Encryption Is all about keeping our data safe from unauthorized access. It has long been used thousands of years ago, mostly by the ancient rulers to protect their military secrets.
Today, encryption is not the exclusive turf of militaries and governments. Our personal, professional and business lives are constantly under threat from privacy intrusion, often with malicious intent. Our daily online lives greatly depend on encryption for data protection.
Definition of encryption
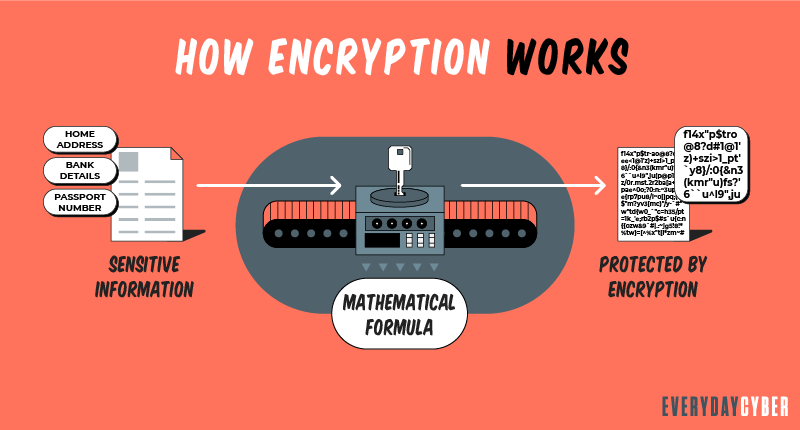
Encryption is the process of converting data into a code so that only people with access to a secret key, called a decryption key, can read it. It is a way of scrambling data so that only authorized parties can understand the information.
Unencrypted data is called plaintext, while encrypted data is called ciphertext. Technically, encryption transforms human-readable plaintext into incomprehensible ciphertext. The process of encoding and decoding data is called cryptography.
The formulas used in encryption are called algorithms or ciphers. A cipher includes a variable, called a key, to make encryption effective and produce a unique output. To an unintended recipient, the encrypted data will appear as a meaningless mix of characters and symbols.
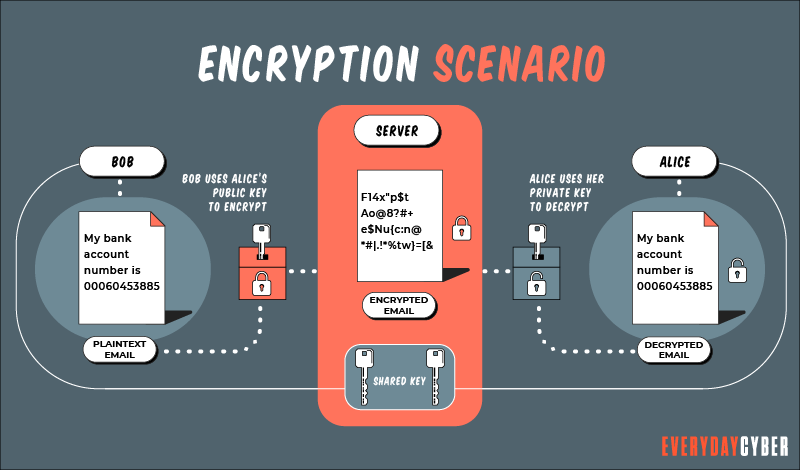
If an encrypted message is hijacked by an unauthorized party, the snooper has to guess which cipher and key the sender used. The time, difficulty and the need for massive computing resources are what make encryption valuable.
Earliest encryption methods
Caesar’s Cipher
Julius Caesar of the Great Roman Empire developed a simple code to send secure messages to his troops. The method involved substituting certain letters for other letters at a predetermined distance or number in the form of an offset or rotation.
For example, in an offset of three, “A” would be written as “D”, “B” would be written as “E” and “C” would be written as “F”, as can be seen in this illustration:

Source: Matt_Crypto/Wikimedia Commons
The modern day “ROT13” or “rotation 13” cipher derives its underlying principle from Caesar’s Cipher. ROT13 is a simple letter substitution of an English letter with the one 13 places forward or backward along the alphabet. It is considered a weak encryption method and is often used in online forums as a means of hiding spoilers.
