Most people perceive the dark web as some mysterious place where all sorts of shady things take place. Also called the darknet, It is often used by cybercriminals to plan and execute cybercrimes. It is also here where crooks sell illegal drugs and guns, hire hitmen, sell stolen information and many more.
That is partly true, but the dark web has its bright side, too. It is a safe community where people meet to experience free speech which otherwise they cannot get in a regulated environment. It is also a venue where journalists and whistleblowers share their stories and expose criminality.
What exactly is the dark web?
In order to understand the dark web fully, we need to know the various layers of the world wide web where people go to get information. There are three of them: the surface web, the deep web and the dark web.
The layers of the web are best illustrated in the popular iceberg model or metaphor of layers of an onion. The surface web protrudes above the water and is visible. Underneath the water lurks the deep web and dark web. They are hidden for various reasons and form the bulk of the web.
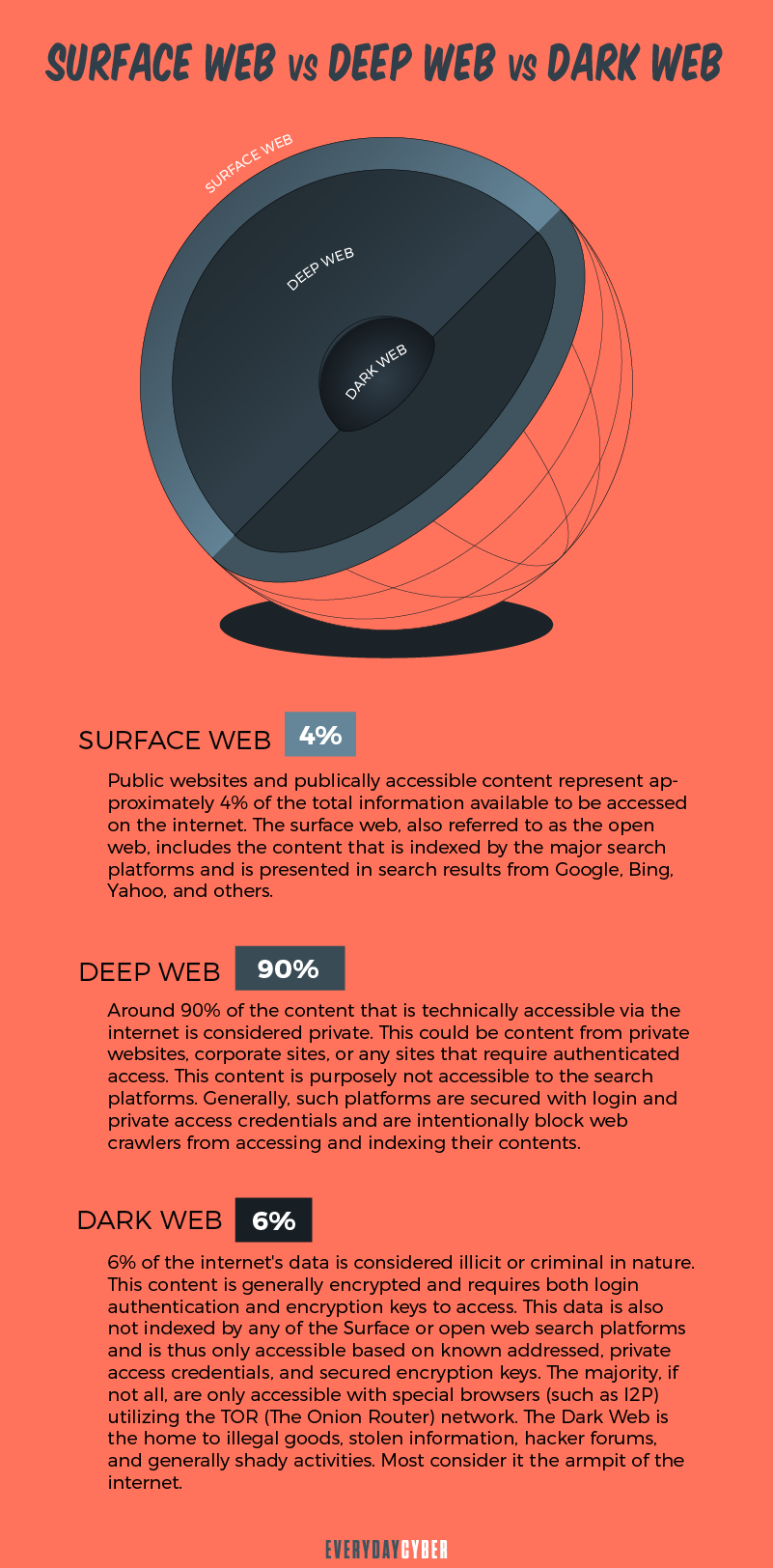
The surface web
The surface web is the part of the web that you can easily access through regular browsers, such as Google Chrome, Firefox, Safari, Internet Explorer and so on. It is the “visible” layer of the web that contains all the publicly-facing websites often registered with a “.com”, “.org” or “.net” domain.
