If you’re familiar with HTTPS, you’ll more likely want to know how it came about. An HTTPS that precedes the URL indicates that you have a secure connection. This is an important role of a certificate authority.
So what is a certificate authority?
A certificate authority, also known as a certification authority, is a reputable company that checks websites so they know who they’re interacting with over the Internet. Their goal is to make the Internet a safer place for both organizations and people. As such, they play an important role in digital
A certificate authority is responsible for issuing digital certificates. Before granting a certificate, a certificate authority thoroughly verifies the legitimacy of the company or individual applying for the certificate. This is likely the most crucial function of a certificate authority.
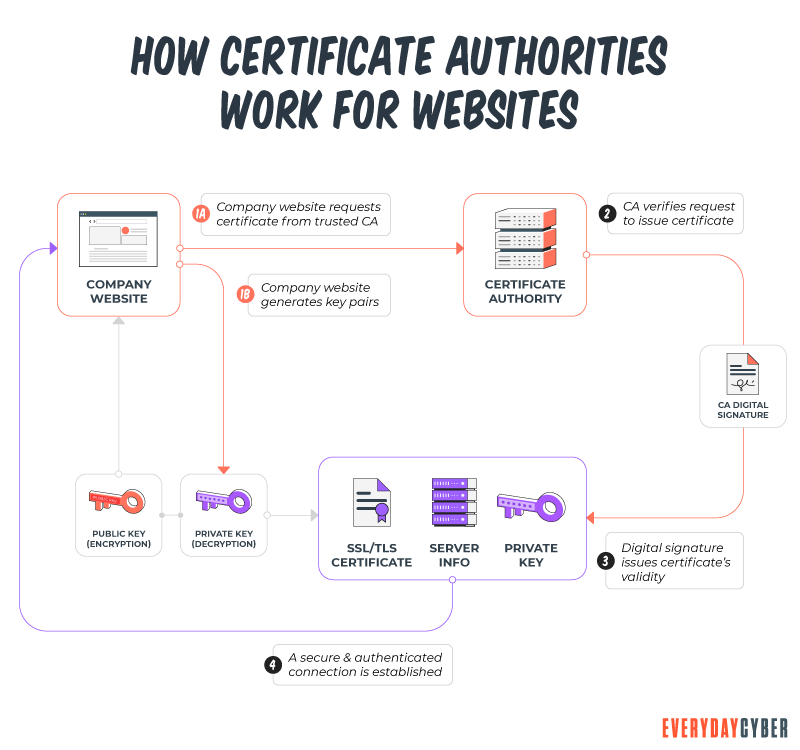
The CA grants a certificate to the website after verifying that all of the information is correct and meets the CA/B forum’s requirements. The web browser recognizes the website’s legitimacy by displaying HTTPS to indicate a secure connection to visitors. The website then displays many visual indicators, such as an address bar with the company name, a site seal, and a padlock, among others.
What are the types of certificate authorities?
Certificate authorities are the guardians of digital
A public certificate authority is an organization that issues digital certificates to individuals and organizations. Certificates issued by public certificate authorities are trusted because information is validated from the requester’s own records or from third party sources.
A private certificate authority is a local CA created by an organization for internal use only. The certificates are signed with the organization’s private key by the private root CA. Private certificate authorities are used to develop a private internal PKI network.
The certificates can be used to run devices and appliances within a business. They can also be used by users for VPNs, secure email, and by servers to encrypt data in databases.
How do you know you’re connected to the real website?
You can depend on a certificate authority to do this. It’s a certificate authority’s job to validate websites and organizations so you know with whom you’re communicating. This way, you won’t unwittingly give your credit card number to a hacker in a foreign country.
