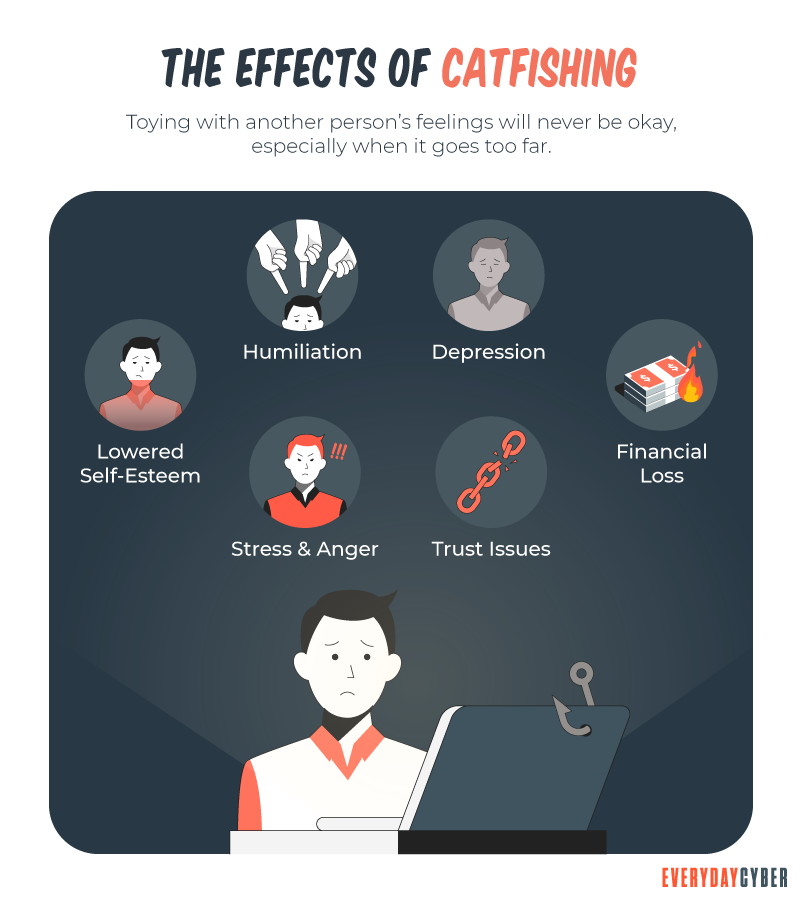
Not all online scams are trying to install adware, spyware, or other malware onto your device. Often scams aren’t a virus burrowing into your hard drive but a fake lover taking root in your heart. If you ever used online dating or other types of social media services, or you might someday, make sure to protect your heart and your bank account from catfishing.

Catfishing is fraud or abuse where someone creates a false online
What are the catfishing red flags to watch for?
Catfishers can be very sneaking and can be very convincing.
If you meet someone through a dating site or social media, proceed with caution. Watch for the common signs that the person you’re interacting with may not be who they say they are.