Also called the visible web or open web, the surface web includes common sites like Google, business sites, social media sites, government sites, educational sites, news sites and the millions of blogs populating the Internet. Kaspersky estimates the surface web to be under 5% of the entire Internet, while Wikipedia puts it at 10%. A majority of experts suggest it is around 4%. [3]
The deep web
The deep web lies below the surface layer of an onion or below water level in the iceberg model. It makes up about 90% to 95% of the world wide web. It consists of websites ranging from personal blogs to corporate and public databases.
A conventional Google search will not bring you directly to the deep web. Most sites that would be considered part of the the deep web are hidden behind
- Email accounts
- Social media accounts
- Enterprise databases
- Financial accounts
- Medical and health records
- Legal information
- News and entertainment services, among many more
The dark web
The dark web is the part of the world wide web that is hardest to reach because it lies at the center of the onion or the bottom portion of the proverbial submerged iceberg. It is accessible only through special browsers, such as the TOR browser and via network paths enabled by the TOR (The Onion Network) network. It is not regulated by any government or organization and there are no rules to follow. This is why the dark web is commonly associated with illegal activities.
Dark web URLs consist of a random mix of letters and numbers and end in “.onion”. The URLs change regularly to keep them hidden. The guarantee of anonymity is the very reason why cybercriminals carry out their malicious activities in the dark web.
The dark web is not all dark, though. It is a safe haven for advocates who fear repercussions from their governments if their identities are revealed. It is also a place that promotes free speech for journalists, protection for whistleblowers and refuge for human rights activists.
How does the deep web differ from the dark web?
People often mistakenly interchange deep web with dark web. While they are both hidden, they are not the same.
The deep web is home to harmless private, public and business sites. They can be people’s password-protected accounts or the online bank accounts of consumers. They also include intranets run by enterprises and government databases. They can also be the millions of blog sites all over the Internet. They are hidden from the general public, but they can be accessed by specific users who have a relevant need for them by logging in to the accounts.
On the other hand, the dark web hides the sites on purpose. Governments use it for spy communication. Private individuals may also go to the dark web to protect themselves from oppressive regimes. Still others like journalists and whistleblowers use the dark web as a safe forum for exchanging information on criminality that they want to expose while protecting their sources. Cybercriminals also go to the dark web to carry out their trade.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How and why was the dark web created?
The dark web traces its origins to the ARPANET or Advanced Research Projects Agency Network. It was a scholarly invention in the 1960’s that made communicating between devices possible over great distances. It was funded by ARPA or Advanced Research Projects Agency, an arm of the U.S. Defense Department.
ARPANET researchers saw the usefulness of the project for more experiments, while the military also needed it during the Cold War. This led the ARPANET founders to split it into two parts in 1983. One was a military version called MILNET to be used by defense agencies for spy communication. The other was a civilian version that aimed to protect the anonymity of users. The latter formed the basis for what later became the Internet.
