Scareware is rogue malware (malicious software) that preys on people’s emotions, fears, and limited technical knowledge — using social engineering techniques to persuade victims to compromise their
Scareware most often presents itself through fake virus alerts, deceptive software updates, or sham malware removal tools that scare you into believing your device is infected or needs updating. The criminals fool you into clicking the link or ‘download’ button, thinking you’re getting genuine

The bad actors know that a human tendency is to trust others, particularly those who appear to be in authority positions. Cybercriminals recognized that this is true of human behavior on the Internet, just like in real life. So, they exploit this quality.
How does Scareware work?
The most common method is when you’re browsing online, and a pop-up ad appears on your screen, warning you of some bad event – such as your device is infected with dozens of viruses. The ad claims that it will immediately eliminate the viruses if you buy and download their
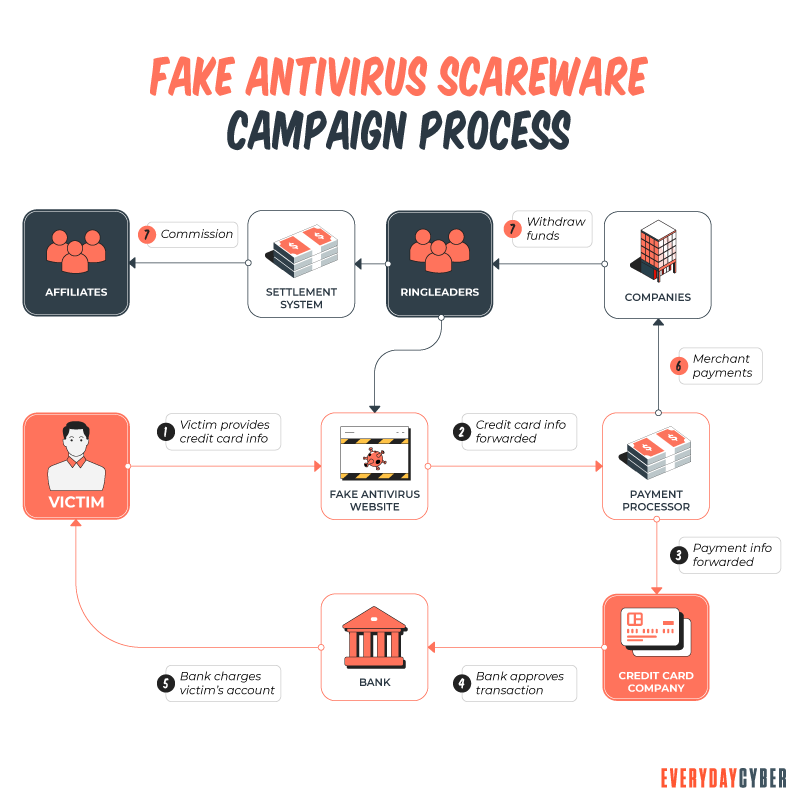
If you’ve experienced this, you’ve been hit with a scareware attack. Scareware is a scam in which bad actors attempt to access your financial or payment (credit card) information and often access your device by tricking you into buying fake
How do I know if I am hit with Scareware?
The most practical option to protect yourself is by recognizing the warning signs of Scareware.
The pop-up ad is especially ominous
The scammers want to scare you so that you’re more likely to act and purchase their fake product. They intentionally use ominous warnings that your computer is infected with hundreds of viruses, or that these viruses will immediately cause your computer to crash to persuade you to act – it is a form of social engineering. The more threatening and scarier the claims are, the more likely you will react to the scareware the way they want.
The ads push you to act fast
Urgency is a technique used by marketers to cause action. Cybercriminals are creative, and they leverage the same methods that legitimate individuals use to influence behavior. The bad actors behind these attacks want you to quickly purchase and install their malware before you have a chance to think about it. If a pop-up demands that you act now, it’s probably Scareware.
