
This typosquatting technique involves adding or removing a hyphen in the domain name. At a glance, people are often confused with the presence or absence of a hyphen. For example, if the genuine URL is “onlinejobs.com”, hackers may add a hyphen in the domain as in “online-jobs.com”.
Corrupting or changing domain endings
Domain names normally end with a top-level domain (TLD) that includes .com, .co, .uk, .us, .au and many more. Domain names can also end with the type of organization, such as .org, .web, .edu, or .net. For example, www._____.com can be changed to www._____.org. Or www._____.com can also be changed to www._____.co.
What are the common types of typosquatting techniques?
Cybercriminals use typosquatting for various cyberattacks. To achieve their goal, they implement these common types of typosquatting strategies:
Imitators
The typosquatting website acts as if it is a genuine site. It imitates its target brand or website, including the site’s page layout and the brand’s logo and color scheme. Its main aim is to perform a phishing attack to gather personal information like passwords, bank, and credit card numbers, or Social
Bait and switch
The fake website baits you to buy an item you were intending to buy at the legitimate website. You will then pay for it but will not receive the item. Hackers can also use this scheme to steal credentials to install malicious software on devices.
Leverage traffic to generate revenue
The owners of typosquatting websites can monetize traffic by putting up advertisements and pop-ups. The more careless searchers there are, the more these hackers will earn.
Affiliate links
The fake websites advertise products and services of authentic brands and become a partner of the company’s affiliate program. When searchers visit the fake websites, the fake websites send back the traffic to the original website through affiliate links. When they do this, they get a referral commission. [7]
Related search results listing
Owners of typosquatting websites can earn additional income by redirecting traffic to competitors’ websites. They can charge the competitors on a cost-per-click basis.
Surveys and giveaways
Typosquatting websites fool visitors into getting customer feedback. In reality, they are interested in personal information and other data to carry out
Install malware
Many typosquatting websites are designed to inject malware. Once they have infected your device with a virus, they can ask for a substantial amount to uninstall the virus. Other websites can infuse a virus that tracks your keyboard strokes, browsing history, and private email messages.
Joke sites
As the name implies, cybercriminals make fun of the official website for revenge or in collusion with a competitor. These sites are related to gripe sites that publish political, religious or social views that contradict the legit website’s values.
What are some advanced typosquatting techniques?
Typosquatting feeds on peoples’ typing mistakes. The techniques are constantly evolving as people make new mistakes. While not that common, these advanced typosquatting techniques are trickier and more difficult to detect by the average eye or wandering mind.
Homograph attacks
A homograph is a word that has the same spelling as another or more, but may differ in meaning and pronunciation. Here are examples of homographs: [8]
- Tear pronounced as “teer” means the watery fluid produced by the eyes
- Tear pronounced as “tair” means to pull apart into pieces
In typosquatting, homograph attacks work on the visual similarity of the characters that make up the domain name. For example, the uppercase “O” would be similar to the numeral “0” but with a slight difference in most computer typefaces. In other typefaces, these two characters are totally identical.
Bitsquatting
Bitsquatting relies on a computer error that is one bit different from the genuine website a user wants to visit. So, microsoft.com could be typosquatted as mic2osoft.com with the letter “r” one bit different from the numeral “2”. Once the victim reaches the malicious site, the hacker can spread malware, phish for sensitive information or carry out cyberespionage.
Soundsquatting
Soundsquatting happens when two words with similar sounds but different spelling and meaning can be mistakenly interchanged. For example, “wait” may be mistaken for “weight”. If you are in a hurry, you could type waitloss.com for weightloss.com.
Typosquatting Cross-Site Scripting (TXSS)
Typosquatting can be done on software packages. Developers might unwittingly download and install malicious software. This poses a serious problem to all visitors visiting the typosquatting site.
What harm can domain squatting do to systems and business?