In 1991, the Internet became public and the decade of the Dot-Com Bubble followed. This period marked the rise of data havens as people began to see the Internet as a one-stop shop for products and services they wanted whenever and wherever they wanted them. It was only a matter of time until illegal transactions started happening online. To make them happen, promoters of these activities needed anonymity.
Finally in 2002, Tor was released as a private Internet browsing network. Its creators could not have known the widespread impact their creation would have on criminal activity. Through it, the dark web was born and thrives to this day.
How can you access the dark web?
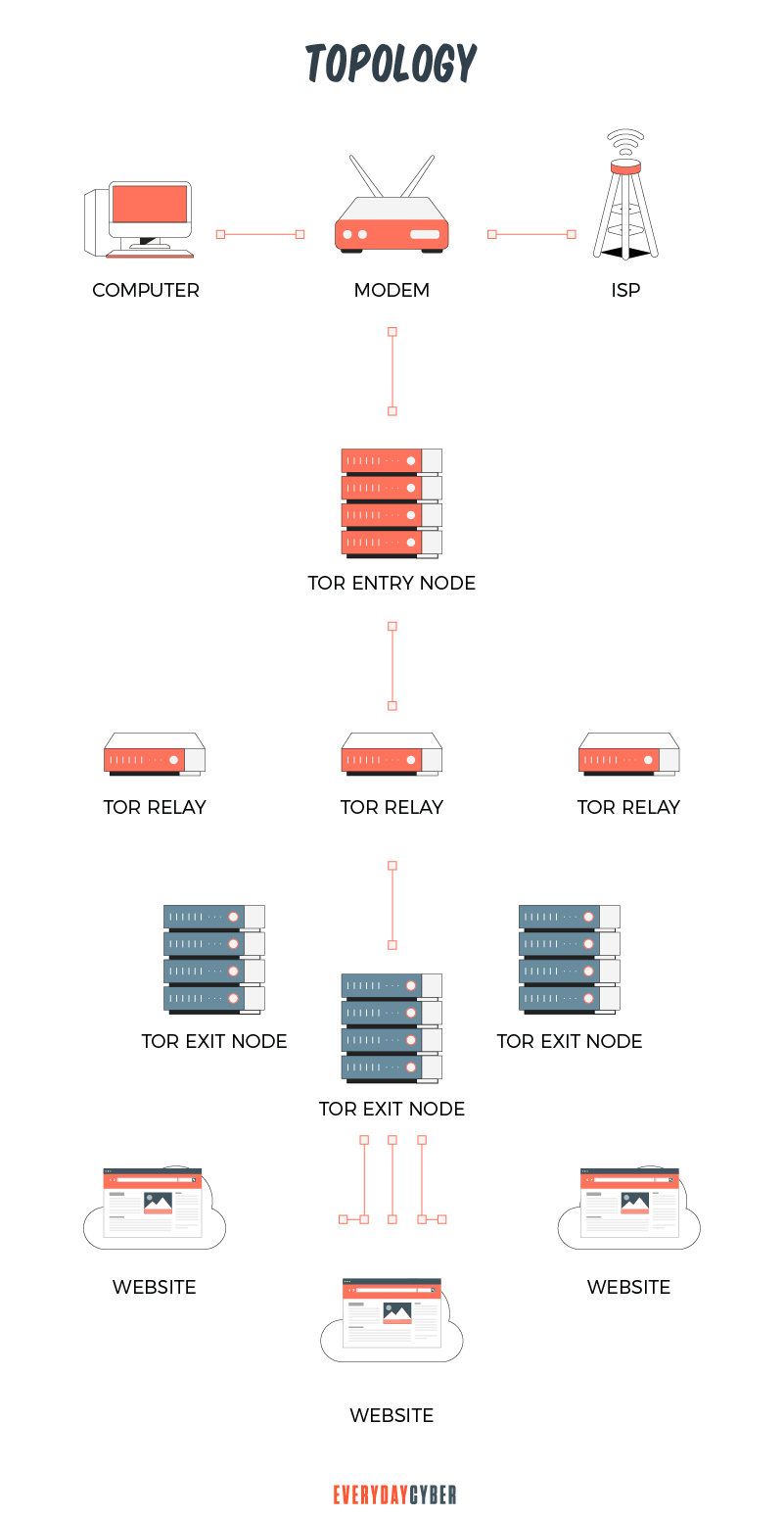
To access the dark web, you need a special anonymous browser, such as the Tor browser or I2P. It uses multi-layered encryption and thousands of volunteer-run servers called Tor relays. When you use Tor, your traffic is relayed and encrypted three times as it passes the Tor network. This is why the Tor browser is also called the Onion browser. An onion bulb consists of layers that you need to peel off in order to reach the core.
