Rapid technology shifts bring new risks. Small businesses experience cyber
A cybersecurity risk assessment is not a top priority for many small business owners. Some claim it’s too complicated, time-consuming, and expensive. Others allege it’s just for compliance or show. Still, many others feel they are not prime targets of cyberattacks.
Numbers don’t lie
Cyber
Fundera, a subsidiary of NerdWallet and financial resource to small businesses, has put together shocking figures that should open your eyes to the dire state of cyber
- Small business cyber breaches increased by 424% in 2020 or five times compared to the previous year
- 60% of small businesses that are victims of cyber attacks go out of business within six months
- 43% of cyber attacks target small businesses
- 54% of small businesses believe they’re too small for a cyberattack
- 65% of small businesses didn’t know what to do following a cybersecurity attack
- 63% of reported data breaches happened due to weak, stolen, or default passwords
- 66% of small businesses are worried or extremely worried about cybersecurity risk
- 94% of detected malware in small businesses came through email
- 65% of small businesses failed to rectify their cybersecurity system after an attack
- Projections show cyber attacks will cost $6 trillion in 2021
If you’re scared of the numbers, so are we. These figures show the sad reality of the cybersecurity landscape, but it’s not hopeless. A purposeful cyber
What is cybersecurity risk assessment?
A cyber
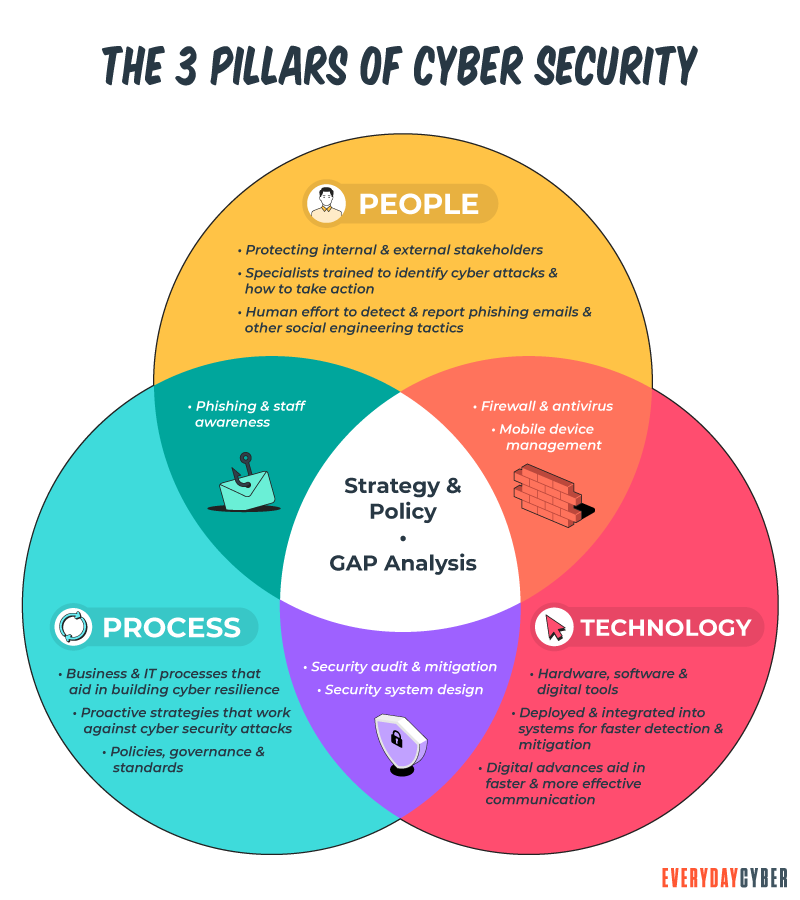
Assessing the risks includes a careful analysis of all potential threats, vulnerabilities, and vectors in the IT system on an ongoing basis, not a one-off affair. IT experts recommend an assessment every two years and more often as new threats develop. The idea here is to thwart new risks that come with emerging technologies.
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Why small businesses need to conduct a cybersecurity risk assessment
Conducting a proper cybersecurity risk assessment isn’t inexpensive and can take time. But the money and time you invest are worth it if only to save your business from future cyber threats.