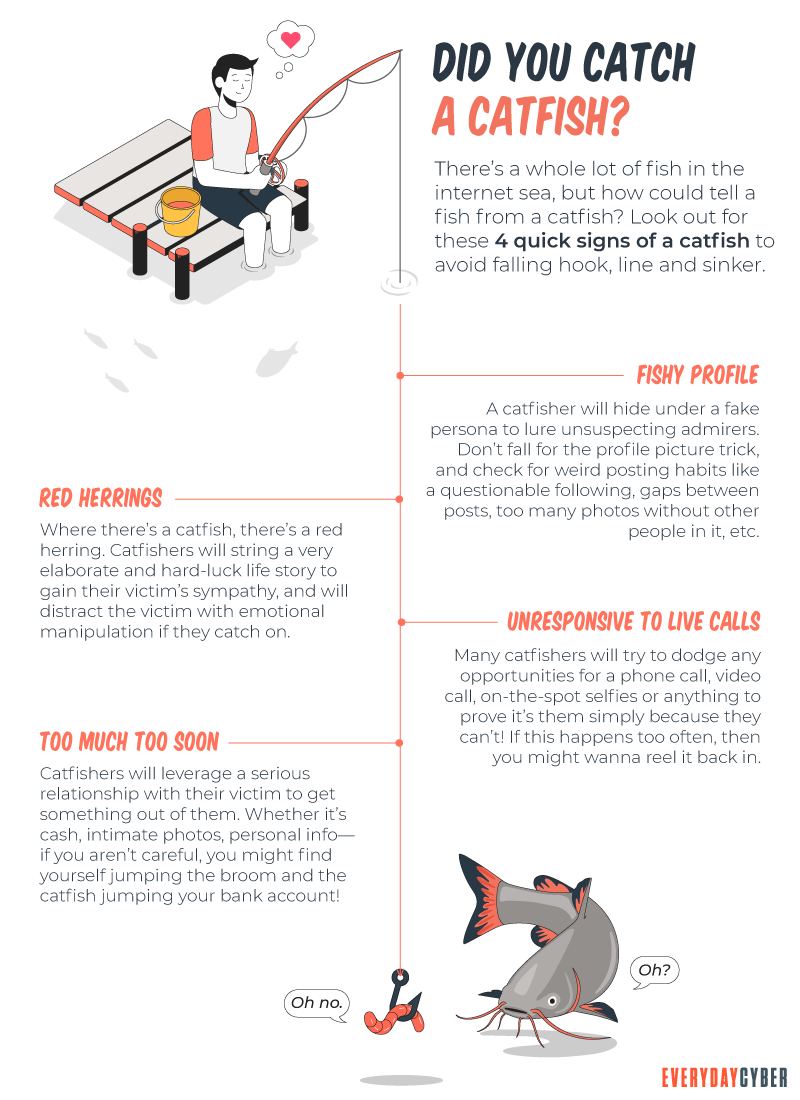
The person seems too good to be true – If the new love interest appears to be attractive, rich, with a fancy job, it may all be fake. Many catfishers claim to have a job that has them constantly on the road, as it can be an easy cover for why they can’t meet you in person.
They move fast – Pushing the relationship forward unusually fast is an often-used technique; if this is happening, pump the breaks. Be wary about sharing very personal details too quickly (especially about issues that might garner your sympathy) or professing their feelings to you way too early.
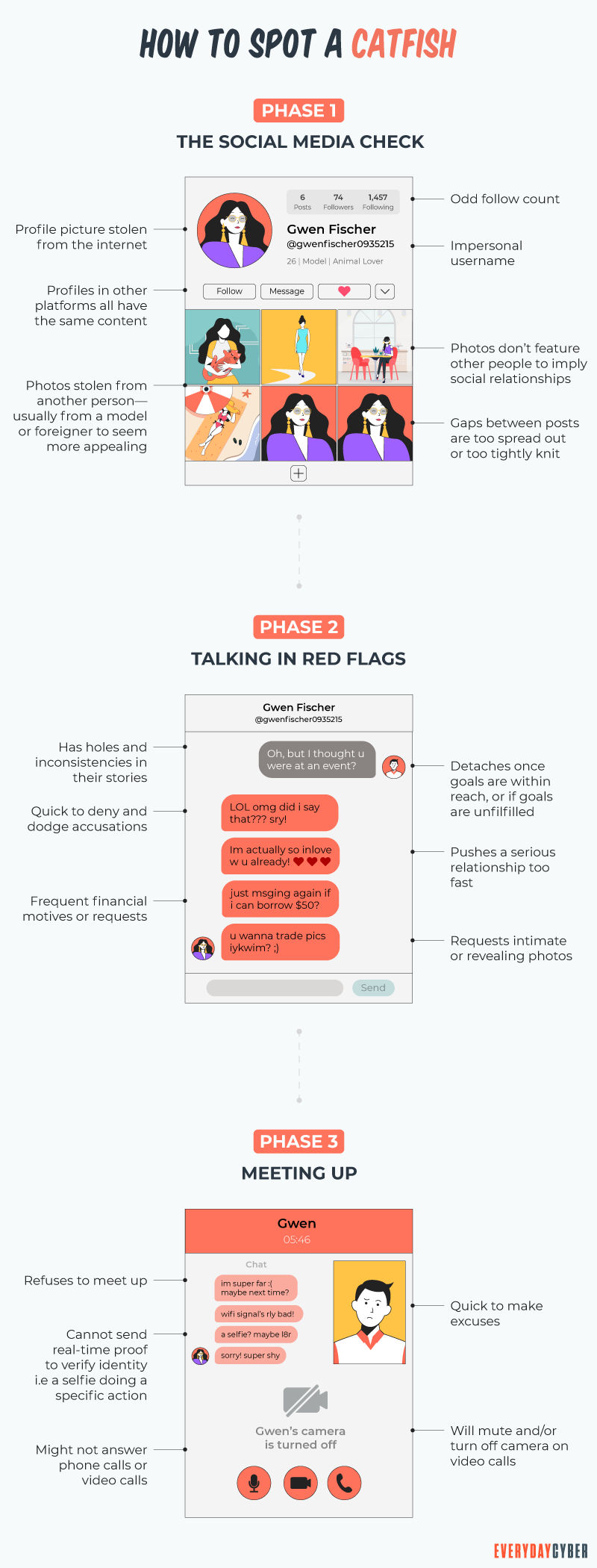
Their story has holes – Watch for inconsistencies in their story. Do details about their job, hobbies, or family seem to change frequently? Liars tend to make mistakes or forget what they said previously. Check out how they write — for example, do they come across as a native English speaker, but their writing is full of mistakes? This could be a huge red flag that they aren’t who they say they are.
The individual has a minimal presence on social media – Check the individual out on social media and see how many friends and photos they have. If the account appears new, it could signal that they created the account just for a fake persona.
They seem to have everything in common with you – If they seem to agree with everything you say or suggest they have everything in common with you, this could be another sign that they are lying to establish common ground and build an artificial sense of trust.
What can I do to avoid being catfished?
You can do several things to protect yourself and validate whether the individual is real or possibly a catfisher.
- Ask to do a video chat via Skype, Google Duo, Zoom, or some other video chat services. If excuses start, you can bet they are catfishers – and you won’t hear from them again.
- Meet them in person. Nothing provides validation than seeing someone face to face.