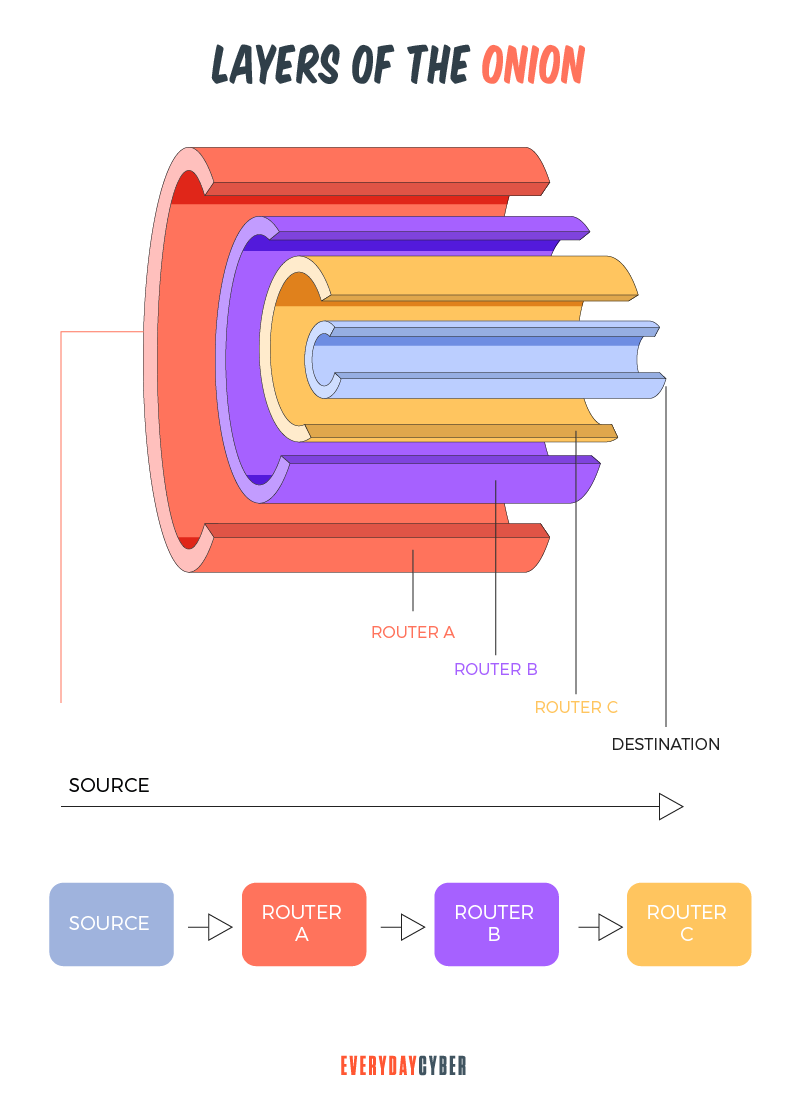
You can access the dark web by following the steps below.