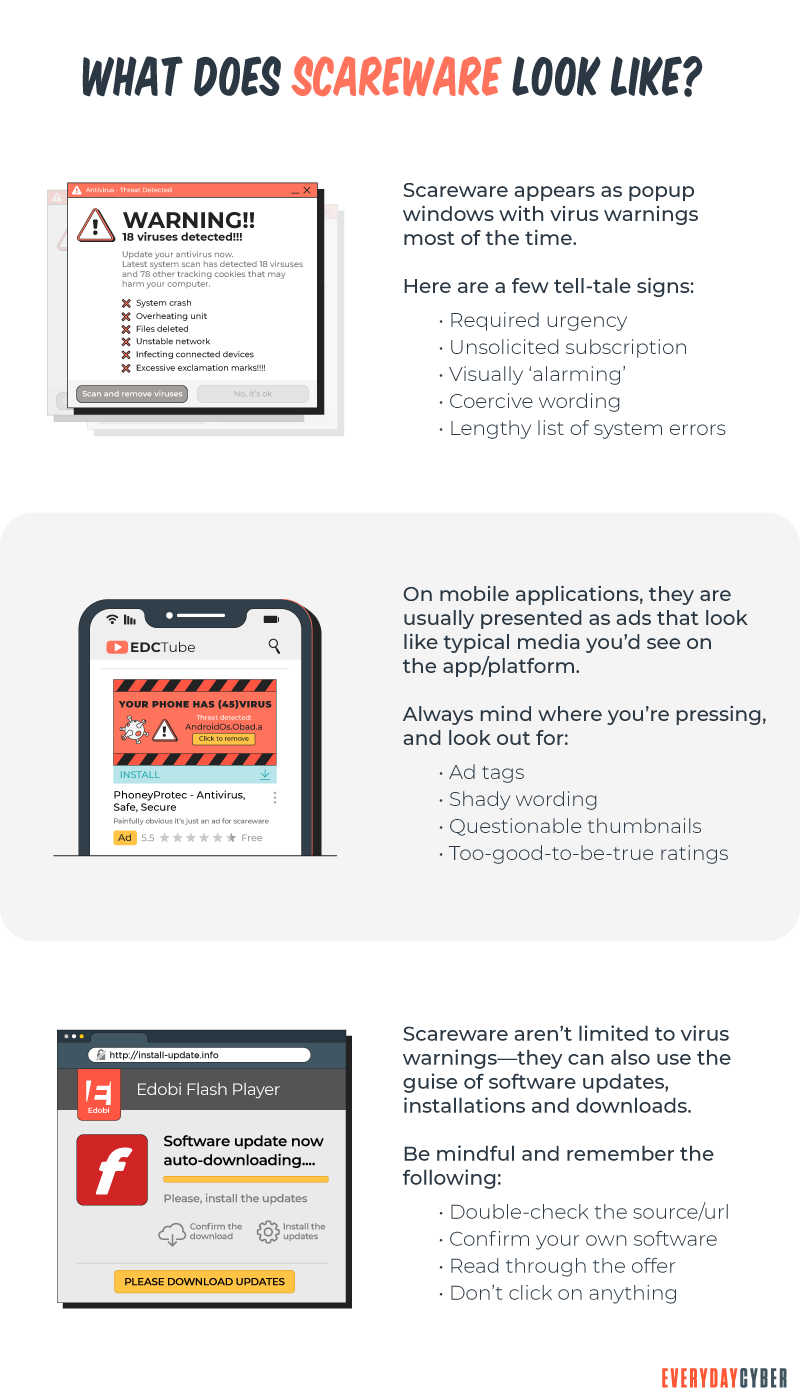
You can’t seem to close the pop-ups
They want their scareware pop-ups to remain on your device’s screen as long as possible. So, they make it difficult to get rid of the popups from your screen. If it’s difficult to close the pop-up ads, or if clicking on the “X” button to close them instead brings up more warnings, you’re likely dealing with scareware.
It’s a company you have never heard of
Most of the
Some known fake
They appear to “scan” your device for viruses
To make their warnings seem even scarier, many of these pop-ups will seemingly start scanning your computer for viruses and report a list of the dozens or hundreds of viruses they claim to have uncovered. They are not scanning your device, and the results they’re showing are bogus.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Best practices to avoid Scareware?
Here’s how you can help keep scareware at bay.
- Keep your browser updated – Most browsers have built-in popup and ad blockers. Keeping your browser(s) updated is one of the best ways to minimize being hit by scareware.
- Turn pop-up blockers turned on – Stopping or shutting off popups will prevent your screen from being filled with advertisements for fake
security programs.
- Install a quality antivirus/antimalware tool on your devices – A top priority should be to install a quality
antivirus /antimalware program from a trusted company. They offer the best protection against all forms of viruses, malware and will protect your devices from scareware. - If you get pop-ups, RESIST the urge to CLICK – Good cybersecurity practices include “Never Click” on any links or “download” buttons on pop-ups. If you are really worried that your computer is infected, do a Google search on the company behind the pop-up you’ve received. You’ll quickly discover whether that company is offering legitimate or scam
security software.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is DNS Hijacking?
DNS hijacking is no laughing matter. It is a serious security threat that is consuming the cyber world. The critical role of DNS for network security has made a primary target for facilitating mass data theft.
What is Pharming?
Pharming is cybercriminals “slight of hand” cyber attack. Redirecting you to a fake website imitating a legitimate site so they can steal your login info, financial data, and more.
What is Typosquatting?
Cybercriminals target visitors that accidentally mistype website addresses directly into their browsers. They use typosquatting, also called URL hijacking, to deceive visitors and lead them to malicious sites they themselves have set up.
What is a Remote Access Trojan (RAT)?
A remote access Trojan is a software used by hackers to gain unauthorized access and remote control on a user’s computer or mobile device, including mouse and keyboard manipulation.
What is Spear Phishing?
Spear phishing is a targeted cyberattack to steal your information. You should be aware of the dangers of this and how to address them.
What is Hacking?
Hacking is an old game in the cyberworld with ever changing players and techniques. It may be done with good intentions or malicious motives. It is growing rapidly because of the proliferation of devices.