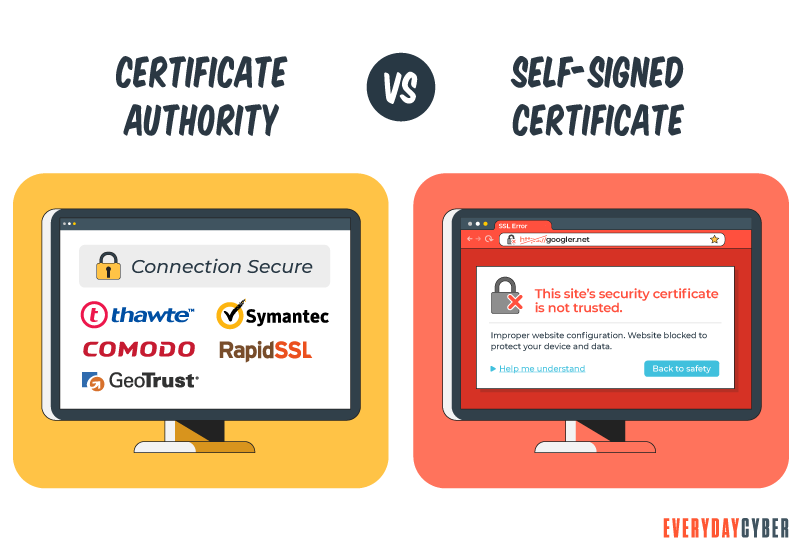
We can tell that the website has been confirmed by looking at the digital certificate details for the website. For example, if you want to check the authenticity of the EveryDayCyber website, it would look something like this:
How does my browser recognize a certificate authority?
Every CA has its own root certificate. All of the major browsers and operating systems share this root certificate. Root certificates are pre-installed in the root store of all browsers, operating systems, and devices.
Certificate authorities typically do not issue end-user certificates based on the primary root certificate. To issue end-entity certificates, they normally establish a number of intermediate certificates. This results in the creation of a certificate chain. Take a look at this simple illustration:
Browsers must always verify basic certificate information. The following steps show the sequence of checks that browsers perform:
1. The browser determines if the certificate is credible
Normal public key cryptography can be used to verify the signature on the certificate. If the signature is invalid, the certificate is deemed to have been altered after it was issued and is thus denied.
2. The browser checks if the certificate is authentic
The validity period of a certificate is the amount of time that the signing CA guarantees that it will keep track of its status. Any certificates with a validity term that ends before or starts after the date of the validation check are rejected by browsers.
3. The browser verifies if the certificate is revoked
When a certificate is granted, it is assumed that it will be used for the duration of its validity period. A certificate may become invalid before it naturally expires due to various factors.
It can happen that a subject’s name is changed. There are also instances when the private key is suspected of being compromised. In such instances, a certificate authority must revoke the relevant certificate. Users must also trust the certificate authority to tell browsers of the revocation status of their certificates.
4. The browser validates the issuer
Certificates are typically linked to two types of entities:
- The issuer owns the signing key
- The subject owns the public key that authenticates the certificate
Browsers check that the issuer field of a certificate matches the subject field of the certificate before it in the path. Most public key infrastructure (PKI) applications also check that the issuer’s key matches the key that signed the current certificate for enhanced
5. The browser processes constraints
A certificate authority has the power to set constraints or limitations on how each certificate is validated. Every certificate in the path can apply extra requirements that must be followed by all following certificates.
Certificate limitations are rarely a problem for the average Internet user. But they are frequent in enterprise SSL solutions. Functional constraints can be used for operational purposes, but their main role is to address recognized
The constraints include the following:
- Name constraints
- Policy constraints
- Key usage constraints
- Basic constraints, such as path length
6. The browser needs to continue processing all remaining important extensions
Browsers need to evaluate all remaining extensions that the current certificate deems critical before reaching a path’s leaf certificate. If it successfully reaches a path’s leaf certificate, the path is considered legitimate. If any issues occur, the path is flagged as invalid, and a secure connection is not made.
How does a certificate chain work?
When you visit a website, your browser inspects the SSL certificate and executes a brief process to verify the certificate’s validity. It checks the certificate’s validity dates, confirms the certificate hasn’t been revoked, and verifies the digital signature of the certificate.