How do small businesses benefit from a cyber
Increased awareness of cyber threat preparedness
Awareness of cyber threats lets you know what to do to avert those threats. But, as some people would say, it’s always better to be on the side of caution than to be sorry when it’s too late. In short, a cyber
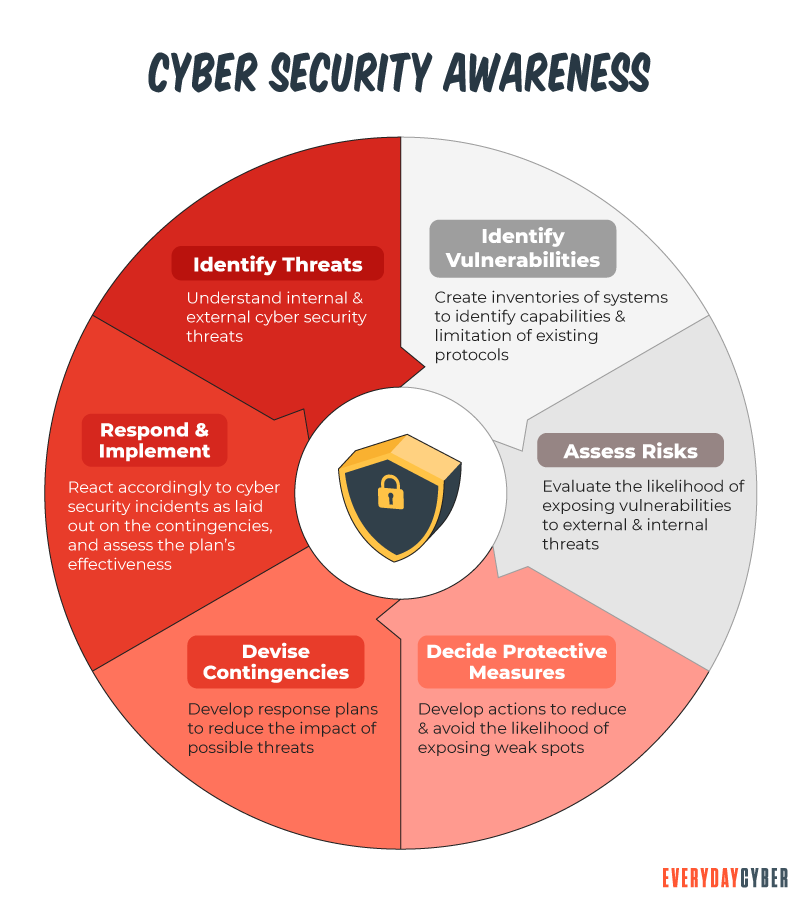
In a worst-case scenario, your first lines of defense fail, and you fall victim to some kind of cyber
Discovery of hidden threats
You can’t fight an enemy you can’t see. Cyber
Mitigation of future risks
Conducting a cybersecurity risk assessment will help your business mitigate future hacks and breaches. Being prepared will save time, money, and resources for your company.
Existing assessments can serve as templates for future assessments. Consider Cyber
It helps business leaders make more informed decisions
A cyber
It eliminates the need to review misleading threats based on non-quantifiable data or misinformation.
Components of a cyber security risk assessment
More comprehensive cyber
For small businesses, they can tailor their cybersecurity risk assessment program according to their needs based on the following common elements of a risk assessment:
1. Company risk profile
To understand what threats are worth assessing, you need to develop a profile of your business type, operations, and priorities. For example, a financial company will have different
2. Technology assessment
Technology resources include both hardware and software. They make up the core digital infrastructure of most small businesses. Sadly, many SMBs can’t bankroll a comprehensive cyber
Whether you decide on an in-house team or an outsourced partner, you should sit down with them and ask the following questions:
Are all devices and software properly configured and regularly updated? Unfortunately, not all devices and software are perfect. However, responsible vendors monitor products they roll out and implement updates to patch vulnerabilities that bad actors can exploit through zero-day attacks. Zero-day exploits are malicious attempts by hackers to exploit vulnerabilities that the vendor has not identified. New product or version rollouts are particularly vulnerable.
Are all
Is your Intrusion Detection System (IDS) deployed across your network? An IDS has the crucial role of acting as the last line of defense when all the first lines fail. For example, an attacker may successfully gain an admin password through phishing. His next attempt would be to access a secure server from an unrecognized IP address. If your IDS is working, it should be able to detect this next move and thwart the attack.
Are all incoming and outgoing information traffic secured? This traffic includes all information coming in and out through emails, websites, and virtual private networks (VPNs). Since most malware comes through emails, securing emails with encryption and spam filters is the best way to block malicious attempts. A centralized spam filter helps sift poisoned communication before they reach employee mailboxes.
