Rootkits first appeared in the 1990s, targeting Linux systems. Up until the late 1990’s, rootkits were mainly a Unix/Linux phenomenon, after which a Windows rootkit was spotted. It was followed by other rootkits and from then on, rootkits have become a common but challenging cyber threat.
What is a rootkit?
Historically, a rootkit was a set of tools that provided administrative level access to a network. It is a combination of the two words “root” and “kit”. Root referred to the administrative function on Linux and Unix systems while kit was the software component that ran the tool.
Today, rootkit connotes a negative meaning. It is a nearly invisible and dangerous type of malware that allows hackers access to computers without the knowledge of the owners. It is designed in such a way that it can remain in a network or on a computer system undetected for an extended period of time. Only if discovered and removed by the affected victim or by the cyber criminal themselves, rootkits can remain resident on the affected system or network for extended periods. They are often associated with viruses, worms, and Trojans.
What do rootkits do?
Once a rootkit attacks a computer, it takes control of administrative functions without being detected. It can modify anything an administrator can, such as the following:
- Hide malware – A rootkit hides itself and other types of malware within the device, making it harder to remove them.
- Provide remote access – Rootkits enable hackers to gain remote access to operating systems while avoiding detection.
- Alter or shut off
security programs – Many rootkits tamper withsecurity programs, or turn them off entirely, to conceal themselves and make it hard to catch them.
- Gather data – Rootkits allow cybercriminals to steal data, particularly personal data, for fraudulent motives.
- Set up a backdoor – A backdoor provides hackers a method of bypassing normal authentication processes and
security systems. Hackers can then keep coming back undetected to carry out their activities unimpeded.
- Violate your privacy – Rootkits help hackers eavesdrop on you by tracking your traffic, recording your keystrokes, reading your emails and many more. Often to steal personal and sensitive information such as banking credentials.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
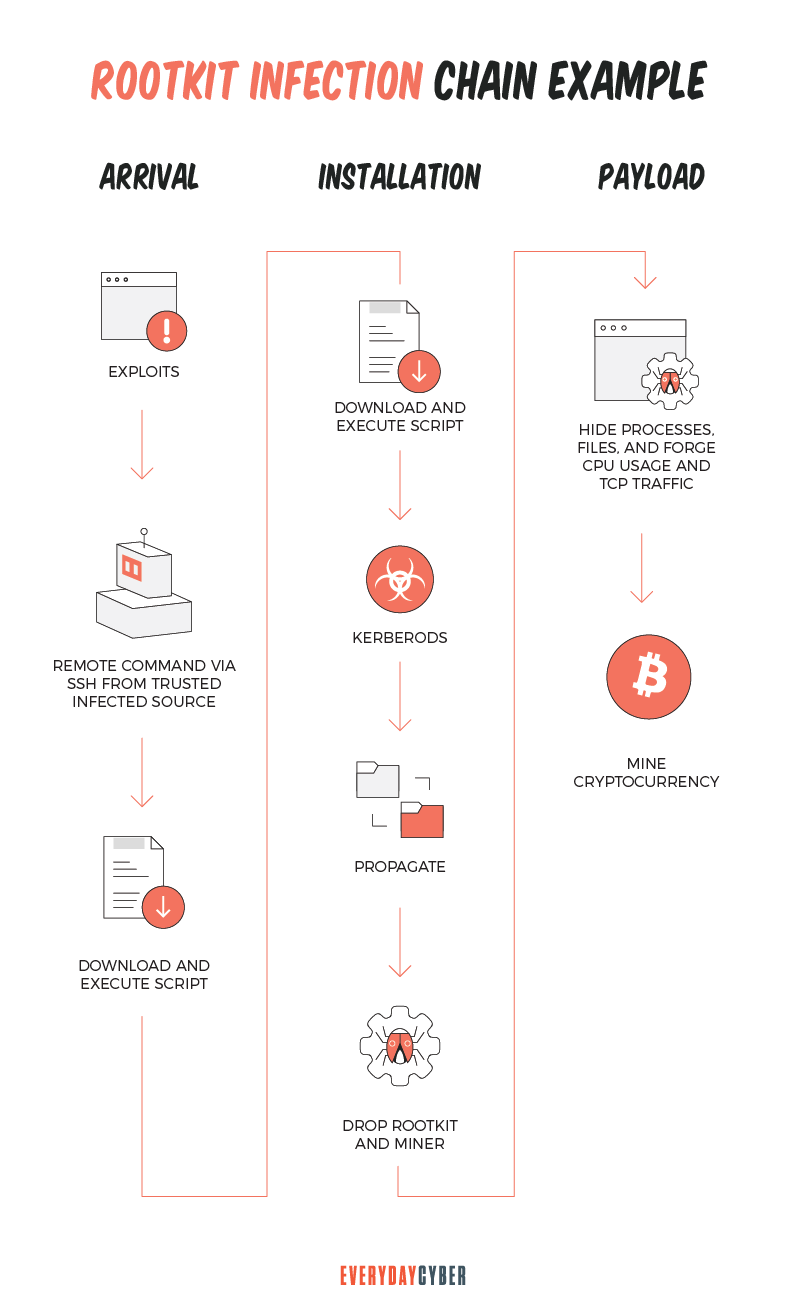
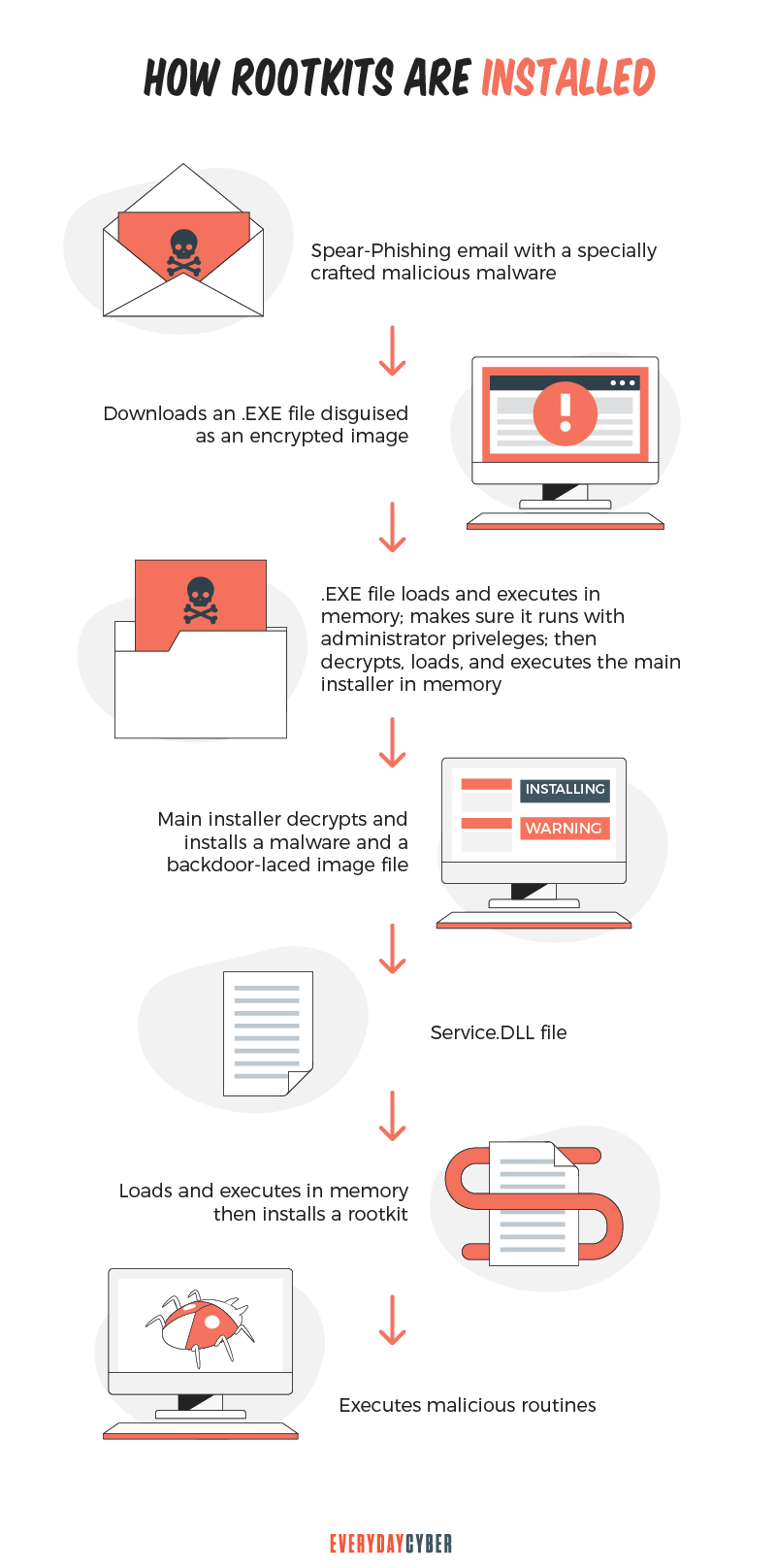
How are rootkits installed?