The first step is to consider buying a virtual private network or VPN. While Tor hides your
The second step involves downloading and installing the Tor browser. While waiting for Tor to download, cover your webcam with a piece of dark tape to hide your physical
The third step is to sign up for a secure and untraceable email address that you will need to register for the dark web sites you’ll want to access. Here are a few you might explore:
- ProtonMail
- TORbox
- RiseUp
- Bitmessage
- Mail2Tor
When the Tor download is completed, you are ready to start your anonymous journey into the dark web. But watch your step. Carefully browse and do not divulge any personal information.
Web Hosting Secret Revealed provides a list of dark web search engines and onion websites you can choose from. Here is an initial list of search engines used on the dark web:
- DuckDuckGo
- Ahmia.fi
- DarkSearch
What can you do on the dark web?
You can enjoy the many benefits the dark web has to offer, such as the following
- Freedom of speech. People living in countries with oppressive regimes or under excessive censorship can run to the dark web to communicate freely with fellow dissidents.
- Haven for journalists and whistleblowers. The dark web is a safe place for people who want to expose criminality. Here, they can share and receive information and tips, or investigate the criminal activities of politicians and other public figures.
- Cheaper products and services. Many items are available on the dark web for less money than the open markets. The products can be cheaper because there are no price regulators and taxes to pay. The catch here is that you will need cryptocurrency to pay for the goods.
- A wealth of research materials. The dark web offers free resources, such as research papers, digital books, surveys and studies.
- Get professional advice. If you need professional advice for your sensitive medical or legal issues, for example, you might want to search the dark web.
What can criminals do on the dark web?
Criminals are leveraging the absence of regulations and regulators on the dark web to intensify their malicious campaigns. Here are what they can do that can put many people at risk:
Spread malware
Many websites on the dark web could infect your devices with malware and viruses. So be very choosy with the sites you go to and never download files from sites you don’t know and trust.
Criminal activities
The dark web is host to many criminal activities, from drug distribution to selling and buying guns. Some people also engage in sex trafficking and child pornography. Some even go to the extent of hiring murderers, while others steal and sell personal information. They can also broker the selling of counterfeit goods and digital currencies.
Cybercriminals are free to set up fraudulent sites where they can launch their phishing activities. They can also organize and implement spam campaigns and DDoS (Denial-of-Service) attacks.
Why is the dark web allowed to operate?
The dark web in itself is legal. Governments use it to conduct surveillance for criminal elements. Private individuals use it for privacy.
However, because of its extreme anonymity, many dark web site owners conduct lucrative criminal activities. It, thus, can be both beneficial and dangerous. Because it is useful to the U.S. government in multiple ways, the government cannot shut it down. And even if it does, it will need the cooperation of many countries to shut it down in its entirety.
What authorities from different countries can do is to get together and shut down the websites that are engaging in illegal activities, but not the entire dark web. It will be a concerted effort among domestic, regional, and national authorities within a certain jurisdiction.
Common dark web terms you should know
The dark web can be as confusing and mysterious as its name. The expansion of the dark web has spawned a whole new dark web language that may be unfamiliar to those who have never visited this baffling corner of the online world. The complete glossary is extensive, but below are the more common ones.
Alphabay
People flocked to Alphabay when Silk Road was shut down. It was the biggest marketplace during its time. It also closed down after a few years.
Bitcoin
Bitcoin is a virtual currency that people use to buy items from the dark web marketplaces or subscribe to sites. It is the preferred payment method because visitors can buy it anonymously. BTC is the acronym of Bitcoin.
Blockchain
Blockchain is the basic technology of Bitcoin. The Bitcoin blockchain serves as a public ledger of every Bitcoin transaction to ensure compliance. All transactions are time stamped and once entered, they cannot be erased or altered. There is no one central person or entity that has control over the transactions because information in a blockchain is distributed across a series of users or computers.
Botnet
Botnet is a network of virus-infected devices that hackers can operate simultaneously for an attack. Botnets are sold on the dark web.