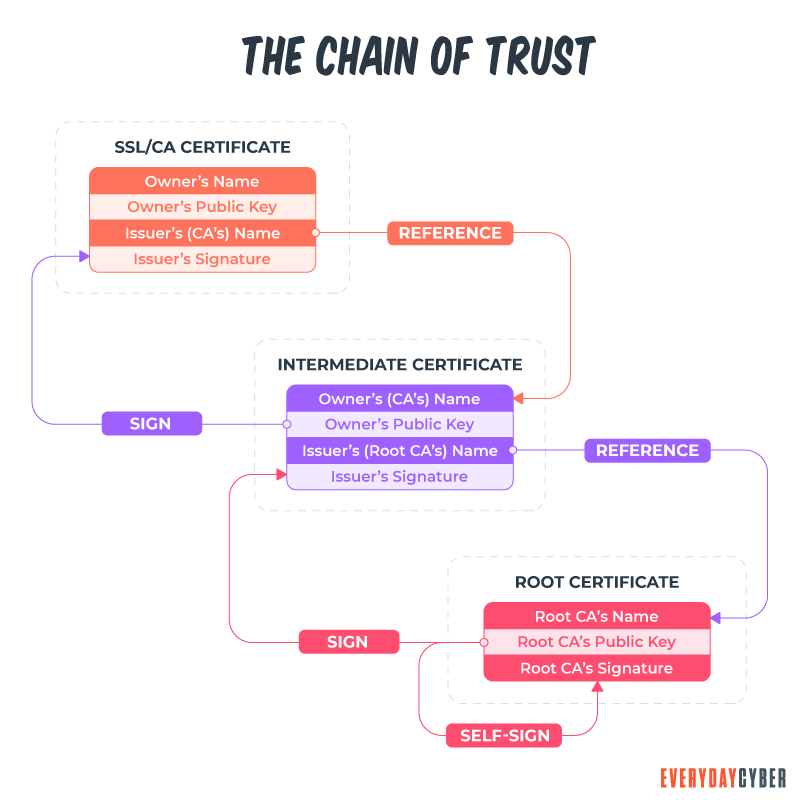
When your browser does this, it’s following the certificate chain. When you apply for a certificate, you must first create a certificate signing request (CSR) and a private key. In its most basic form, you transmit the CSR to the certificate authority. The certificate authority then issues your SSL certificate using its root’s private key and provides it back to you.
When a browser recognizes an SSL certificate, it knows that it was issued by one of the trusted roots or intermediate roots in the browser’s root store. It was signed with the root or intermediate root’s private key. The links from the root to the intermediate root to leaf (SSL) certificate constitute the certificate chain.
How do I get a CA certificate?
To get a digital certificate from a trusted certificate authority, you can contact the authority directly. Then follow the following steps:
1. Generate the certificate signing request (CSR).
2. After receiving the CSR, the CA will send you a private key in cryptographic form. Store both private key and CSR safely on your server or a local drive.
3. The certificate authority will require some validation:
- For domain validation (DV), the certificate authority only needs to validate domain ownership before issuing a digital certificate.
- For organization validation (OV) and extended validation (EV), the certificate authority needs to verify all the business-related information and documents before issuing a digital certificate.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
What does a certificate authority do?
A certificate authority plays a central role in a public key infrastructure. When an entity applies for a certificate, every process trickles down from the certificate authority.
Let’s break down the functions of certificate authorities:
Information gathering and verification
When a website requests a digital certificate from a certificate authority, the verification process begins. Depending on the type of certificate sought, the certificate authority starts verifying information about the certificate requester. The level of validation will depend on the certificate sought.
For domain validation (DV)
The certificate authority confirms that the requester is the legitimate owner of the domain or website in question. That’s all a certificate authority has to do. Domain validation is the bare minimum in terms of validation.
For organization validation (OV)
The certificate authority examines the legitimacy of the domain information. It goes further by conducting basic business validation. There is a human component to the OV process. To guarantee that the organization is legitimate, the certificate authority examines the information provided by the certificate requester. It also conducts its own investigation using third-party records and sources. OV has a higher validation level than DV.
For extended validation (EV)
This is the level of business validation that goes the furthest. The certificate authority examines the requester’s organization in depth during this one- to five-day validation phase. They go beyond the OV certification process’s criteria to guarantee that your company is real.