The Scytale
The Spartans of ancient Greece used a wooden rod called scytale where they would tightly wrap around a strip of parchment where they write their messages. Uncoiled and without a scytale of the right dimensions, the writing on the parchment made no sense.
A messenger would deliver the parchment to the recipient. The recipient would need to have his or her own matching scytale where he or she would wrap around the parchment to be able to read the message.

Source: Luringen/Wikimedia Commons
The scytale’s contribution to modern encryption is the need for both sender and recipient to know in advance the type of encryption system used and how to use it with matching tools.
The Polybius Square
The Polybius Square is an early Greek invention consisting of a five-by-five or six-by-six grid of letters. A letter was referenced by its coordinates and the resulting number combination is the code for that letter. The resulting number combinations that form the coordinates could go either way: vertical to horizontal, or horizontal to vertical.

Source: https://crypto.interactive-maths.com
In the illustration above representing a standard Polybius square, the resulting codes using the vertical to horizontal coordinates would be:
- “11” for A
- “21” for B
- “32” for H
- “42” for I/J
- “14” for Q
- “55” for Z and so on
Using the horizontal to vertical coordinates, the resulting codes for the same letters would be:
- “11” for A
- “12” for B
- “23” for H
- “24” for I/J
- “41” for Q
- “55” for Z and so on
The encryption is standard and has no key; thus, it can be easily broken. A good remedy is to create a mixed square that contains a keyword, or another rule such as reversing or shifting the alphabet.
In the illustration below, the keyword is POLYBI/JUS. The letters of the keyword go to the first squares in consecutive horizontal order. Then the rest of the squares are filled with the remaining alphabets.
 Source: https://crypto.interactive-maths.com
Source: https://crypto.interactive-maths.com
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
How is encryption used?
Encryption is used to secure data at rest and data in transit. It has three major components: data, encryption software and key management. On your laptop for instance it stores and runs all three components. In application systems, however, the three components are stored and run in separate places so that the compromise of one component does not result in the compromise of the entire system.
You may not notice it, but you probably encounter encryption every day. Every time you purchase items online or send an email, your smartphone or laptop uses encryption to protect the information being relayed.
Most of the connections you make to major websites are encrypted, usually indicated by HTTPS and/or a padlock in your browser’s URL bar. These may include your WhatsApp or Facebook messages or an appointment to your dentist.
Businesses are increasingly dependent on encryption to protect their customers’ data, applications and other sensitive information to minimize reputational damage in case of data breach. A vast amount of encryption is especially used by communication and financial systems. With the emergence of cryptocurrency technologies, encryption is becoming more and more important.
How does encryption work?
Encryption involves the encoding and decoding of data in order to preserve its integrity and confidentiality. When the sender transmits information, he or she converts plaintext into ciphertext. This is encoding or encrypting. When the intended recipient accesses the message, he or she translates ciphertext back into plaintext to unlock the message. This is called decoding or decrypting.
Both the sender and the recipient use a secret key, which is used as input into a set of algorithms to scramble and unscramble data back from and to readable form. Encryption uses two key systems that are random and unique.
Symmetric encryption vs. asymmetric encryption
Symmetric encryption, often referred to as Private Key Encryption, uses one key for both encoding and decoding. It serves as a shared key by both sender and recipient to encode and decode data, respectively. Symmetric algorithms are less complex and generally relatively faster to implement, making it the preferred method for transmitting bulk data.