Typosquatting negatively impacts affected businesses and systems. Systems can get infected with viruses and other malware, making them function improperly or crumble all together. The effect on businesses can be more visible. Here are serious threats businesses may encounter from typosquatting:
Social engineering and phishing attacks
Cybercriminals can send out phishing emails using a typosquat of your organization’s website to your employees and customers. Since the typos and spelling errors seem minimal and your employees trust your brand, they may unknowingly click on malicious links. This could result in the hackers installing malware, stealing data and scamming both employees and customers.
Damage to brand reputation
Customers who are landing on malicious websites, even if it is not your fault, will be disappointed. They may lose trust in your company and your ability to protect their information and, thus, harm your reputation. Worst, they may start looking for other brands or going to your competitors.
Revenue loss
If customers lose confidence in your brand, you may eventually lose them and the revenue they have been providing. If employees distrust how you manage their data, this may mean lowered morale, decreased efficiency, productivity, and loss of revenue. These affect your bottom line.
What laws apply to cybersquatting and typosquatting?
Most cybersquatting is illegal in the United States. In 1999, the government enacted the Anticybersquatting Consumer Protection Act (ACPA). This law protects both trademark owners and consumers. The law provides that:
- URL owners must prove that they will use the URL in good faith
- URL owners must show proof that the URL is not similar to an existing trademark, brand or website
- Legitimate URL owners can seek damages of up to $100,000 depending on the severity of the damages
The World Intellectual Property Organization (WIPO) oversees squatter issues internationally. To get ownership of a typosquatted domain, you can petition this court and prove that:
- The domain is confusingly identicalI or similar to your original domain
- The holder of the typosquatted domain has no right to any of your products, services or work
- The domain registrar uses the site in bad faith
You can also file a claim to get control of a typosquatted website at the Internet Corporation for Assigned Names and Numbers. This body is mandated to give ownership rights to the URL, but does not impose compensation for damages.
The Coalition Against Domain Name Abuse (CADNA) was established in 2007 with the aim of reducing cybersquatting in all forms. The group believes the maximum damages are not proportional to the damage done by hackers. They intend to increase the penalties.
How can you protect yourself from typosquatting and cybersquatting?
Here are some ways to prevent typosquatting or cybersquatting from happening to you.
For individuals:
- Do not open emails unless you are completely sure of the sender or source