Do you implement a layered approach to cybersecurity? A segmented
- Network perimeter
security - Endpoint
security - Authentication protocols
- Real-time monitoring
- Backup and disaster recovery
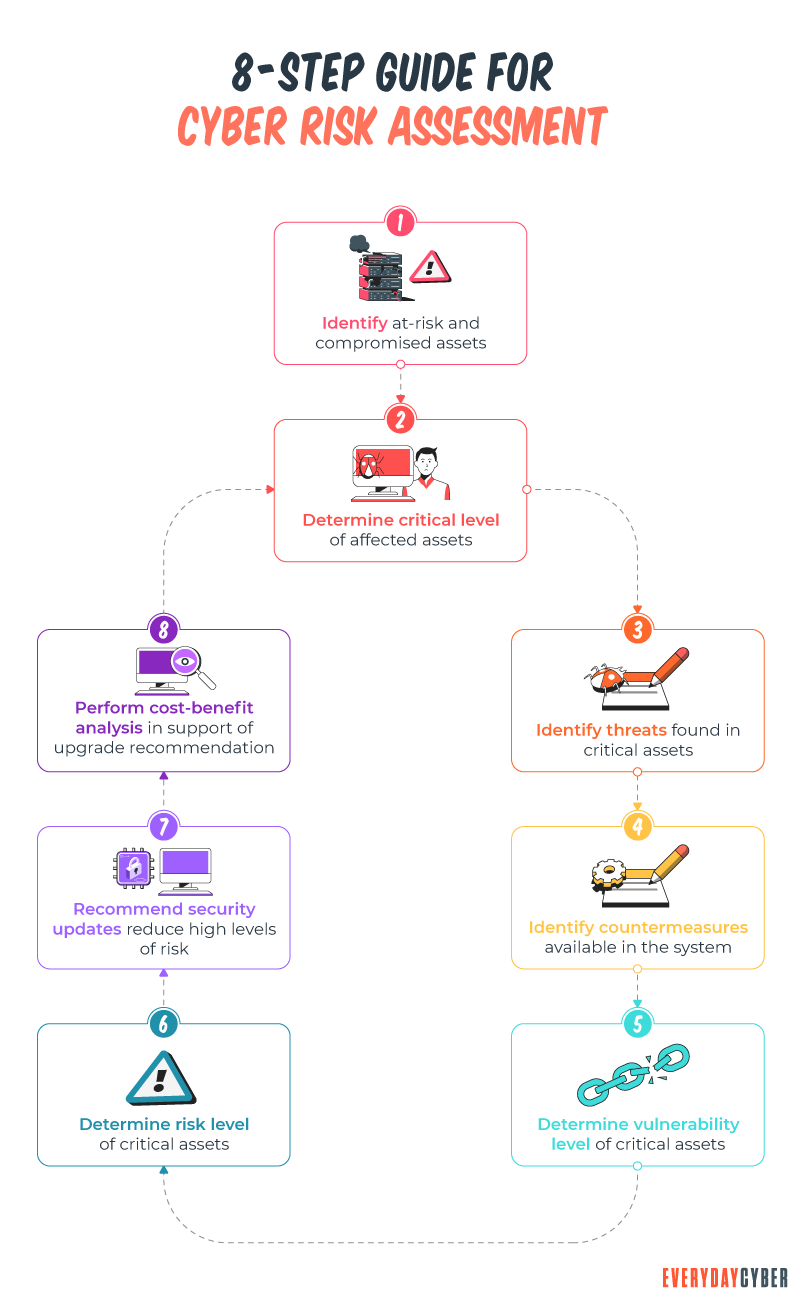
3. Governance practices assessment
Governance practices include guidelines, procedures, and other acts performed to implement policies by the organization. Your assessment should include:
Access control practices. Limit physical, administrative, and remote access to only people who need them in doing their jobs.
Implement policies that ban weak passwords, restrict password sharing, prevent access from unsecured networks like public Wi-Fi and prohibit the use of unauthorized devices to access work.
Supply chain endpoint management. Small businesses normally do business with outside vendors and third-party partners for products and services they need to operate their businesses. They use mobile devices, computers, laptops, tablets, and other networked devices in the process. These endpoints are potential vulnerability points. Your risk assessment should consider a provision for endpoint
Bring your own device (BYOD) assessment. BYOD is commonplace in many small businesses. However, devices owned by employees and not managed by the company are more likely to be infected with malware. Connecting employee devices to company networks makes it easier for malware to hop to secure corporate servers and other company endpoints.