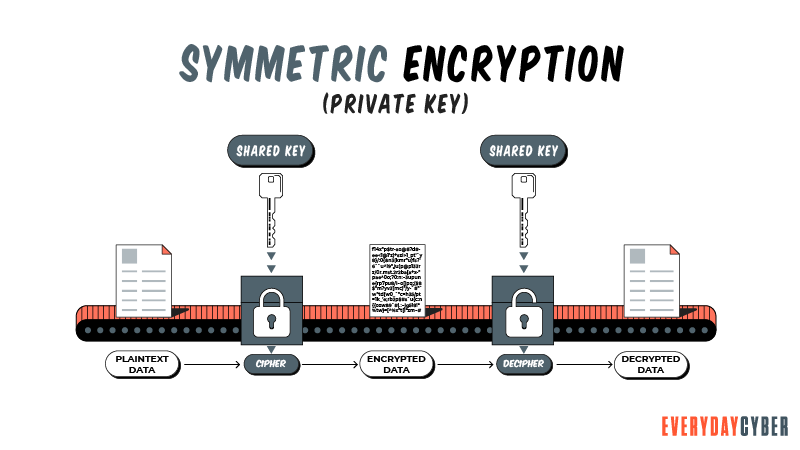
Symmetric encryption, often referred to as Private Key Encryption, uses one key for both encoding and decoding. It serves as a shared key by both sender and recipient to encode and decode data, respectively. Symmetric algorithms are less complex and generally faster to implement, making it the preferred method for transmitting bulk data.
Symmetric encryption keys use block ciphers or stream ciphers. The length of the keys are shorter than those of asymmetric keys. For example, the advanced encryption standard (AES) uses a block size of 128-, 192- or
Asymmetric encryption, generally referred to as Public Key Encryption, uses two encryption keys. The first key is a public key used to encrypt data and is accessible to everyone. The second key is a private key used to decrypt a message. It is shared by only the message initiator and the recipient and not shared by everyone.
Asymmetric encryption is more complicated, time-consuming and has longer keys compared to symmetric encryption, but it offers more robust
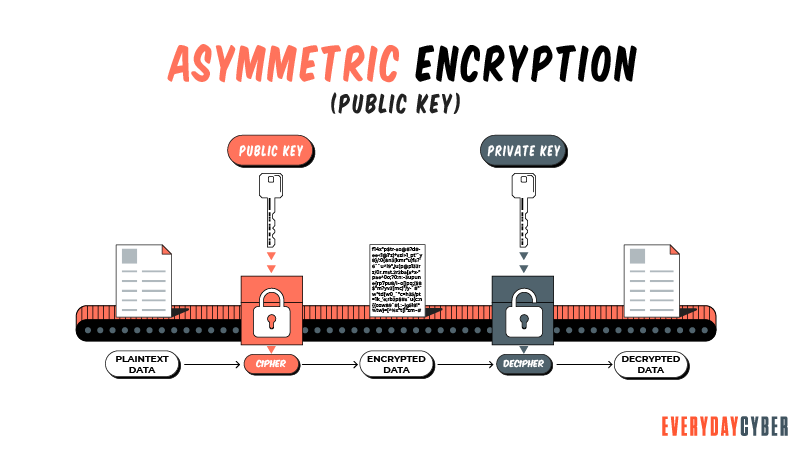
Why is encryption important
Data
Modern businesses store and use massive amounts of data about their employees and customers. They must make it their responsibility to protect this data to maintain their business reputation or avoid legal penalties.
Compliance is another reason why encryption is important. Businesses must comply with laws and regulations that apply to their industry or business sector. For example, there are specific laws that protect health information, student records, legal documents, consumer’s data and more.
What are the types of encryption?
Encryption types vary to suit particular use cases, infrastructure and other benchmarks. Here are the common types.
Bring your own encryption (BYOE)
The BYOE model enables cloud service customers to use their own encryption software and manage their own encryption keys. Amazon and Microsoft have introduced cloud-hosted key management systems while an increasing number of cloud service providers (CSPs) are finding new ways of handing over key management control to end users.
To further strengthen the BYOE system, CSPs are building on a “bring your own key” (BYOK) mechanism. This would allow owners of data to store their keys in their own premises, away from the cloud, which the CSPs themselves cannot access.
Encryption as a service (EaaS)
Encryption as a Service or EaaS provides a way for cloud service customers who lack the resources to manage encryption themselves to take advantage of the
Cloud storage encryption
In cloud storage encryption, cloud storage providers offer to encrypt data with encryption algorithms and then store them in their cloud storage facilities. The cloud customers do the encryption themselves just like they do in-house encryption, but they must comply with the cloud provider’s policies and procedures on encryption and key management.