The certificate authority can provide greater assurance that the requester’s website is legitimate by requiring individuals and organizations to verify themselves.
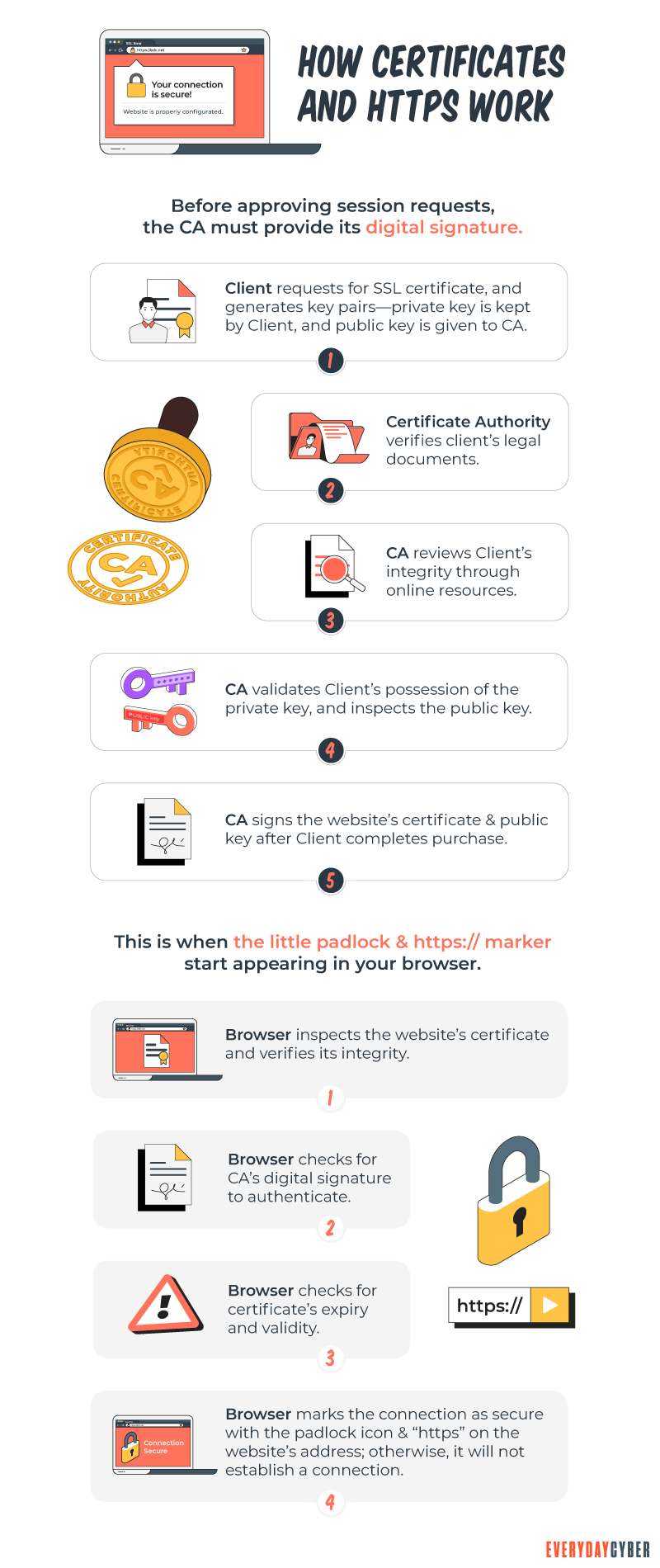
Issuance of digital certificates
Certificate authorities use certificate authentication to identify entities. This is what allows the website to gain your browser’s confidence.
Digital certificates are issued by certificate authorities in various formats. Within PKI, each has a distinct function. Within each category, there may be several types of digital certificates. These certificates are called X.509 digital certificates. An X.509 certificate is the standard that defines the format of PKI certificates as set by the International Telecommunications Union (ITU).
Certificate authorities may issue various types of digital certificates, such as:
- SSL/TLS certificates – single domain, multi-domain, wildcard, and multi-domain wildcard certificates
- Code signing certificates – Developers use these certificates to digitally sign their code to ensure its integrity.