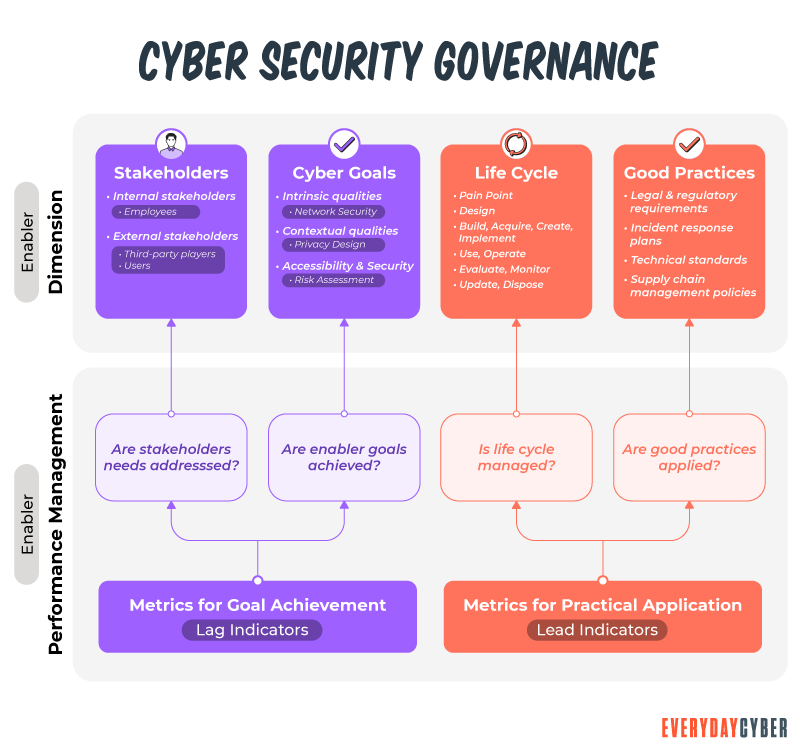
Implement BYOD security management practices just like you do for supply chain endpoints to mitigate this risk.
4. Assessment of people
The enemy from within is often more dangerous than a hacker from outside. They can do it on purpose or by mistake. Employees have access to systems and know their way around the network. A thorough assessment of your people should include the following:
Implementation of incident reporting. Every employee should be encouraged or even obligated to report perceived anomalous practices of people or abnormal behavior of equipment. Not all employees can identify viruses, but they can report unauthorized access, use of unsecured BYOD, password sharing, and other restricted activities.
Full-scale end user and cyber
Experience is one of the best teachers. Try running a phishing vulnerability test using an online phishing simulator. You can send phishing emails to email inboxes anonymously and see how your employees respond. The results will help you measure your employees’ level of awareness of cybersecurity threat attempts and implement better practices to avoid such attacks.
Our final thoughts. Protecting your small business’ network is paramount for business continuity, or at least survival in the increasingly chaotic cyberspace. Your company data and, by extension, your customers’ data are highly valuable.
Cybersecurity risk assessments do more than just identify and analyze threats. They help small businesses proactively counteract threats before compromising their IT
It’s a good first step to do your own cyber
By entering your email address you agree to receive emails from EveryDayCyber. We'll respect your privacy and you can unsubscribe at any time.
Recommended Reading
What is Malware?
Malware or “malicious software” is a cybersecurity term used to describe software that steals your data, spies on you, damages your devices, and generally causes chaos and destruction.
What is Business Email Compromise (BEC)
Business email compromise is one of the most financially destructive cyber crimes. These are emails that appear to be sent by known or trusted sources asking for something legitimate.
What is Pharming?
Pharming is cybercriminals “slight of hand” cyber attack. Redirecting you to a fake website imitating a legitimate site so they can steal your login info, financial data, and more.
Element Chat Review: How Secure Is It, Really?
Element is a secure messaging app for safer personal and corporate communication and other group chats.
5 Biggest Cybersecurity Mistake SMBs do
Small and midsize companies can’t afford to learn cybersecurity haphazardly while cyberattacks are steadily rising. If you’re a decision-maker, you can’t ignore the 424% increase in cyber breaches in 2021.
What is a Firewall?
A firewall blocks outsiders from gaining unauthorized access to your computer and helps stop malicious software from infecting your computer.