Deniable encryption
Deniable encryption is a type of encryption that enables encrypted data to be decrypted in two or more ways with the use of two or more keys. It allows the sender of the encrypted message to deny sending the message by using a decoy key to mislead or misinform the recipient, especially if the sender anticipates unauthorized interception of the message.
End-to-end encryption (E2EE)
The end-to-end encryption model ensures that unauthorized parties cannot intercept the encrypted communication between the sender and the recipient. It uses an encrypted communication circuit where the client software encrypts the data being transmitted before being passed to a web client and decrypted only by the recipient.
Network-level encryption
Network-level encryption is done through Internet Protocol
Column-level encryption
Column-level encryption is suitable for database encryption. It allows users to select specific pieces of information to be encrypted instead of encrypting the entire database. Each cell in a particular column can be accessed using the same password.
For example, a database may contain sensitive information such as date of birth, home address, Social
Field-level encryption
This type of encryption enables users to encrypt data in specific fields on a webpage. These fields may be for bank account numbers, credit card numbers, wages, Social
Link-level encryption
Link-level encryption ensures that data is encrypted and decrypted from link to link. This means that data encrypts when it leaves a host and decrypts when it reaches the next link. It re-encrypts when it leaves for the next relay point and decrypts when it arrives at the next. This process is repeated until it reaches its final recipient.
Full-disk encryption (FDE)
Full-disk encryption happens at the hardware level. It automatically converts data on a disk, such as a hard drive, into incomprehensible form so that any one who does not have access to the authentication key cannot read it. Even if the hard drive is transferred to another computer, the data remains inaccessible in readable form.
Homomorphic encryption
This type of encryption makes it possible to analyze and work on encrypted data as if it were in its original form without revealing the data to anyone. For example, if you are searching for the best pizza house over the Internet, you use volumes of data as you access various websites. None of the information would be visible to these websites or any other third parties, such as service providers like Google.
Like other encryption models, homomorphic encryption uses a public key to encrypt data. However, it uses an algebraic system that other encryption types don’t use. This algebraic system allows the user to work on the data in its encrypted form. Only the party with the matching private key can access the unencrypted data after the manipulation is completed.
Hypertext Transfer Protocol Secure (HTTPS) encryption
HTTPS encryption ensures that all data that a web server sends are encrypted. It also prevents third parties from injecting content into web pages, such as unauthorized advertisements, without the consent of the website owner. To be able to do this, a public key certificate must be installed.
Quantum encryption
Quantum cryptography is based on the complex principles of quantum mechanics that an ordinary reader may not be able to understand clearly. Specifically, the principle of uncertainty states that the location and momentum of a particle, the two identifying properties of that particle, cannot be measured without changing the values of those properties.
Quantum cryptography uses a series of light particles called photons to transmit data from one location to another over a fiber optic cable. Any attempt to access quantum-encoded data will cause a change in the data. As a result, the change alerts the authorized parties that an intrusion has occurred.
What are encryption algorithms?
Also called a cipher, an algorithm is a set of rules or instructions for the encryption process. The overall effectiveness of an algorithm depends on the key length, functionality and other unique features. However, the strength of an algorithm is usually directly proportional to its length.
Encryption algorithms come in various forms, key sizes, strengths, methods and complexities.. Here are some common types:
Advanced encryption standard (AES)
Also known as Rijndael, AES is a symmetric block cipher approved by the U.S. National
The AES algorithm employs three different key lengths with several possible combinations as follows:
- 128-bit with 3.4 X 10 to the 38th power combinations
- 192-bit with 6.2 X 10 to the 57th power combinations
- 256-bit with 1.1 X 10 to the 77th power combinations
Rivest-Shamir-Adleman (RSA)
Named after its inventors Ronald Rivest, Adi Shamir and Leonard Adleman, RSA is a type of asymmetric encryption that involves a public key and a private key. The private key is used to generate digital signatures and the public key is used to verify digital signatures.