Bridges
Bridges are nodes that people from countries that ban the Tor network use to access the dark web. Bridges make it appear as though people are entering the network from a different location. Some people also use bridges to hide their
Carding
Carding is the practice of stealing credit card information and selling them on the dark web. The dark web offers a lucrative market for the selling and buying of credit card information.
Clearnet
Clearnet is another name for the surface net or the traditional Internet we know. It hosts all the websites we visit everyday using traditional browsers, such as Google Chrome. Such websites can be your favorite news and entertainment sites, social media sites or the home page page of your online bank.
Cryptocurrency
Cryptocurrency is a digital or virtual currency commonly used on the dark web for both legal and illegal transactions. It has no physical form unlike paper bills and coins. It is not issued from a central point, such as a bank, but instead transacted on a peer-to-peer basis.
CP
CP means child pornography. The dark web contains many pedophile websites where members can exchange illicit material.
Darknet
Darknet is another name for the dark web.
Doxing
Doxing is the practice of exposing the
Encryption
Encryption is the process of converting data or information into a code to protect such information when they are transmitted online and while they rest in a database. The code is a string of unrecognizable characters so that even if a hacker intercepts it, he or she will not be able to understand it. The Tor browser implements three-level encryption for more improved anonymity.
HS
HS is short for hidden services. Hidden services on the dark web do not track the IP addresses of their users, nor do they reveal their own IP addresses. Communication goes on, but the channels are obscured.
Honeypot
Security experts set up honeypots to study cyberattacks and catch cybercriminals. A honeypot is a system or program that mimics something that would attract the attention of cybercriminals. For example, a bank might create a honeypot that looks like a database of its clients. When hackers attack, the bank’s
Onion Router
Onion Router is another name for Tor. With this browser, you can find websites with the “.onion” suffix on the dark web.
Red Rooms
Some people claim that you can pay a fee to gain access to special sites that show live streams of graphic activities, such as tortures or murders. Red Rooms on the dark web is a myth.
Sandboxing
Sandboxing is an added measure to boost cyber
Satoshi Nakamoto
Satoshi Nakamotot is the pseudonym of the creator of Bitcoin.
Silk Road
The infamous Silk Road is mostly known as the first successful marketplace for illegal items, such as drugs and weapons. It was shut down in 2013.
Tails
Tails or The Amnesiac Incognito Live System is an operating system you can load from a USB drive to navigate the dark web anonymously. Once you exit the system, no information will be stored on your computer.
Tor
The Tor browser is the most used browser to access the dark web.
Our final thoughts: Curiosity is understandable, but we want to stress that going to the dark web is risky if you don’t take the proper safety measures. While the dark web in itself is legal, there is criminal activity going on inside the dark web that can expose you to the dangers of this unregulated layer of the web.
So yes, you can go to the dark web, but remember to take all the necessary security precautions. And keep your personal data off that cryptic part of the online world.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Whaling?
Whale phishing is a targeted spear-phishing attack in which cybercriminals impersonate the high-level executives of an organization to send messages to lower-level company administrators in a position to do the acts being requested by the criminals on two things they want most -- money and data.
What is a WPA2 Password
Your Wi-Fi password is the network security pass you use to connect to your home network. This password is important because it protects your system from intruders.
What is a Hacker?
A hacker is someone who challenges technology to see if it can be compromised. A hacker can black hat or white hat.
What is a Website Security Certificate?
A website security certificate is a digital certificate that asserts the identity of a website. It’s a virtual file approved by an industry-trusted third-party called a certificate authority (CA)
What is a VPN?
A VPN is a virtual private connection to a VPN host server to hide your identity, address and online activity when using a public Internet connection. It does this by encrypting your data and turning them into “rubbish” so no one can make sense of it even if they get their hands on it.
What is Ransomware?
Ransomware is particularly vicious malware that infects your digital device, encrypting your data and then holding you hostage until you pay a ransom.