Rootkits cannot find their way through computer systems by themselves. They need help from other malware; typically referred to as droppers and loaders. Hackers bundle these three pieces to form a blended threat.
The dropper deposits the rootkit onto the victim’s computer. When the victim activates the dropper, the dropper in turn triggers the loader to go to work. The loader then installs the rootkit onto the target system. Loaders are often capable of penetrating inaccessible areas of a computer’s memory in order to install and activate the rootkit.
Installing the blended threat is a challenge for hackers. To accomplish this they may utilize several methods, such as:
- Taking control of messaging programs – Instant messaging traffic is a common target for hackers to spread the rootkit to even more victims. When a victim clicks on a malicious link in the message, the rootkit rolls out itself to the victim’s contacts as well.
- Hitching onto legit programs – Hackers can embed a rootkit into trusted apps and upload those infected apps to popular download portals. When you download any of those apps, you unwittingly install the rootkit into your computer, too.
- Leveraging other malware – Viruses, worms and Trojans easily find their way into computer systems. Cybercriminals use them to spread their rootkits.
- Stuffing them in rich content files – Rootkits can hide in PDFs, videos, infographics, live streams, podcasts and many other digital files.
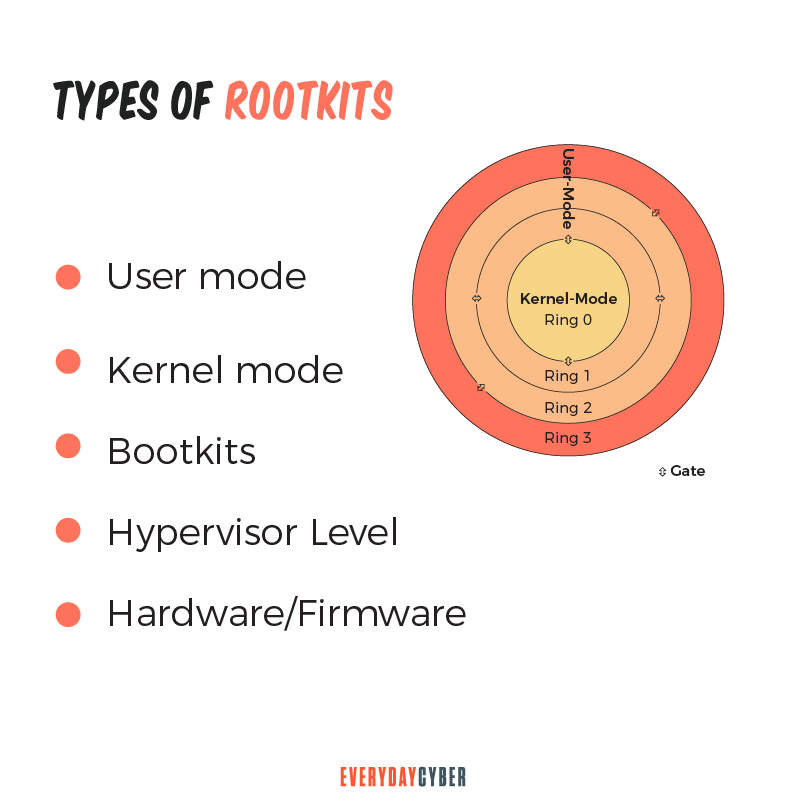
What are the basic types of rootkits?
Security experts categorize rootkits based on where and how deeply they infect devices. Here they are:
Hardware or firmware rootkit
This type of rootkit can infect the part of your computer that is external to the operating system. It can affect your computer’s hard drive or BIOS (Basic Input/Output System), the parts often responsible for booting up your system.
Firmware rootkits are notoriously hard to remove. Some rootkits can hide inside a piece of computer hardware while the computer is turned off. When you reopen the computer, the rootkit can reinstall itself and get back to work. If a rootkit scanner finds and deactivates the rootkit while the computer is running, the rootkit can bounce back to life when you turn on your computer again.