Many protocols, such as Secure Shell (SSH), OpenPGP and Secure Sockets Layer/TLS, depend on RSA for encryption. However, RSA is not usually used for long messages because of its resource-intensive structure.
Data encryption standard (DES)
DES is an outdated data encryption method and was replaced by the AES algorithm. DES uses one key for encryption and decryption, so both the sender and the receiver share the same key.
Triple DES (3DES)
The triple data encryption standard provides block cipher algorithms three times to each data block to ensure stronger
Diffie-Hellman key exchange
Also called exponential key exchange, Diffie-Hellman key exchange is an encryption method that uses numbers raised to specific powers to produce decryption keys that are mathematically overwhelming to break. It allows two parties to create a shared key to be used for secure communication in an unsecured channel.
SNOW
SNOW is a word-based stream cipher that works on 128-bit and
- SNOW 1.0 used to identify new ciphers for widespread adoption
- SNOW 2.0 that solved the weaknesses of SNOW 1.0 and was later chosen for the ISO/IEC standard
- SNOW 3.0 which was chosen for the 3GPP algorithms UAE2 for confidentiality and UIA2 for integrity, respectively
Elliptic curve cryptography (ECC)
Elliptic curve cryptography uses the algebraic functions of elliptic curves to generate key pairs for public key encryption, making them trickier to break. It is gaining popularity as an alternative for RSA because of its smaller key size and lesser memory requirement. It is a good choice for the Internet of Things (IoT) devices and other machines with limited computing resources.
Blowfish
Blowfish is a symmetric encryption algorithm that uses a single key to encrypt and decrypt data. It uses a block size of 64 which is considered not so secure. Blowfish uses a lesser amount of operations compared to other encryption algorithms. It is not patented and can be used by anyone for free.
Although it is not as secure as other encryption algorithms, it is widely used in the encryption of password management, file/disk encryption, email encryption, operating system encryption and backup tools encryption.
Twofish
Twofish is the predecessor of Blowfish. It is a symmetric encryption algorithm that uses a block size of 128-bits and key sizes of up to
Quantum key distribution (QKD)
Quantum key distribution is an encryption method which generates encryption keys using a pair of intertwined photons that are transmitted separately to the message. This enables the sender and receiver to know whether the encryption key has been ambushed or changed before the message even arrives.
In the quantum dimension, merely observing the transmitted data changes it. Once the parties determine that the message has not been intercepted and is secure, permission is given to transmit it over a public Internet channel.
What are the challenges of encryption?
One of the biggest challenges of encryption is key management. Keys have to reside within the environment for easy access when needed, but attackers have a pretty good idea where to look.
The human factor is also the weakest link in encryption key management. If not monitored, properly configured and limited to authorized individuals, key management can be an attack vector for cyber thieves.
Encryption is often paired with other
Can encryption be broken?
In this world, nothing is absolute or perfect. So yes, encryption can be broken by brute force, especially if the cipher is weak. However, it will take wildly impractical lengths of time to crack longer ciphers.
I would like to use the computation of Lamont Wood, a freelance technology writer, in his featured article at Computerworld. The number of possible producible keys in a 128-bit cipher with 3.4 X 10 to the 38th power would be 340 undecillion. An undecillion is the number 1 followed by 36 zeros, so 340 undecillion would be 340,000,000,000,000,000,000,000,000,000,000,000,000.
Assuming a machine has enough computing power to test one trillion keys per second, testing all possible combinations would take 10.79 quintillion years. This is crazily improbable to do. That said, using
quantum technology with the same throughput as current computing technology, it would take about six months to test all possible combinations of a 128-bit cipher. Comparatively , for a quantum computer to break a
Aside from brute force, what can hackers do? They can employ side-channel attacks, which do not attack the actual cipher but an error in design or execution. They may also attempt to use cryptanalysis, the technique of finding a weakness in the cipher that can be exploited.
Data encryption best practices
Unencrypted data is at risk and the threat is real. Apply the following basic principles if you want to encrypt data securely and efficiently:
Keep your encryption key(s) secure
It can be easy to make mistakes that unauthorized parties can exploit. For example, if you store your encryption key in an unencrypted file on your computer, someone could find it and use it for malicious activities.