- Avoid clicking on attachments in emails, chat and text messages and social media as well links or pop-ups in unknown websites
- Use
antivirus software to protect your device from malware
- Bookmark frequently needed sites so you don’t have to type URLs everytime you want to access those sites
- Search for sites via search engines so you don’t risk making typos and other errors
- Hover your mouse over links to check for spelling and completeness of the domain
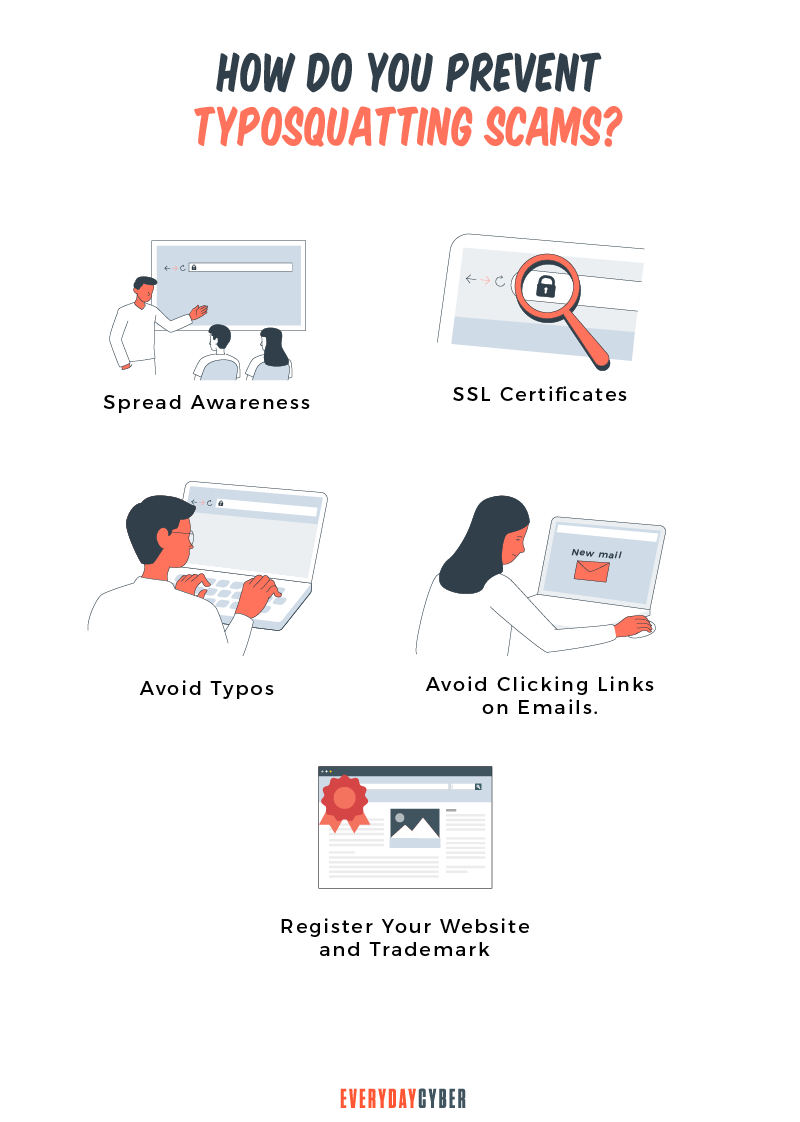
For organizations
- Consult ICANN’s Trademark Clearing House on how domain names are used
- Register typosquatted versions of your website before the crooks do and redirect them to your original site to increase traffic
- Use SSL certificates to build trust
- Notify all your staff, customers, and other relevant parties in the organization at the first hint of typosquatting
- Have suspicious websites taken down through ICANN’s Uniform Domain Name Dispute Resolution policy
Going to court to resolve domain name disputes is costly and time-consuming. There are legislation and other venues to run to, but preventive measures are always the best safeguard against typosquatting and cybersquatting.
It is not always easy to tell an O from a 0 or an I (uppercase i) from an l (lowercase L). But we need to be always vigilant about unusual changes in our systems and devices because malicious actors are always looking for new ways to take advantage of people’s mistakes.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
Why should you use a Password Manager?
How many passwords do you have? Did you know the average Internet user has 100 passwords. That's a lot of passwords to remember on a daily basis. How do manage all those password effectively - a password manager.
Piggybacking in Plain English: 6 Ways to Keep Your Neighbors from Stealing Your Wi-Fi
Stopping piggybacking all boils down to vigilance and protecting your Wi-Fi with a good VPN, antivirus software, firewall, and security patches.
12 Ways to Help Older Adults Stay Safe Online These Days
Seniors, like everyone else, have special vulnerabilities in addition to the common Internet risks. They have specific characteristics that make them vulnerable online, particularly to online fraud. Isolation and lockdowns caused by the pandemic have forced seniors to embrace technology like never before. Here are 12 ways to key seniors safe online.
BEST 10 Tips to Secure your Smart Home Devices
Smart devices are everywhere and rapidly becoming ubiquitous in our lives. Secure them or pay the price.
What is ATM Skimming and Ways to Protect Yourself
ATM skimming can lead you to losing all your money in your bank account. Here's how to protect yourself from it.
Should you use a VPN?
The Internet can be a treacherous place. One of the most important measures you can take while online is to use a virtual private network (VPN), whether you’re at your workplace, on the go, or at home. VPNs keep your online activities secure and private, especially on public Wi-Fi. But VPNs can do so much more.