Bootkit or bootloader rootkit
When you turn on your computer, the bootloader loads your computer’s operating system. A bootkit can replace the legitimate bootloader and attack the operating system. For Windows 8 and Windows 10 operating systems, the Secure Boot feature blocks off bootloader rootkits.
Memory rootkit
Memory rootkits hide in the computer’s RAM, or Random Access Memory, where they carry out their harmful activities. These rootkits have a short lifespan and will disappear when you power off your computer but may reappear when you power back on.
User-mode rootkit
This rootkit impacts the operating system’s administrative function. It can gain top-level privileges needed to alter your system’s
Application rootkit
An application rootkit replaces or changes standard files and applications. The infected programs will still run normally which makes it all the more difficult to detect the rootkit.
Kernel-mode rootkit
A kernel-mode rootkit lives in your computer’s operating system and can compromise the whole OS. Once this rootkit hits, everything about your computer is potentially corrupted, including the accuracy of anti-rootkit scans. Fortunately, this rootkit is difficult to hide because it causes system crashes that reveal its presence.
Hybrid rootkit
A hybrid rootkit is a blend of the user-mode and kernel-mode rootkits. As such, it enjoys the stability of a user-mode rootkit and the stealth of a kernel-mode rootkit. This hybrid user-kernel rootkit is a preference of cybercriminals.
Virtual rootkit
A virtual rootkit is a virtual machine-based rootkit (VMBR) that runs beneath an existing operating system. After placing that OS onto a virtual machine, the virtual rootkit runs separately from the computer’s OS which makes it difficult for scanners to detect it.
How to detect rootkits
Rootkits are designed to stay hidden which makes detecting them a real challenge. This allows them to remain invisible while doing their dirty job. What are the possible signs of rootkit infection? Here are the common ones:
- Blue screen of death or BSOD – Also called stop error, exception error or blue screen error, a blue screen indicates that the Windows operating system has crashed. It means that the OS has reached a critical condition where it can no longer run safely. It may be caused by a malfunctioning hardware due to improper use or a firmware rootkit that got its way into the hard drive.
- Unusual web browser behavior – This can include web browser redirects, unrecognized bookmarks or link redirection.
- Dramatically slow device performance – Your device may take time starting, perform slowly, fail to respond to input by the keyboard or mouse, or freeze often.
- Windows settings change without authorization – You have not changed anything but the date and time displayed are incorrect, the task bar is hidden, or the screensaver has changed.
- Web pages are not functioning properly – There seems to be excessive network traffic, making web pages behave strangely.
How to prevent rootkits
Rootkits are as dangerous as viruses, but rootkits are more difficult to find. You can prevent rootkit attacks by following the same strategies you would implement against viruses and other forms of malware, such as:
- Using a comprehensive cyber
security solution - Updating your computer’s operating system and applications
- Watching out for phishing emails and never clicking on links attached to them
- Downloading files from trusted sources only
- Ignoring suspicious web browser pop ups
- Being vigilant about your web browser behavior
- Enabling the built-in kernel protection mode
- For companies, implementing the principle of least privilege
Rootkits are one of the most elusive types of malware. They can linger in hard drives and operating systems undetected and take their time wreaking havoc. Once the damage is done by a rootkit, you will need to totally rebuild your computer or network using original software. That is why prevention is often the best defense.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Computer Virus?
What's a computer virus? We hear about it all the time but do you really know what it is and how to prevent one?
How to protect yourself from identity theft
Identity fraud is all over. Almost every day, we see news reports describing new techniques for crooks to steal your personal information, as well as warnings about big data breaches that expose your sensitive data to hackers on the Dark Web.
What to do if your phone is lost or stolen
When your phone is lost or stolen, it is more than just a pricey handheld that is lost. Our phones keep track of our lives. If you’ve lost your phone, there are things you can do to track, locate, and recover it depending on the type of phone you have. Read this to get tips on how.
What is Spear Phishing?
Spear phishing is a targeted cyberattack to steal your information. You should be aware of the dangers of this and how to address them.
What is Spam?
Spam - spam emails, texts and sms messages (i.e. junk email), are unsolicited messages sent indiscriminately in bulk. Spam is a gigantic waste of time and resources.
7 ways to secure your home office
People working from home perform most of their tasks online. They are now more exposed to cyber attacks than ever before. Cyber criminals see a great opportunity in the massive growth in working from home and the vulnerabilities of home office security.