To keep your encryption key(s) secure, separate them from the data. Separate key ownership duties and limit access of the key(s) to authorized persons.
Rotate or change your keys regularly.
Encrypt all sensitive data
No matter where they are stored or transmitted, encrypt all types of sensitive data so you make it much harder for attackers, who breach your system, from doing something bad. Many companies have been breached, with important data compromised, simply because they left those data unencrypted and crooks found a way to access them.
Review data encryption performance
Data encryption involves assessing the effectiveness of your encryption process to ensure that resources are used efficiently. Is it taking too long to encrypt data? The longer data remains unencrypted, the better the chance for intruders to attack.
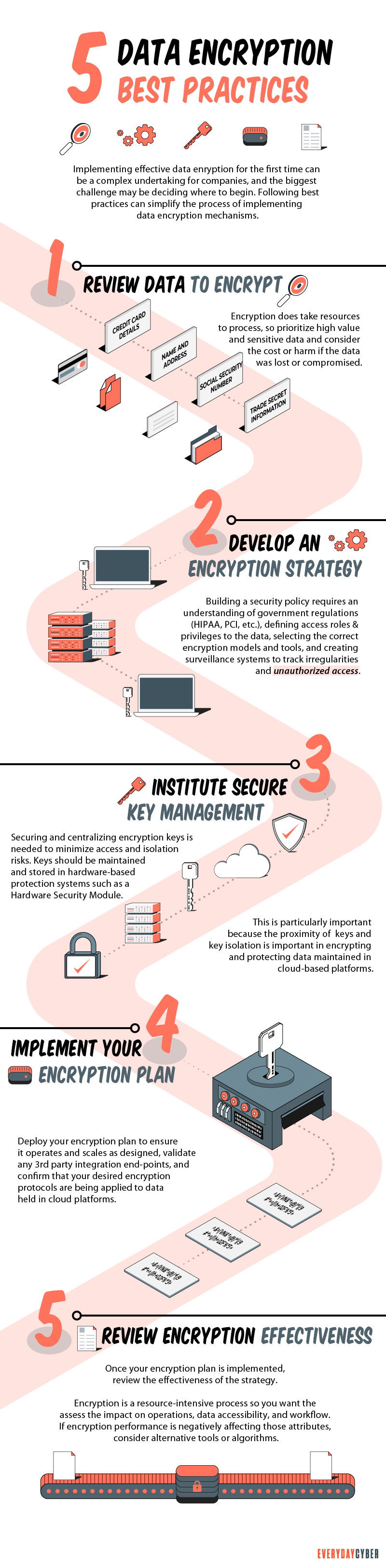
Is your encryption method consuming too much computing time and memory? Maybe it is time to consider adjusting the settings of your encryption tools or switching to a different algorithm.
Choose multi-layer security
Encryption alone, especially a weak one, cannot give your data full protection. Every encryption strategy should include layers of anti-malware protection capable of detecting and mitigating malicious code. Device and application control should also be integrated to reduce the opportunities criminals have to access and steal sensitive data.
Final thought
Encryption is the heart of data
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is the Dark Web?
The dark web is the part of the world wide web that is hardest to reach because it lies at the center of the onion or the bottom portion of the proverbial submerged iceberg.
What is Malware?
Malware or “malicious software” is a cybersecurity term used to describe software that steals your data, spies on you, damages your devices, and generally causes chaos and destruction.
What is Social Engineering?
Social Engineering in the digital world is the intentional deception and manipulation of victims to cause the release and sharing of confidential information used to commit fraud and other cybercrimes.
What is a WPA2 Password
Your Wi-Fi password is the network security pass you use to connect to your home network. This password is important because it protects your system from intruders.
The #1 Cyber Threat Small Businesses are Facing
Phishing attacks are the most widespread and most damaging threat to small businesses, accounting for 90% of all cyber security breaches.
5 Powerful Ways to Protect Your Business from Vishing
Vishing is a cybercrime that’s threatening people all over the world. And it’s not expected to go away anytime soon.