- Do a Google reverse image search against the online photo they show on a dating site. You may find the same image on multiple online profiles with different names.
- Check out their online photos. Are they primarily selfies or studio shots, but none have other friends in them, show no family, or have no real context, like a vacation. That can big sign that this is a con job.
The best strategies to avoid being catfished are being skeptical, using the techniques above to confirm the person you are connecting with, is who they say they are, and just being cautious.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Hacking?
Hacking is an old game in the cyberworld with ever changing players and techniques. It may be done with good intentions or malicious motives. It is growing rapidly because of the proliferation of devices.
What is Digital Identity?
Your digital identity is your set of unique features and characteristics identifiable to you. It is all data that can be traced back to you.
What is Encryption?
Encryption is the process of scrambling data – text, audio, video into an unreadable form, known as ciphertext, so only authorized resources can decode/access it.
Why should you use a Password Manager?
How many passwords do you have? Did you know the average Internet user has 100 passwords. That's a lot of passwords to remember on a daily basis. How do manage all those password effectively - a password manager.
What you should know about Chatbots And cybersecurity
Chatbots are conversational assistants that automate repetitive chores. We like them because they assist them in completing jobs swiftly and without the need for human interaction. But an unprotected chatbot can be a security problem. Hackers can use defenseless AI chatbots to carry out nefarious activities. Read to learn more.
What is a certificate authority CA and what do they do?
Certificate authorities are the guardians of digital identity. They come in both public and private capacities. Certificates issued by them are trusted because information are validated from the requester’s own records and/or from third party sources.