- Email signing certificates – Individuals and organizations use these certificates to authenticate themselves to web servers.
- Document signing certificates – These certificates are used for authenticating the document creator and validating the document itself.
Put digital signatures on digital certificates
Certificate authorities apply digital signatures to the digital certificates. Why are digital signatures important?
Digital signatures prove that the digital certificates were issued by trusted certificate authorities. They also validate that the certificates are authentic and have not been modified.
But isn’t it possible to forge a digital signature? Digital signatures can’t be duplicated, forged, or altered because they are protected by hashing. Hashing uses an algorithm to map data of any size to a fixed length. It’s meant to verify that a file or piece of data hasn’t been altered and therefore is authentic. [8]
Certificate authorities can revoke digital certificates
The chain of trust is made up of a sequence of certifications that all go back to the issuing CA. This hierarchical trust model uses an intermediate certificate to connect the server certificate of the website to the root certificate. All public CAs use the following trust model:
- Root certificate – This digital certificate belongs to the issuing certificate authority. It’s stored in a trust store and is well-guarded by the CA.
- Intermediate certificate – A root certificate creates an intermediate certificate to protect it (the root) from threats. The intermediate acts as the go-between of the protected root certificate and leaf certificate.
- Server certificate – This certificate is issued to the applicant domain or entity.
When something goes wrong along the way, certificate authorities have an important role to do. When a digital certificate gets compromised, for example, a CA must revoke that certificate. The CA then adds it to the certificate revocation list (CRL) where clients can check for certificates that are no longer trustworthy.
Why do we need certificate authorities?
If you’re looking for a certificate for your company, here’s what a certification authority can help you with:
Validate your company’s identity
You may scream to the whole world that you are what you say you are. Some may believe you but most will likely not. A CA will help you spread your true
Prove that your company is legitimate
And that your website isn’t the playground of the bad guys. Hackers are cunning individuals who are constantly on the lookout for new ways to dupe consumers into revealing personal information. Without a digital certificate on your website, hackers can create a phony website that looks identical to your genuine one and pretend to be you.
CAs also help in establishing safe, encrypted connections between your web servers and the browsers of your users. You can use a TLS protocol to send and receive encrypted data by getting an SSL/TLS certificate for your website. This aids in securing data traveling to and from your servers. A TLS certificate protects against eavesdropping and man-in-the-middle attacks, which can lead to data theft.
Finally, CAs maintain certificate revocation lists. You can always go to them so you can stay away from dangerous websites.
Our final thoughts. There’s no doubt SSL certificates help protect your digital
Just remember to pick a thought leader and a CA partner that has and does it all. Pricing is a consideration but cheaper isn’t always better. It’s always better to consider:
- Industry standards
- Verification tools and practices
- Certificate management system
- Security system
- Local presence
You would never want to leave your business door wide open to intruders. You can depend on a trusted CA to guard that door for you.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is a Potentially Unwanted Program (PUP)?
PUPs refer to programs, applications and other software downloaded onto computers or mobile devices that may have an adverse impact on user privacy or security. The term “potentially unwanted program” was coined by McAfee to distinguish the program from malware.
What is AD tracking?
Digital and online ad tracking is the process of gathering data and insights about the performance of online advertising campaigns. Digital systems use methods like cookies, unique tracking URLs, tracking pixels, and other tools
What is Pharming?
Pharming is cybercriminals “slight of hand” cyber attack. Redirecting you to a fake website imitating a legitimate site so they can steal your login info, financial data, and more.
What is a Remote Access Trojan (RAT)?
A remote access Trojan is a software used by hackers to gain unauthorized access and remote control on a user’s computer or mobile device, including mouse and keyboard manipulation.
SMBs 7 Deadly Cybersecurity Sins
How many of these seven deadly cybersecurity sins are you guilty of? Build a resilient cybersecurity strategy before it’s too late.
What is Catfishing?
Catfishing is a deceptive technique individuals or criminal entities use to create a fictional personas or fake identities online and use them to scam unwitting victims.

